准备
手机得是root过的,然后从这个网站https://github.com/frida/frida/releases下载对应版本的frida-server,现在的手机大多数都是arm64的。
电脑上下载adb,手机用USB连到电脑上,打开开发者选项的USB调试。adb devices确认已经连接,用adb push把frida-server传到手机上,chmod 777后切换到root用户下运行。这一步手机上会向你确认adb要求root权限,可以用magisk管理root权限。
adb push arm64-frida-server /data/local/tmp
adb shell
chmod 777 /data/local/tmp/arm64-frida-server
su
./data/local/tmp/arm64-frida-server
在电脑上安装frida,直接用pip安装,常见的问题可以看这篇文章:
https://www.jianshu.com/p/25b430bb60a6
电脑端设置一下端口转发
adb forward tcp:27042 tcp:27042
adb forward tcp:27043 tcp:27043
先frida-ps -U看一下有没有成功连接上,同时还能看到你要hook的app的进程名。
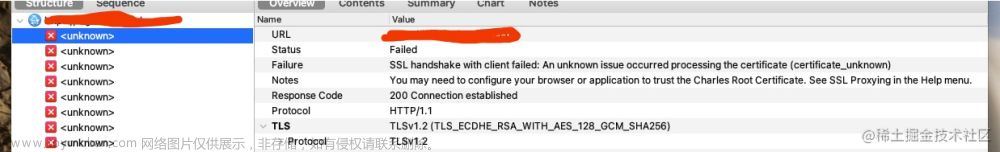
绕过ssl pinning的frida脚本如下,用途是在使用fiddler抓包的时候给手机安装了fiddler的证书但是app只信任自己的根证书因此app连不上网或者抓不到https包。文章来源:https://www.toymoban.com/news/detail-522620.html
import frida
import sys
print("start")
session = frida.get_usb_device().attach('Facebook')
src = """
setTimeout(function(){
Java.perform(function() {
var array_list = Java.use("java.util.ArrayList");
var ApiClient = Java.use('com.android.org.conscrypt.TrustManagerImpl');
ApiClient.checkTrustedRecursive.implementation = function(a1, a2, a3, a4, a5, a6) {
console.log('Bypassing SSL Pinning');
var k = array_list.$new();
return k;
}
});
},0);
"""
def on_message(message, data):
if message["type"] == "send":
print("[+] {}".format(message["payload"]))
else:
print("[-] {}".format(message))
script = session.create_script(src)
script.on("message", on_message)
script.load()
sys.stdin.read()
或者写成xposed模块,现在都是用在lsposed上了。lsposed的安装和模块编写可以看我其他的文章。文章来源地址https://www.toymoban.com/news/detail-522620.html
package com.xposed.ssl;
import de.robv.android.xposed.IXposedHookLoadPackage;
import de.robv.android.xposed.XC_MethodHook;
import de.robv.android.xposed.XposedBridge;
import de.robv.android.xposed.XposedHelpers;
import de.robv.android.xposed.callbacks.XC_LoadPackage;
import java.security.cert.X509Certificate;
import java.util.ArrayList;
import java.util.Set;
public class passHook implements IXposedHookLoadPackage {
@Override
public void handleLoadPackage(XC_LoadPackage.LoadPackageParam lpparam) throws Throwable {
XposedBridge.log("Loaded app: " + lpparam.packageName);
//[Ljava.security.cert.X509Certificate;', '[B', '[B', 'java.lang.String', 'boolean', 'java.util.ArrayList', 'java.util.ArrayList', 'java.util.Set'
Class<?> trustmanager = lpparam.classLoader.loadClass("com.android.org.conscrypt.TrustManagerImpl");
XposedHelpers.findAndHookMethod(trustmanager, "checkTrustedRecursive",
X509Certificate[].class, byte[].class, byte[].class, String.class, boolean.class, ArrayList.class, ArrayList.class, Set.class, new XC_MethodHook() {
@Override
protected void beforeHookedMethod(MethodHookParam param) throws Throwable {
super.beforeHookedMethod(param);
XposedBridge.log("ssl pinning start");
}
@Override
protected void afterHookedMethod(MethodHookParam param) throws Throwable {
super.afterHookedMethod(param);
ArrayList result = new ArrayList();
param.setResult(result);
}
});
}
}
到了这里,关于手机frida绕过ssl pinning的文章就介绍完了。如果您还想了解更多内容,请在右上角搜索TOY模板网以前的文章或继续浏览下面的相关文章,希望大家以后多多支持TOY模板网!