由于之前的实验很多同学提出了问题,确实是我排版不当导致,我重新梳理规划,发给大家。
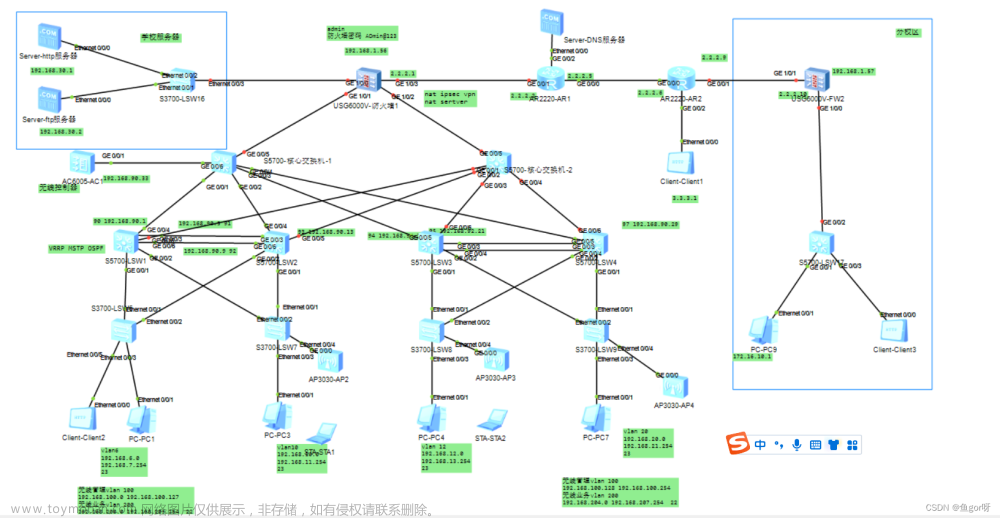
本次论文实验是园区多出口带宽资源调配和管理,大家可以参考组网结构,在此基础上可以进行各种改良,符合自己的实验需求是最终目的,下面直接上配置,想要定制的+绿泡泡18812668402
技术范围
接入层:MSTP 边缘端口
汇聚层:MSTP VRRP DHCP全局 OSPF 静态路由
核心层:OSPF QOS(MQC)
防火墙:OSPF HRP IP-LINK 策略路由 安全策略 NAT策略
---------------------------------------------------------------------------------------------------------------------------------
接入层交换机
sysname jindelou
#
vlan batch 10 to 11
#
stp region-configuration
region-name huawei
instance 1 vlan 10 to 12
instance 2 vlan 13 to 15
active region-configuration
#
interface Ethernet0/0/1
port link-type access
port default vlan 10
stp edged-port enable
#
interface Ethernet0/0/2
port link-type access
port default vlan 11
stp edged-port enable
#
interface GigabitEthernet0/0/1
port link-type trunk
port trunk allow-pass vlan 10 11
#
interface GigabitEthernet0/0/2
port link-type trunk
port trunk allow-pass vlan 10 11
----------------------------------------------------------
sysname baiyanglou
#
vlan batch 14 to 15
#
stp region-configuration
region-name huawei
instance 1 vlan 10 to 12
instance 2 vlan 13 to 15
active region-configuration
#
interface Ethernet0/0/1
port link-type access
port default vlan 14
stp edged-port enable
#
interface Ethernet0/0/2
port link-type access
port default vlan 15
stp edged-port enable
#
interface GigabitEthernet0/0/1
port link-type trunk
port trunk allow-pass vlan 14 15
#
interface GigabitEthernet0/0/2
port link-type trunk
port trunk allow-pass vlan 14 15
-------------------------------------------------------
sysname wenshilou
#
vlan batch 12 to 13
#
stp region-configuration
region-name huawei
instance 1 vlan 10 to 12
instance 2 vlan 13 to 15
active region-configuration
#
interface Ethernet0/0/1
port link-type access
port default vlan 12
stp edged-port enable
#
interface Ethernet0/0/2
port link-type access
port default vlan 13
stp edged-port enable
#
interface GigabitEthernet0/0/1
port link-type trunk
port trunk allow-pass vlan 12 13
#
interface GigabitEthernet0/0/2
port link-type trunk
port trunk allow-pass vlan 12 13
---------------------------------------------------------------------------------------------------------------------------------
汇聚层交换机
sysname WS-SW1
#
vlan batch 10 to 15 100 to 101
#
stp instance 1 root primary
stp instance 2 root secondary
#
dhcp enable
#
stp region-configuration
region-name huawei
instance 1 vlan 10 to 12
instance 2 vlan 13 to 15
active region-configuration
#
ip pool vlan10
gateway-list 192.168.10.254
network 192.168.10.0 mask 255.255.255.0
#
ip pool vlan11
gateway-list 192.168.11.254
network 192.168.11.0 mask 255.255.255.0
#
ip pool vlan12
gateway-list 192.168.12.254
network 192.168.12.0 mask 255.255.255.0
#
ip pool vlan13
gateway-list 192.168.13.254
network 192.168.13.0 mask 255.255.255.0
#
ip pool vlan14
gateway-list 192.168.14.254
network 192.168.14.0 mask 255.255.255.0
#
ip pool vlan15
gateway-list 192.168.15.254
network 192.168.15.0 mask 255.255.255.0
#
interface Vlanif10
ip address 192.168.10.252 255.255.255.0
vrrp vrid 10 virtual-ip 192.168.10.254
vrrp vrid 10 priority 120
vrrp vrid 10 preempt-mode timer delay 42
vrrp vrid 10 track interface GigabitEthernet0/0/1 reduced 30
dhcp select global
#
interface Vlanif11
ip address 192.168.11.252 255.255.255.0
vrrp vrid 11 virtual-ip 192.168.11.254
vrrp vrid 11 priority 120
vrrp vrid 11 preempt-mode timer delay 42
vrrp vrid 11 track interface GigabitEthernet0/0/1 reduced 30
dhcp select global
#
interface Vlanif12
ip address 192.168.12.252 255.255.255.0
vrrp vrid 12 virtual-ip 192.168.12.254
vrrp vrid 12 priority 120
vrrp vrid 12 preempt-mode timer delay 42
vrrp vrid 12 track interface GigabitEthernet0/0/1 reduced 30
dhcp select global
#
interface Vlanif13
ip address 192.168.13.252 255.255.255.0
vrrp vrid 13 virtual-ip 192.168.13.254
dhcp select global
#
interface Vlanif14
ip address 192.168.14.252 255.255.255.0
vrrp vrid 14 virtual-ip 192.168.14.254
dhcp select global
#
interface Vlanif15
ip address 192.168.15.252 255.255.255.0
vrrp vrid 15 virtual-ip 192.168.15.254
dhcp select global
#
interface Vlanif100
ip address 10.1.10.1 255.255.255.252
#
interface Vlanif101
ip address 10.1.10.9 255.255.255.252
#
interface Eth-Trunk1
port link-type trunk
port trunk allow-pass vlan 10 to 15 101
mode lacp-static
#
interface GigabitEthernet0/0/1
port link-type access
port default vlan 100
#
interface GigabitEthernet0/0/2
port link-type trunk
port trunk allow-pass vlan 10 to 11
#
interface GigabitEthernet0/0/3
port link-type trunk
port trunk allow-pass vlan 12 to 13
#
interface GigabitEthernet0/0/4
port link-type trunk
port trunk allow-pass vlan 14 to 15
#
interface GigabitEthernet0/0/5
eth-trunk 1
#
interface GigabitEthernet0/0/6
eth-trunk 1
#
ospf 1 router-id 1.1.1.1
area 0.0.0.0
authentication-mode md5 1 cipher #vCJKvae/8uqcXT}k'OIe_n#
network 10.1.10.0 0.0.0.3
network 10.1.10.8 0.0.0.3
area 0.0.0.1
network 192.168.10.0 0.0.0.255
network 192.168.11.0 0.0.0.255
network 192.168.12.0 0.0.0.255
network 192.168.13.0 0.0.0.255
network 192.168.14.0 0.0.0.255
network 192.168.15.0 0.0.0.255
-----------------------------------------------------------------------
sysname WS-SW2
#
vlan batch 10 to 15 100 to 101
#
stp instance 1 root secondary
stp instance 2 root primary
#
stp region-configuration
region-name huawei
instance 1 vlan 10 to 12
instance 2 vlan 13 to 15
active region-configuration
#
ip pool vlan10
gateway-list 192.168.10.254
network 192.168.10.0 mask 255.255.255.0
#
ip pool vlan11
gateway-list 192.168.11.254
network 192.168.11.0 mask 255.255.255.0
#
ip pool vlan12
gateway-list 192.168.12.254
network 192.168.12.0 mask 255.255.255.0
#
ip pool vlan13
gateway-list 192.168.13.254
network 192.168.13.0 mask 255.255.255.0
#
ip pool vlan14
gateway-list 192.168.14.254
network 192.168.14.0 mask 255.255.255.0
#
ip pool vlan15
gateway-list 192.168.15.254
network 192.168.15.0 mask 255.255.255.0
#
interface Vlanif10
ip address 192.168.10.253 255.255.255.0
vrrp vrid 10 virtual-ip 192.168.10.254
dhcp select global
#
interface Vlanif11
ip address 192.168.11.253 255.255.255.0
vrrp vrid 11 virtual-ip 192.168.11.254
dhcp select global
#
interface Vlanif12
ip address 192.168.12.253 255.255.255.0
vrrp vrid 12 virtual-ip 192.168.12.254
dhcp select global
#
interface Vlanif13
ip address 192.168.13.251 255.255.255.0
vrrp vrid 13 virtual-ip 192.168.13.254
vrrp vrid 13 priority 120
vrrp vrid 13 preempt-mode timer delay 42
vrrp vrid 13 track interface GigabitEthernet0/0/1 reduced 30
dhcp select global
#
interface Vlanif14
ip address 192.168.14.251 255.255.255.0
vrrp vrid 14 virtual-ip 192.168.14.254
vrrp vrid 14 priority 120
vrrp vrid 14 preempt-mode timer delay 42
vrrp vrid 14 track interface GigabitEthernet0/0/1 reduced 30
dhcp select global
#
interface Vlanif15
ip address 192.168.15.251 255.255.255.0
vrrp vrid 15 virtual-ip 192.168.15.254
vrrp vrid 15 priority 120
vrrp vrid 15 preempt-mode timer delay 42
vrrp vrid 15 track interface GigabitEthernet0/0/1 reduced 30
dhcp select global
#
interface Vlanif100
ip address 10.1.10.5 255.255.255.252
#
interface Vlanif101
ip address 10.1.10.10 255.255.255.252
#
interface Eth-Trunk1
port link-type trunk
port trunk allow-pass vlan 10 to 15 101
mode lacp-static
#
interface GigabitEthernet0/0/1
port link-type access
port default vlan 100
#
interface GigabitEthernet0/0/2
port link-type trunk
port trunk allow-pass vlan 10 to 11
#
interface GigabitEthernet0/0/3
port link-type trunk
port trunk allow-pass vlan 12 to 13
#
interface GigabitEthernet0/0/4
port link-type trunk
port trunk allow-pass vlan 14 to 15
#
interface GigabitEthernet0/0/5
eth-trunk 1
#
interface GigabitEthernet0/0/6
eth-trunk 1
#
ospf 1 router-id 2.2.2.2
area 0.0.0.0
authentication-mode md5 1 cipher ~7oISC6o';EBi%T]n/.IQ_%#
network 10.1.10.8 0.0.0.3
network 10.1.10.4 0.0.0.3
area 0.0.0.1
network 192.168.10.0 0.0.0.255
network 192.168.11.0 0.0.0.255
network 192.168.12.0 0.0.0.255
network 192.168.13.0 0.0.0.255
network 192.168.14.0 0.0.0.255
network 192.168.15.0 0.0.0.255
---------------------------------------------------------------------------------------------------------------------------------
核心层路由器
sysname R1
acl number 2000
rule 5 permit source 192.168.10.0 0.0.0.255
rule 10 permit source 192.168.11.0 0.0.0.255
acl number 2001
rule 5 permit source 192.168.12.0 0.0.0.255
rule 10 permit source 192.168.13.0 0.0.0.255
acl number 2002
rule 5 permit source 192.168.14.0 0.0.0.255
rule 10 permit source 192.168.15.0 0.0.0.255
#
traffic classifier class3 operator or
if-match acl 2002
traffic classifier class2 operator or
if-match acl 2001
traffic classifier class1 operator or
if-match acl 2000
#
traffic behavior behavior1
car cir 200000 cbs 37600000 pbs 62600000 green pass yellow pass red discard
traffic behavior behavior2
car cir 100000 cbs 18800000 pbs 31300000 green pass yellow pass red discard
traffic behavior behavior3
car cir 50000 cbs 9400000 pbs 15650000 green pass yellow pass red discard
#
traffic policy policy1
classifier class1 behavior behavior1
classifier class2 behavior behavior2
classifier class3 behavior behavior3
#
interface GigabitEthernet0/0/0
ip address 10.1.10.13 255.255.255.252
#
interface GigabitEthernet0/0/1
ip address 10.1.10.2 255.255.255.252
traffic-policy policy1 inbound
#
interface GigabitEthernet0/0/2
ip address 10.1.10.17 255.255.255.252
#
ospf 1 router-id 3.3.3.3
area 0.0.0.0
authentication-mode md5 1 cipher ~1:a.wr./6;BH^68NhwO[_F#
network 10.1.10.0 0.0.0.3
network 10.1.10.12 0.0.0.3
network 10.1.10.16 0.0.0.3
--------------------------------------------------
sysname R2
acl number 2000
rule 5 permit source 192.168.10.0 0.0.0.255
rule 10 permit source 192.168.11.0 0.0.0.255
acl number 2001
rule 5 permit source 192.168.12.0 0.0.0.255
rule 10 permit source 192.168.13.0 0.0.0.255
acl number 2002
rule 5 permit source 192.168.14.0 0.0.0.255
rule 10 permit source 192.168.15.0 0.0.0.255
#
traffic classifier class3 operator or
if-match acl 2002
traffic classifier class2 operator or
if-match acl 2001
traffic classifier class1 operator or
if-match acl 2000
#
traffic behavior behavior1
car cir 200000 cbs 37600000 pbs 62600000 green pass yellow pass red discard
traffic behavior behavior2
car cir 100000 cbs 18800000 pbs 31300000 green pass yellow pass red discard
traffic behavior behavior3
car cir 50000 cbs 9400000 pbs 15650000 green pass yellow pass red discard
#
traffic policy policy1
classifier class1 behavior behavior1
classifier class2 behavior behavior2
classifier class3 behavior behavior3
#
interface GigabitEthernet0/0/0
ip address 10.1.10.21 255.255.255.252
#
interface GigabitEthernet0/0/1
ip address 10.1.10.6 255.255.255.252
traffic-policy policy1 inbound
#
interface GigabitEthernet0/0/2
ip address 10.1.10.18 255.255.255.252
#
ospf 1 router-id 4.4.4.4
area 0.0.0.0
authentication-mode md5 1 cipher l3(!FIA7n~ani^>"qh^;e`,#
network 10.1.10.4 0.0.0.3
network 10.1.10.16 0.0.0.3
network 10.1.10.20 0.0.0.3
---------------------------------------------------------------------------------------------------------------------------------
负载防火墙
sysname FW1
#
hrp enable
hrp interface GigabitEthernet1/0/3 remote 1.1.1.2
hrp standby config enable
hrp track interface GigabitEthernet1/0/0
hrp track interface GigabitEthernet1/0/1
hrp track interface GigabitEthernet1/0/2
hrp track interface GigabitEthernet1/0/4
hrp track ip-link test
#
ip-link check enable
ip-link name test
destination 200.1.1.2 interface GigabitEthernet1/0/1 mode icmp
destination 201.1.1.6 interface GigabitEthernet1/0/2 mode icmp
destination 202.1.1.2 interface GigabitEthernet1/0/4 mode icmp
#
interface GigabitEthernet1/0/0
undo shutdown
ip address 10.1.10.14 255.255.255.252
link-group 1
#
interface GigabitEthernet1/0/1
undo shutdown
ip address 200.1.1.1 255.255.255.252
link-group 1
service-manage ping permit
#
interface GigabitEthernet1/0/2
undo shutdown
ip address 201.1.1.5 255.255.255.252
link-group 1
service-manage ping permit
#
interface GigabitEthernet1/0/3
undo shutdown
ip address 1.1.1.1 255.255.255.252
#
interface GigabitEthernet1/0/4
undo shutdown
ip address 202.1.1.1 255.255.255.252
link-group 1
#
firewall zone trust
set priority 85
add interface GigabitEthernet0/0/0
add interface GigabitEthernet1/0/0
#
firewall zone untrust
set priority 5
add interface GigabitEthernet1/0/1
add interface GigabitEthernet1/0/2
add interface GigabitEthernet1/0/4
#
firewall zone dmz
set priority 50
add interface GigabitEthernet1/0/3
#
ospf 1 router-id 5.5.5.5
default-route-advertise
area 0.0.0.0
authentication-mode md5 1 cipher %^%#U-PmB4R{&FA}xm-)t]IMW5M:E8yKRG)ay'"i5@5G%^%#
network 10.1.10.12 0.0.0.3
#
ip route-static 10.0.0.0 255.0.0.0 200.1.1.2
ip route-static 20.0.0.0 255.0.0.0 201.1.1.6
ip route-static 30.0.0.0 255.0.0.0 202.1.1.2
#
security-policy
rule name t-u
source-zone trust
destination-zone untrust
source-address 192.168.10.0 mask 255.255.255.0
source-address 192.168.11.0 mask 255.255.255.0
source-address 192.168.12.0 mask 255.255.255.0
source-address 192.168.13.0 mask 255.255.255.0
source-address 192.168.14.0 mask 255.255.255.0
source-address 192.168.15.0 mask 255.255.255.0
action permit
#
nat-policy
rule name t-u
source-zone trust
destination-zone untrust
source-address 192.168.10.0 mask 255.255.255.0
source-address 192.168.11.0 mask 255.255.255.0
source-address 192.168.12.0 mask 255.255.255.0
source-address 192.168.13.0 mask 255.255.255.0
source-address 192.168.14.0 mask 255.255.255.0
source-address 192.168.15.0 mask 255.255.255.0
action source-nat easy-ip
--------------------------------------------------
sysname FW2
#
hrp enable
hrp interface GigabitEthernet1/0/3 remote 1.1.1.1
hrp standby config enable
hrp track interface GigabitEthernet1/0/0
hrp track interface GigabitEthernet1/0/1
hrp track interface GigabitEthernet1/0/2
hrp track interface GigabitEthernet1/0/4
hrp track ip-link test
#
ip-link check enable
ip-link name test
destination 200.1.1.6 interface GigabitEthernet1/0/1 mode icmp
destination 201.1.1.2 interface GigabitEthernet1/0/2 mode icmp
destination 202.1.1.6 interface GigabitEthernet1/0/4 mode icmp
#
interface GigabitEthernet1/0/0
undo shutdown
ip address 10.1.10.22 255.255.255.252
link-group 1
#
interface GigabitEthernet1/0/1
undo shutdown
ip address 200.1.1.5 255.255.255.252
link-group 1
service-manage ping permit
#
interface GigabitEthernet1/0/2
undo shutdown
ip address 201.1.1.1 255.255.255.252
link-group 1
service-manage ping permit
#
interface GigabitEthernet1/0/3
undo shutdown
ip address 1.1.1.2 255.255.255.252
#
interface GigabitEthernet1/0/4
undo shutdown
ip address 202.1.1.5 255.255.255.252
link-group 1
#
firewall zone trust
set priority 85
add interface GigabitEthernet0/0/0
add interface GigabitEthernet1/0/0
#
firewall zone untrust
set priority 5
add interface GigabitEthernet1/0/1
add interface GigabitEthernet1/0/2
add interface GigabitEthernet1/0/4
#
firewall zone dmz
set priority 50
add interface GigabitEthernet1/0/3
#
ospf 1 router-id 6.6.6.6
default-route-advertise
area 0.0.0.0
authentication-mode md5 1 cipher %^%#U-PmB4R{&FA}xm-)t]IMW5M:E8yKRG)ay'"i5@5G%^%#
network 10.1.10.20 0.0.0.3
#
ip route-static 10.0.0.0 255.0.0.0 200.1.1.6
ip route-static 20.0.0.0 255.0.0.0 201.1.1.2
ip route-static 30.0.0.0 255.0.0.0 202.1.1.6
#
security-policy
rule name t-u
source-zone trust
destination-zone untrust
source-address 192.168.10.0 mask 255.255.255.0
source-address 192.168.11.0 mask 255.255.255.0
source-address 192.168.12.0 mask 255.255.255.0
source-address 192.168.13.0 mask 255.255.255.0
source-address 192.168.14.0 mask 255.255.255.0
source-address 192.168.15.0 mask 255.255.255.0
action permit
#
nat-policy
rule name t-u
source-zone trust
destination-zone untrust
source-address 192.168.10.0 mask 255.255.255.0
source-address 192.168.11.0 mask 255.255.255.0
source-address 192.168.12.0 mask 255.255.255.0
source-address 192.168.13.0 mask 255.255.255.0
source-address 192.168.14.0 mask 255.255.255.0
source-address 192.168.15.0 mask 255.255.255.0
action source-nat easy-ip
-------------------------------------------------------------
外网路由器配置
sysname ISP1
#
interface GigabitEthernet0/0/0
ip address 200.1.1.2 255.255.255.252
#
interface GigabitEthernet0/0/1
ip address 200.1.1.6 255.255.255.252
#
interface LoopBack0
ip add 10.10.10.10 32
#
ospf 1
area 0.0.0.0
network 0.0.0.0 255.255.255.255
----------------------------------------------
sysname ISP2
#
interface GigabitEthernet0/0/0
ip address 201.1.1.6 255.255.255.252
#
interface GigabitEthernet0/0/1
ip address 201.1.1.2 255.255.255.252
#
interface LoopBack0
ip add 20.20.20.20 32
#
ospf 1
area 0.0.0.0
network 0.0.0.0 255.255.255.255 文章来源:https://www.toymoban.com/news/detail-472292.html
-----------------------------------------------
sysname ISP3
#
interface GigabitEthernet0/0/0
ip address 202.1.1.2 255.255.255.252
#
interface GigabitEthernet0/0/1
ip address 202.1.1.6 255.255.255.252
#
interface LoopBack0
ip add 30.30.30.30 32
#
ospf 1
area 0.0.0.0
network 0.0.0.0 255.255.255.255 文章来源地址https://www.toymoban.com/news/detail-472292.html
到了这里,关于网络毕业设计--基于华为ensp防火墙双出口负载拟真实验的文章就介绍完了。如果您还想了解更多内容,请在右上角搜索TOY模板网以前的文章或继续浏览下面的相关文章,希望大家以后多多支持TOY模板网!