es官网下载地址:https://www.elastic.co/cn/downloads/past-releases#elasticsearch
可以去官网下载包然后放到服务器
也可以使用wget进行下载安装
如果使用wget方式下载的话需要先安装
安装wget
yum install -y wget

wget下载es:wget https://artifacts.elastic.co/downloads/elasticsearch/elasticsearch-8.8.0-linux-x86_64.tar.gz
wget下载Kibana:wget https://artifacts.elastic.co/downloads/kibana/kibana-8.8.0-linux-x86_64.tar.gz 
下载完成后进行解压
tar -zxvf elasticsearch-8.8.0-linux-x86_64.tar.gz
tar -zxvf kibana-8.8.0-linux-x86_64.tar.gz

修改ElasticSearch配置文件
Es默认分配了2G的内存,如果Linux服务配置本来就很高可以不做修改
进入config文件夹开始配置
cd /home/elasticSearch/elasticsearch-8.8.0/config
vi jvm.options
## -Xms4g
## -Xmx4g
改为
-Xms256m
-Xmx256m

修改ElasticSearch核心文件
在 es目录下创建data文件
vi elasticsearch.yml
cluster.name: mycluster
node.name: node-1
network.host: 0.0.0.0
bootstrap.memory_lock: false
http.port: 9200
xpack.security.enabled: true
xpack.security.enrollment.enabled: true
# Enable encryption for HTTP API client connections, such as Kibana, Logstash, and Agents
xpack.security.http.ssl:
enabled: false
keystore.path: certs/http.p12
# Enable encryption and mutual authentication between cluster nodes
# 跨域
http.cors.enabled: true
http.cors.allow-origin: "*"
http.cors.allow-headers: Authorization,X-Requested-With,Content-Type,Content-Length
xpack.security.enabled: true
xpack.security.authc.accept_default_password: true
xpack.security.transport.ssl.enabled: true
xpack.security.transport.ssl.verification_mode: certificate
xpack.security.transport.ssl.keystore.path: /home/elasticSearch/elasticsearch-8.8.0/elastic-certificates.p12
xpack.security.transport.ssl.truststore.path: /home/elasticSearch/elasticsearch-8.8.0/elastic-certificates.p12
# Create a new cluster with the current node only
# Additional nodes can still join the cluster later
cluster.initial_master_nodes: ["iZ8vb6tda6e8mwssfo6usfZ"]
# Allow HTTP API connections from anywhere
# Connections are encrypted and require user authentication
http.host: 0.0.0.0
path:
data: /home/elasticSearch/elasticsearch-8.8.0/data #数据路径
logs: /home/elasticSearch/elasticsearch-8.8.0/logs #日志路径
修改配置 sysctl.conf
vi /etc/sysctl.conf
# 编辑如下信息
vm.max_map_count=655360
# 保存退出,执行以下命令
/sbin/sysctl -p
创建ElasticSearch专属用户启动
root用户不能直接启动,所以需要创建一个专用用户,来启动Es,如果没有报错则已经启动成功,Es默认只能本地连接,可以对核心配置文件进行修改来支持外部连接
创建elastic用户
useradd elastic
chown elastic:elastic -R /home/elasticSearch
切换用户
su elastic
进入bin目录
cd /home/elasticSearch/elasticsearch-8.8.0/bin
后台启动es
./elasticsearch -d
启动报错:bootstrap check failure [1] of [1]: max file descriptors [4096] for elasticsearch process is too low, increase to at least [65535]
解决方案:
vi /etc/security/limits.conf
加入下面配置
* hard nofile 65535 # *可以是es启动用户
* soft nofile 65535
vi /etc/security/limits.conf
关闭连接工具重新连接服务器然后再启动es
./elasticsearch -d
设置elastic、kibana、logstash等的访问密码
./elasticsearch-setup-passwords interactive
如果报错ERROR: Failed to verify bootstrap password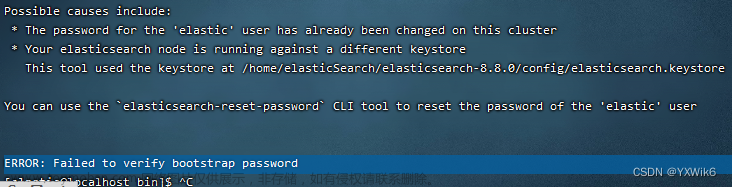
则根据提示重新生成密码
elasticsearch-reset-password -u elastic

如果需要设置自定义密码 增加参数 -i
elasticsearch-reset-password -u elastic -i
Elasticsearch开启安全认证
生成证书:
cd /home/elasticSearch/elasticsearch-8.8.0/bin
./elasticsearch-certutil ca
碰到第一个直接回车,不用管
碰到第二个输入密码,例如123456
完成后会生成一个文件:elastic-stack-ca.p12
生成秘钥:
./elasticsearch-certutil cert --ca elastic-stack-ca.p12
看见password就输入刚才设置的密码 ,其他就直接回车,之后会生成一个文件:elastic-certificates.p12文件

赋权
chmod 777 /home/elasticSearch/elasticsearch-8.8.0/elastic-certificates.p12
添加密码
./elasticsearch-keystore add xpack.security.transport.ssl.keystore.secure_password
输入密码:第一步中设置的密码,123456
./elasticsearch-keystore add xpack.security.transport.ssl.truststore.secure_password
生成节点正书
elasticsearch-certutil http
Generate a CSR? [y/N]n:是否生成 CSR,输入 n
Use an existing CA? [y/N]y:用已经存在的根证书,输入 y
CA Path: /usr/share/elasticsearch/elastic-stack-ca.p12:输入根证书的绝对路径
Password for elastic-stack-ca.p12:输入根证书的密码
For how long should your certificate be valid? [5y] :证书有效期,默认为 5y(5年)
Generate a certificate per node? [y/N]:是否为每一个节点都生成证书
Enter all the hostnames that you need, one per line.:输入集群中节点的主机名,回车两次跳过即可
Enter all the IP addresses that you need, one per line.:输入集群中节点的IP地址,回车两次跳过即可
Do you wish to change any of these options? [y/N]n:是否要改变选项,输入 n
Provide a password for the “http.p12” file: [ for none]:输入私钥 http.p12 的密码,回车不设置密码
What filename should be used for the output zip file? :输出的压缩文件的文件名
之后会生成 elasticsearch-ssl-http.zip在根目录
将其中的elasticsearch 文件夹下的http.p12文件放到 /home/elasticSearch/elasticsearch-8.8.0/config 目录下

更改es配置文件中keystore.path 的路径
剩下压缩包中的kibana 文件夹下的证书也放到对应目录下
将 elasticsearch-ca.pem 为你文件复制到 Kibana 配置目录

修改配置文件kibana.yml
添加如下内容
elasticsearch.ssl.certificateAuthorities: /home/elasticSearch/kibana-8.8.0/config/elasticsearch-ca.pem
启动ES
java
./elasticsearch -d
设置elastic、kibana、logstash等的访问密码
./elasticsearch-setup-passwords interactive
配置Kibana
cd /home/elasticSearch/kibana-8.8.0/config
vi kibana.yml
增加如下配置,es需要配置自己es的账号密码
server.port: 5601
server.host: "0.0.0.0"
elasticsearch.hosts: ["http://localhost:9200"]
#es的账号密码,如果设置了必须修改以下两行
elasticsearch.username: "elastic"
elasticsearch.password: "Qg4AHjAoTobf0HyAt3ml"
#改为中文
i18n.locale: "zh-CN"
执行如下命令:./kibana-encryption-keys generate
会生成如下三个key
我们可以把这三个同时拷贝,并添加到 config/kibana.yml 文件的后面
启动
cd /home/elasticSearch/kibana-8.8.0/bin
./kibana
启动成功进行访问
然后根据要求配置注册令牌
cd /home/elasticSearch/elasticsearch-8.8.0/bin

elasticsearch-create-enrollment-token --scope kibana

将令牌粘贴至页面然后出现验证
运行
cd /home/elasticSearch/kibana-8.8.0/bin
kibana-verification-code




账号是:elastic
这里的密码就是上面执行elasticsearch-reset-password -u elastic 重置的密码Qg4AHjAoTobf0HyAt3ml
如果忘记了就再执行下重置密码
后台运行 kibana
nohup ./kibana > nohup.out 2>&1 &
问题整理: FATAL Error: Port 5601 is already in use. Another instance of Kibana may be running!
5601端口占用问题
查询端口进程 并kill掉
fuser -n tcp 5601

如果启动kibana报如下错误
解决方案:Elasticsearch和Kibana之间HTTPS连接文章来源:https://www.toymoban.com/news/detail-544826.html
然后重启就好了文章来源地址https://www.toymoban.com/news/detail-544826.html
到了这里,关于Linux安装ElasticSearch和Kibana的文章就介绍完了。如果您还想了解更多内容,请在右上角搜索TOY模板网以前的文章或继续浏览下面的相关文章,希望大家以后多多支持TOY模板网!