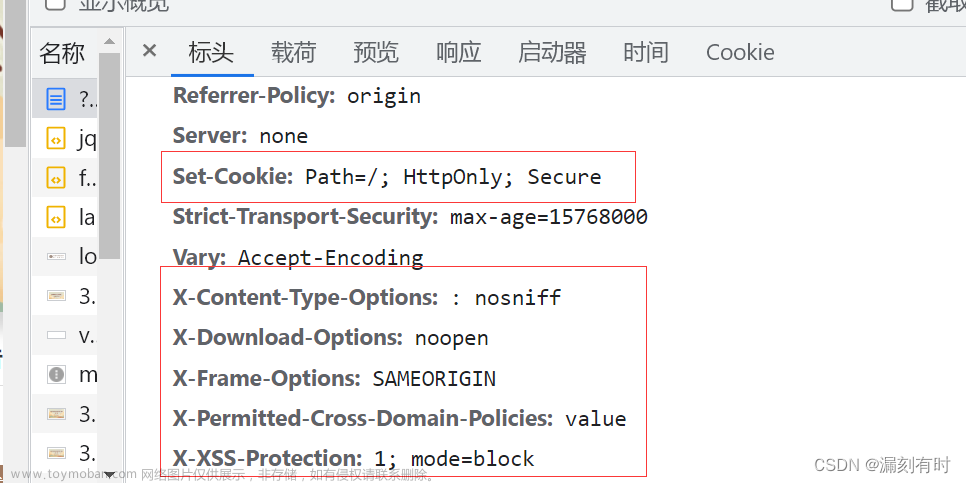
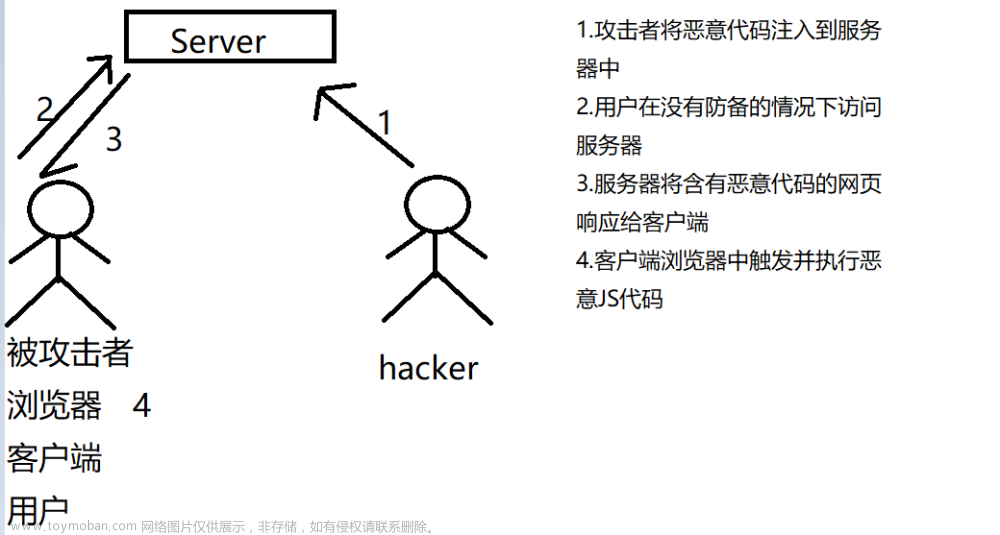
收到检查报告,说是有xss 存储型漏洞,百度看了很多资料总结两句话
1、保存数据库内容需要过滤
2、设置过滤器
思路:我们需要一个过滤前在Controller方法调用前对所有参数进行检查,过滤替换。
过滤》替换非法参数》继续Controller调用。
网上得思路基本是替换,没看到拒绝请求,因为过滤得检查很多很容易被拒绝非常不友好
做法spring拦截器:检查非法内容或特定内容拒绝请求,使用sprintboot得做法很简单,做一个aop切面定义一个定义一个拦截器
<mvc:interceptor>
<mvc:mapping path="/**"/>
<bean class="com.iwater.ishuidi.interceptor.EncodingInterceptor"/>
</mvc:interceptor>import javax.servlet.http.HttpServletRequest;
import javax.servlet.http.HttpServletResponse;
import org.springframework.web.servlet.HandlerInterceptor;
import org.springframework.web.servlet.ModelAndView;
/**
* 字符集拦截器
*
* @author victor
*
*/
public class EncodingInterceptor implements HandlerInterceptor
{
/**
* 在controller后拦截
*/
public void afterCompletion(HttpServletRequest request, HttpServletResponse response, Object object,
Exception exception)
throws Exception
{
}
public void postHandle(HttpServletRequest request, HttpServletResponse response, Object object,
ModelAndView modelAndView)
throws Exception
{
}
/**
* 在controller前拦截
*/
public boolean preHandle(HttpServletRequest request, HttpServletResponse response, Object object)
throws Exception
{
这里检查判断,非法返回false、正常返回true继续
return true;
}
}方法2过滤器过滤非法内容,三步处理:
步骤一、定义XssRequestWrappers类用来过滤请求非法内容
import java.util.HashMap;
import java.util.Iterator;
import java.util.Map;
import java.util.Set;
import java.util.regex.Pattern;
import javax.servlet.http.HttpServletRequest;
import javax.servlet.http.HttpServletRequestWrapper;
import org.springframework.util.StringUtils;
import org.springframework.web.multipart.MultipartHttpServletRequest;
import org.springframework.web.multipart.commons.CommonsMultipartResolver;
public class XssRequestWrappers extends HttpServletRequestWrapper {
private CommonsMultipartResolver multiparResolver = new CommonsMultipartResolver();
public XssRequestWrappers(HttpServletRequest request) {
super(request);
String type = request.getHeader("Content-Type");
if (!StringUtils.isEmpty(type) && type.contains("multipart/form-data")) {
MultipartHttpServletRequest multipartHttpServletRequest = multiparResolver.resolveMultipart(request);
Map<String, String[]> stringMap = multipartHttpServletRequest.getParameterMap();
if (!stringMap.isEmpty()) {
for (String key : stringMap.keySet()) {
String value = multipartHttpServletRequest.getParameter(key);
striptXSS(key);
striptXSS(value);
}
}
super.setRequest(multipartHttpServletRequest);
}
}
@Override
public String[] getParameterValues(String parameter) {
String[] values = super.getParameterValues(parameter);
if (values == null) {
return null;
}
int count = values.length;
String[] encodedValues = new String[count];
for (int i = 0; i < count; i++) {
encodedValues[i] = striptXSS(values[i]);
}
return encodedValues;
}
@Override
public String getParameter(String parameter) {
String value = super.getParameter(parameter);
return striptXSS(value);
}
@Override
public String getHeader(String name) {
String value = super.getHeader(name);
return striptXSS(value);
}
@Override
public Map<String, String[]> getParameterMap() {
Map<String, String[]> map1 = super.getParameterMap();
Map<String, String[]> escapseMap = new HashMap<String, String[]>();
Set<String> keys = map1.keySet();
for (String key : keys) {
String[] valArr = map1.get(key);
if (valArr != null && valArr.length > 0) {
String[] escapseValArr = new String[valArr.length];
for (int i = 0; i < valArr.length; i++) {
String escapseVal = striptXSS(valArr[i]);
escapseValArr[i] = escapseVal;
}
escapseMap.put(key, escapseValArr);
}
}
return escapseMap;
}
public static String striptXSS(String value) {
if (value != null) {
value = value.replaceAll("", "");
Pattern scriptPattern = Pattern.compile("<script>(.*?)</script>", Pattern.CASE_INSENSITIVE);
value = scriptPattern.matcher(value).replaceAll("");
scriptPattern = Pattern.compile("src[\r\n]*=[\r\n]*\\\'(.*?)\\\'", Pattern.CASE_INSENSITIVE | Pattern.MULTILINE | Pattern.DOTALL);
value = scriptPattern.matcher(value).replaceAll("");
scriptPattern = Pattern.compile("src[\r\n]*=[\r\n]*\\\"(.*?)\\\"", Pattern.CASE_INSENSITIVE | Pattern.MULTILINE | Pattern.DOTALL);
value = scriptPattern.matcher(value).replaceAll("");
scriptPattern = Pattern.compile("</script>", Pattern.CASE_INSENSITIVE);
value = scriptPattern.matcher(value).replaceAll("");
scriptPattern = Pattern.compile("<script(.*?)>", Pattern.CASE_INSENSITIVE | Pattern.MULTILINE | Pattern.DOTALL);
value = scriptPattern.matcher(value).replaceAll("");
scriptPattern = Pattern.compile("eval\\((.*?)\\)", Pattern.CASE_INSENSITIVE | Pattern.MULTILINE | Pattern.DOTALL);
value = scriptPattern.matcher(value).replaceAll("");
scriptPattern = Pattern.compile("expression\\((.*?)\\)", Pattern.CASE_INSENSITIVE | Pattern.MULTILINE | Pattern.DOTALL);
value = scriptPattern.matcher(value).replaceAll("");
scriptPattern = Pattern.compile("javascript:", Pattern.CASE_INSENSITIVE);
value = scriptPattern.matcher(value).replaceAll("");
scriptPattern = Pattern.compile("vbscript:", Pattern.CASE_INSENSITIVE);
value = scriptPattern.matcher(value).replaceAll("");
scriptPattern = Pattern.compile("onload(.*?)=", Pattern.CASE_INSENSITIVE | Pattern.MULTILINE | Pattern.DOTALL);
value = scriptPattern.matcher(value).replaceAll("");
scriptPattern = Pattern.compile(".*<.*", Pattern.CASE_INSENSITIVE );
value = scriptPattern.matcher(value).replaceAll("");
}
return value;
}
}步骤二、定义过滤器监听XSSFilter 重写Filter
import java.io.IOException;
import javax.servlet.Filter;
import javax.servlet.FilterChain;
import javax.servlet.FilterConfig;
import javax.servlet.ServletException;
import javax.servlet.ServletRequest;
import javax.servlet.ServletResponse;
import javax.servlet.http.HttpServletRequest;
public class XSSFilter implements Filter {
@Override
public void init(FilterConfig arg0) throws ServletException {
}
@Override
public void destroy() {
}
@Override
public void doFilter(ServletRequest request, ServletResponse response, FilterChain chain)
throws IOException, ServletException {
chain.doFilter(new XssRequestWrappers((HttpServletRequest) request), response);
}
}步骤三、配置web.xml 用于监听
<!-- 解决xss漏洞 -->
<filter>
<filter-name>xssFilter</filter-name>
<filter-class>com.iwater.ishuidi.interceptor.XSSFilter</filter-class>
</filter>
<!-- 解决xss漏洞 -->
<filter-mapping>
<filter-name>xssFilter</filter-name>
<url-pattern>/*</url-pattern>
<dispatcher>REQUEST</dispatcher>
</filter-mapping>以上三步完成启动测试,输入测试内容postman测试接口对非法字符得过滤结果文章来源:https://www.toymoban.com/news/detail-458544.html
输出接口拿到得参数,看看非法参数是否没了文章来源地址https://www.toymoban.com/news/detail-458544.html
到了这里,关于XSS 存储漏洞修复的文章就介绍完了。如果您还想了解更多内容,请在右上角搜索TOY模板网以前的文章或继续浏览下面的相关文章,希望大家以后多多支持TOY模板网!