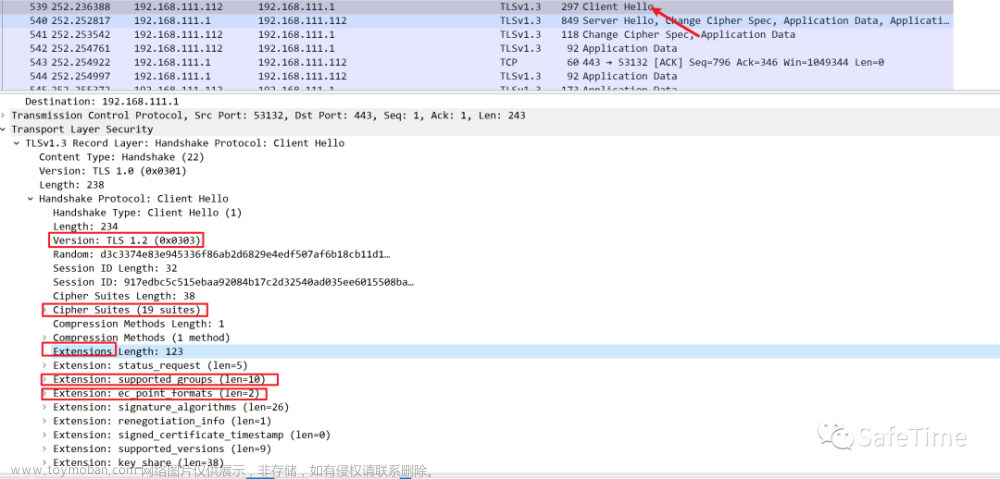
- curl_cffi: 支持原生模拟浏览器 TLS/JA3 指纹的 Python 库
pip install curl_cffi
from curl_cffi import requests
proxy = {
'PROXY_USER': "xxx",
'PROXY_PASS': "xxx",
'PROXY_SERVER': "http://ip:port"
}
def get_proxys():
proxy_host = proxy.get('PROXY_SERVER').rsplit(
':', maxsplit=1)[0].split('//')[-1]
proxy_port = proxy.get('PROXY_SERVER').rsplit(':', maxsplit=1)[-1]
proxy_username = proxy.get('PROXY_USER')
proxy_pwd = proxy.get('PROXY_PASS')
proxyMeta = "http://%(user)s:%(pass)s@%(host)s:%(port)s" % {
"host": proxy_host,
"port": proxy_port,
"user": proxy_username,
"pass": proxy_pwd,
}
proxies = {
'http': proxyMeta,
'https': proxyMeta,
}
return proxies
url = "https://www.infinigo.com/cps/299027a8-9e4d-11ea-b100-20040fe763d8"
# url = "https://www.infinigo.com/classify/08007"
# url = "https://www.infinigo.com/category/"
payload = {}
response = requests.get(url, data=payload, proxies=get_proxys(), allow_redirects=False, impersonate="chrome101")
print(response.text)
- Pyhttpx: https://github.com/zero3301/pyhttpx
pip install pyhttpx
import pyhttpx
proxies = {'https': 'ip:port', 'http': 'ip:port'}
proxy_auth = ("xxx", "xxxx")
url = "https://www.infinigo.com/cps/299027a8-9e4d-11ea-b100-20040fe763d8"
# url = "https://www.infinigo.com/classify/08007"
# url = "https://www.infinigo.com/category/"
payload={}
sess = pyhttpx.HttpSession(browser_type='chrome', http2=True)
response = sess.get(url, proxies=proxies, proxy_auth=proxy_auth, allow_redirects=False)
print(response.text)
- 修改urllib3 ssl_源码的DEFAULT_CIPHERS里的加密算法
requests版本
scrapy版本
文章来源地址https://www.toymoban.com/news/detail-521470.html
文章来源:https://www.toymoban.com/news/detail-521470.html
到了这里,关于python解决JA3 TLS指纹反爬几种方案的文章就介绍完了。如果您还想了解更多内容,请在右上角搜索TOY模板网以前的文章或继续浏览下面的相关文章,希望大家以后多多支持TOY模板网!