目录
一、前言
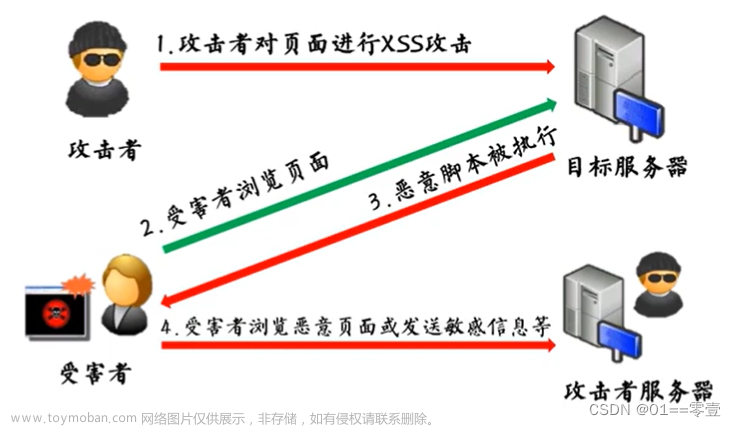
1.1、XSS攻击流程
1.2、XSS攻击分类
1.3、攻击方式
二、解决方案
2.1、SPRINGBOOT XSS过滤插件(MICA-XSS)
2.2、MICA-XSS 配置
三、项目实战
3.1、项目环境
3.2、测试
3.2.1、测试GET请求
3.2.2、测试POST请求
3.2.3、测试POST请求
四、MICA-XSS 原理剖析
4.1、MICA-XSS 源码
一、前言
XSS攻击又称跨站脚本攻击,通常指利用网页开发时留下的漏洞,通过巧妙的方法注入恶意指令代码到网页,使用户加载并执行攻击者恶意制造的网页程序。这些恶意网页程序通常是JavaScript,但实际上也可以包括Java、 VBScript、ActiveX、 Flash 或者甚至是普通的HTML。攻击成功后,攻击者可能得到包括但不限于更高的权限(如执行一些操作)、私密网页内容、会话和cookie等各种内容。
1.1、XSS攻击流程
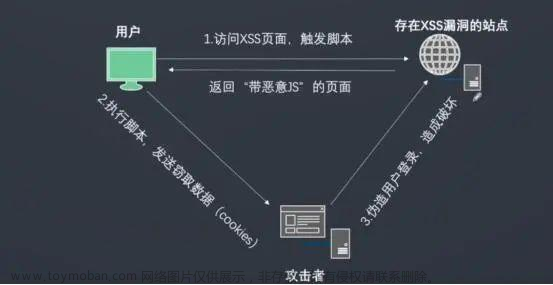
例如在设计某个表单时,没做相关防XSS攻击的处理。用户通过该表单提交相关恶意代码,浏览器会执行相关的代码,从而发起XSS攻击。如下图:
1.2、XSS攻击分类
<span style="background-color:#fafafa"><span style="color:#000000"><code>XSS攻击具有三类:反射型、存储型和DOM XSS
</code></span></span>- 1
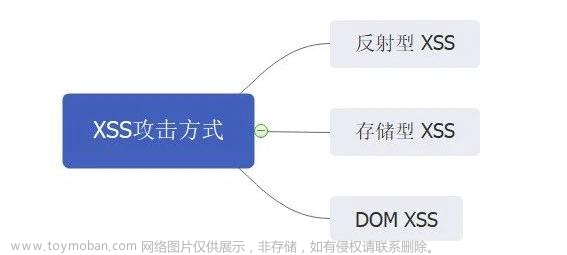
说明:
-
反射型 XSS:通过将XSS攻击代码放在请求URL上,将其作为输入提交到服务器端。当服务器端解析提交后,XSS代码会随着响应内容一起传回浏览器,最后浏览器解析并执行XSS代码。由于整个过程像一个反射,因此称为反射型XSS。如发起如下请求:
https://www.域名.com/index.php?xss=<script>alter(xss攻击)</script> - 存储型 XSS:与反射型XSS“相似”,但不同的是提交的XSS代码会被存储在服务器端,当下一次请求该页面时,不用提交XSS代码,也会触发XSS攻击。例如当进行用户注册时,用户提交一条包含XSS代码的注册信息到服务器端,当用户查看个人信息时候,那些个人信息就会被浏览器当成正常的HTML和JS解析执行,从而触发了XSS攻击。
-
DOM XSS:与反射型和存储型XSS不同之处在于,DOM XSS不需要服务器的参与,通过浏览器的DOM解析即可触发XSS攻击,避免了服务器端的信息检验和字符过滤。如发起如下请求:
https://www.域名.com/index.html#alert(xss攻击)
1.3、攻击方式
XSS攻击方式很多,这里只介绍一些常用的XSS攻击手段以及其目的,为提出Springboot项目防止XSS攻击解决方案做说明。例如:
-
盗用cookie,获取敏感信息。
-
利用植入Flash,通过crossdomain权限设置进一步获取更高权限;或者利用Java等得到类似的操作。
-
利用iframe、frame、XMLHttpRequest或上述Flash等方式,以(被攻击)用户的身份执行一些管理动作,或执行一些一般的如发微博、加好友、发私信等操作。
-
利用可被攻击的域受到其他域信任的特点,以受信任来源的身份请求一些平时不允许的操作,如进行不当的投票活动。
-
在访问量极大的一些页面上的XSS可以攻击一些小型网站,实现DDoS攻击的效果。
许多初级Springboot开发人员经常中此招,最近在测试个人项目时,也出现了这个问题。那么在Springboot项目中,我们该如何防止XSS攻击呢?
二、解决方案
通过对XSS攻击的介绍,我们知道了XSS常从表单输入、URL请求、以及Cookie等方面进行攻击。因此,我们可以从如下几个方面进行防止XSS攻击。
- 对表单数据进行XSS处理
- 对URL请求数据(JSON)进行XSS处理
- 对URL和服务器端控制器方法设置数据放行规则
其实这些解决方案都不用我们自己去实现,SpringBoot 对应的Maven插件为我们提供了对于的XSS 安全过滤插件:mica-core 和 mica-xss
2.1、SPRINGBOOT XSS过滤插件(MICA-XSS)
<span style="background-color:#fafafa"><span style="color:#000000"><code> 添加Maven依赖后,便已经完成了XSS过滤配置。
</code></span></span>- 1
mica-xss组件说明:
- 对表单绑定的字符串类型进行 xss 处理。
- 对 json 字符串数据进行 xss 处理。
- 提供路由和控制器方法级别的放行规则。
<span style="background-color:#fafafa"><span style="color:#000000"><code class="language-java"><span style="color:#dd4a68"><span style="color:#999999"><</span>dependency<span style="color:#999999">></span></span>
<span style="color:#dd4a68"><span style="color:#999999"><</span>groupId<span style="color:#999999">></span></span>net<span style="color:#999999">.</span>dreamlu<span style="color:#a67f59"><</span><span style="color:#a67f59">/</span>groupId<span style="color:#a67f59">></span>
<span style="color:#dd4a68"><span style="color:#999999"><</span>artifactId<span style="color:#999999">></span></span>mica<span style="color:#a67f59">-</span>xss<span style="color:#a67f59"><</span><span style="color:#a67f59">/</span>artifactId<span style="color:#a67f59">></span>
<span style="color:#dd4a68"><span style="color:#999999"><</span>version<span style="color:#999999">></span></span><span style="color:#986801">2.0</span><span style="color:#986801">.9</span><span style="color:#a67f59">-</span>GA<span style="color:#a67f59"><</span><span style="color:#a67f59">/</span>version<span style="color:#a67f59">></span>
<span style="color:#a67f59"><</span><span style="color:#a67f59">/</span>dependency<span style="color:#a67f59">></span>
<span style="color:#dd4a68"><span style="color:#999999"><</span>dependency<span style="color:#999999">></span></span>
<span style="color:#dd4a68"><span style="color:#999999"><</span>groupId<span style="color:#999999">></span></span>net<span style="color:#999999">.</span>dreamlu<span style="color:#a67f59"><</span><span style="color:#a67f59">/</span>groupId<span style="color:#a67f59">></span>
<span style="color:#dd4a68"><span style="color:#999999"><</span>artifactId<span style="color:#999999">></span></span>mica<span style="color:#a67f59">-</span>core<span style="color:#a67f59"><</span><span style="color:#a67f59">/</span>artifactId<span style="color:#a67f59">></span>
<span style="color:#dd4a68"><span style="color:#999999"><</span>version<span style="color:#999999">></span></span><span style="color:#986801">2.1</span><span style="color:#986801">.0</span><span style="color:#a67f59">-</span>GA<span style="color:#a67f59"><</span><span style="color:#a67f59">/</span>version<span style="color:#a67f59">></span>
<span style="color:#a67f59"><</span><span style="color:#a67f59">/</span>dependency<span style="color:#a67f59">></span>
</code></span></span>2.2、MICA-XSS 配置
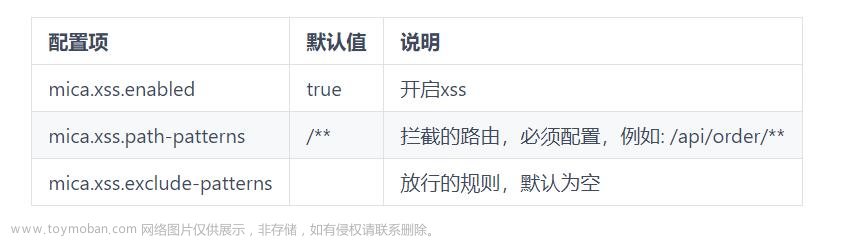
mica:
xss:
enabled: true
path-exclude-patterns:
path-patterns: /**三、项目实战
3.1、项目环境
开发工具:IDEA-2020.02 Springboot 2.4.1
测试工具:Google浏览器 Postman
3.2、测试
3.2.1、测试GET请求
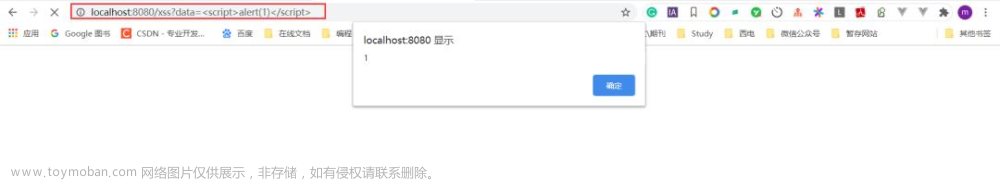
未设置XSS防护:
添加注解@XssCleanIgnore跳过XSS过滤
<span style="background-color:#fafafa"><span style="color:#000000"><code class="language-java"><span style="color:#0077aa">import</span> net<span style="color:#999999">.</span>dreamlu<span style="color:#999999">.</span>mica<span style="color:#999999">.</span>xss<span style="color:#999999">.</span>core<span style="color:#999999">.</span>XssCleanIgnore<span style="color:#999999">;</span>
<span style="color:#0077aa">import</span> org<span style="color:#999999">.</span>springframework<span style="color:#999999">.</span>web<span style="color:#999999">.</span>bind<span style="color:#999999">.</span>annotation<span style="color:#999999">.</span>GetMapping<span style="color:#999999">;</span>
<span style="color:#0077aa">import</span> org<span style="color:#999999">.</span>springframework<span style="color:#999999">.</span>web<span style="color:#999999">.</span>bind<span style="color:#999999">.</span>annotation<span style="color:#999999">.</span>RequestMapping<span style="color:#999999">;</span>
<span style="color:#0077aa">import</span> org<span style="color:#999999">.</span>springframework<span style="color:#999999">.</span>web<span style="color:#999999">.</span>bind<span style="color:#999999">.</span>annotation<span style="color:#999999">.</span>RestController<span style="color:#999999">;</span>
<span style="color:#708090">/**
* @author dell
*/</span>
<span style="color:#999999">@RestController</span>
<span style="color:#999999">@XssCleanIgnore</span> <span style="color:#708090">//设置该注解 用于跳过配置的Xss 防护</span>
<span style="color:#999999">@RequestMapping</span><span style="color:#999999">(</span><span style="color:#50a14f">"/"</span><span style="color:#999999">)</span>
<span style="color:#0077aa">public</span> <span style="color:#0077aa">class</span> IndexController <span style="color:#999999">{</span>
<span style="color:#999999">@GetMapping</span><span style="color:#999999">(</span><span style="color:#50a14f">"/xss"</span><span style="color:#999999">)</span>
<span style="color:#0077aa">public</span> String <span style="color:#dd4a68">xssGet</span><span style="color:#999999">(</span>String data<span style="color:#999999">)</span><span style="color:#999999">{</span>
System<span style="color:#999999">.</span>out<span style="color:#999999">.</span><span style="color:#dd4a68">println</span><span style="color:#999999">(</span>data<span style="color:#999999">)</span><span style="color:#999999">;</span>
<span style="color:#0077aa">return</span> data<span style="color:#999999">;</span>
<span style="color:#999999">}</span>
<span style="color:#999999">}</span>
</code></span></span>效果如下:
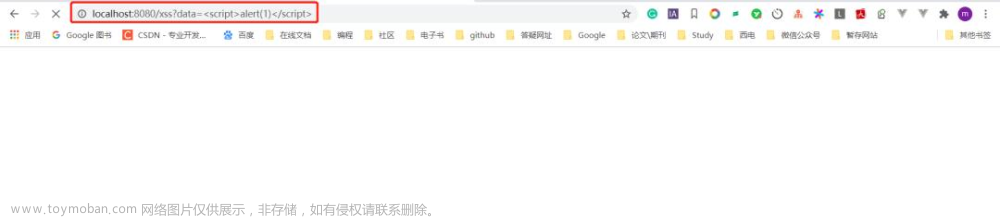
设置XSS防护:
去掉注解 @XssCleanIgnore,返回为空。效果如下
3.2.2、测试POST请求
3.2.2.1、测试POST请求(XSS代码放在URL上)
未设置XSS防护:
添加注解@XssCleanIgnore跳过XSS过滤,返回data数据。
<span style="background-color:#fafafa"><span style="color:#000000"><code class="language-java"><span style="color:#0077aa">import</span> net<span style="color:#999999">.</span>dreamlu<span style="color:#999999">.</span>mica<span style="color:#999999">.</span>xss<span style="color:#999999">.</span>core<span style="color:#999999">.</span>XssCleanIgnore<span style="color:#999999">;</span>
<span style="color:#0077aa">import</span> org<span style="color:#999999">.</span>springframework<span style="color:#999999">.</span>web<span style="color:#999999">.</span>bind<span style="color:#999999">.</span>annotation<span style="color:#999999">.</span>PostMapping<span style="color:#999999">;</span>
<span style="color:#0077aa">import</span> org<span style="color:#999999">.</span>springframework<span style="color:#999999">.</span>web<span style="color:#999999">.</span>bind<span style="color:#999999">.</span>annotation<span style="color:#999999">.</span>RequestMapping<span style="color:#999999">;</span>
<span style="color:#0077aa">import</span> org<span style="color:#999999">.</span>springframework<span style="color:#999999">.</span>web<span style="color:#999999">.</span>bind<span style="color:#999999">.</span>annotation<span style="color:#999999">.</span>RestController<span style="color:#999999">;</span>
<span style="color:#708090">/**
* @author dell
*/</span>
<span style="color:#999999">@RestController</span>
<span style="color:#999999">@XssCleanIgnore</span> <span style="color:#708090">//设置该注解 用于跳过配置的Xss 防护</span>
<span style="color:#999999">@RequestMapping</span><span style="color:#999999">(</span><span style="color:#50a14f">"/"</span><span style="color:#999999">)</span>
<span style="color:#0077aa">public</span> <span style="color:#0077aa">class</span> IndexController <span style="color:#999999">{</span>
<span style="color:#999999">@PostMapping</span><span style="color:#999999">(</span><span style="color:#50a14f">"/xss"</span><span style="color:#999999">)</span>
<span style="color:#0077aa">public</span> String <span style="color:#dd4a68">xssPost</span><span style="color:#999999">(</span>String data<span style="color:#999999">)</span><span style="color:#999999">{</span>
System<span style="color:#999999">.</span>out<span style="color:#999999">.</span><span style="color:#dd4a68">println</span><span style="color:#999999">(</span>data<span style="color:#999999">)</span><span style="color:#999999">;</span>
<span style="color:#0077aa">return</span> data<span style="color:#999999">;</span>
<span style="color:#999999">}</span>
<span style="color:#999999">}</span>
</code></span></span>效果如下:
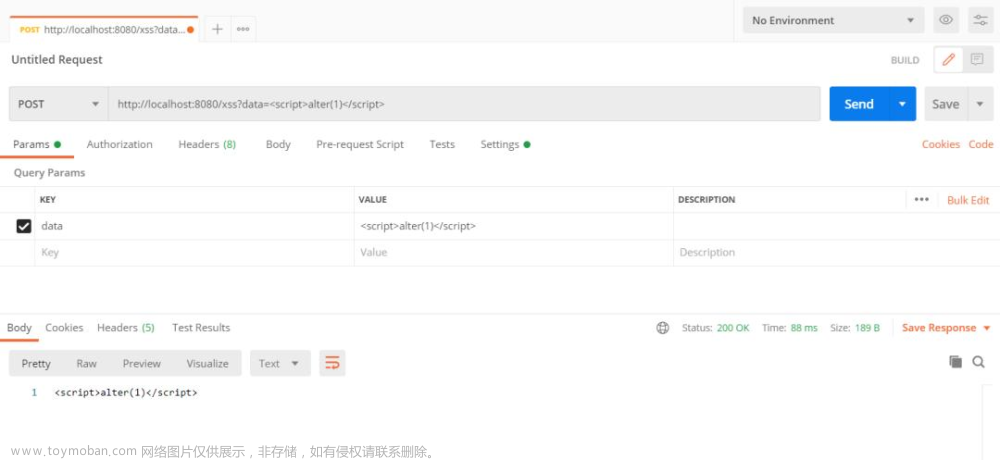
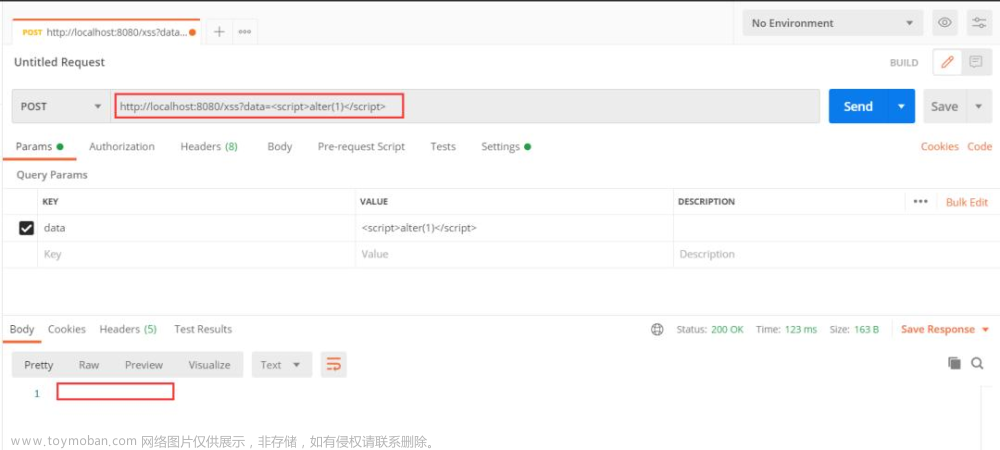
设置XSS防护:
去掉注解@XssCleanIgnore,设置XSS防护,过滤data数据,返回为空。
3.2.2.2、测试POST请求(XSS代码放在 BODY 中)
未设置XSS防护:
<span style="background-color:#fafafa"><span style="color:#000000"><code class="language-java"><span style="color:#0077aa">import</span> net<span style="color:#999999">.</span>dreamlu<span style="color:#999999">.</span>mica<span style="color:#999999">.</span>xss<span style="color:#999999">.</span>core<span style="color:#999999">.</span>XssCleanIgnore<span style="color:#999999">;</span>
<span style="color:#0077aa">import</span> org<span style="color:#999999">.</span>springframework<span style="color:#999999">.</span>web<span style="color:#999999">.</span>bind<span style="color:#999999">.</span>annotation<span style="color:#999999">.</span>PostMapping<span style="color:#999999">;</span>
<span style="color:#0077aa">import</span> org<span style="color:#999999">.</span>springframework<span style="color:#999999">.</span>web<span style="color:#999999">.</span>bind<span style="color:#999999">.</span>annotation<span style="color:#999999">.</span>RequestBody<span style="color:#999999">;</span>
<span style="color:#0077aa">import</span> org<span style="color:#999999">.</span>springframework<span style="color:#999999">.</span>web<span style="color:#999999">.</span>bind<span style="color:#999999">.</span>annotation<span style="color:#999999">.</span>RequestMapping<span style="color:#999999">;</span>
<span style="color:#0077aa">import</span> org<span style="color:#999999">.</span>springframework<span style="color:#999999">.</span>web<span style="color:#999999">.</span>bind<span style="color:#999999">.</span>annotation<span style="color:#999999">.</span>RestController<span style="color:#999999">;</span>
<span style="color:#0077aa">import</span> java<span style="color:#999999">.</span>util<span style="color:#999999">.</span>Map<span style="color:#999999">;</span>
<span style="color:#708090">/**
* @author dell
*/</span>
<span style="color:#999999">@RestController</span>
<span style="color:#999999">@XssCleanIgnore</span>
<span style="color:#999999">@RequestMapping</span><span style="color:#999999">(</span><span style="color:#50a14f">"/"</span><span style="color:#999999">)</span>
<span style="color:#0077aa">public</span> <span style="color:#0077aa">class</span> IndexController <span style="color:#999999">{</span>
<span style="color:#999999">@PostMapping</span><span style="color:#999999">(</span><span style="color:#50a14f">"/xss"</span><span style="color:#999999">)</span>
<span style="color:#0077aa">public</span> String <span style="color:#dd4a68">xssPostBody</span><span style="color:#999999">(</span><span style="color:#999999">@RequestBody</span> Map<span style="color:#dd4a68"><span style="color:#999999"><</span>String<span style="color:#999999">,</span>String<span style="color:#999999">></span></span> body<span style="color:#999999">)</span><span style="color:#999999">{</span>
System<span style="color:#999999">.</span>out<span style="color:#999999">.</span><span style="color:#dd4a68">println</span><span style="color:#999999">(</span>body<span style="color:#999999">)</span><span style="color:#999999">;</span>
<span style="color:#0077aa">return</span> body<span style="color:#999999">.</span><span style="color:#dd4a68">get</span><span style="color:#999999">(</span><span style="color:#50a14f">"data"</span><span style="color:#999999">)</span><span style="color:#999999">;</span>
<span style="color:#999999">}</span>
<span style="color:#999999">}</span>
</code></span></span>效果如下:
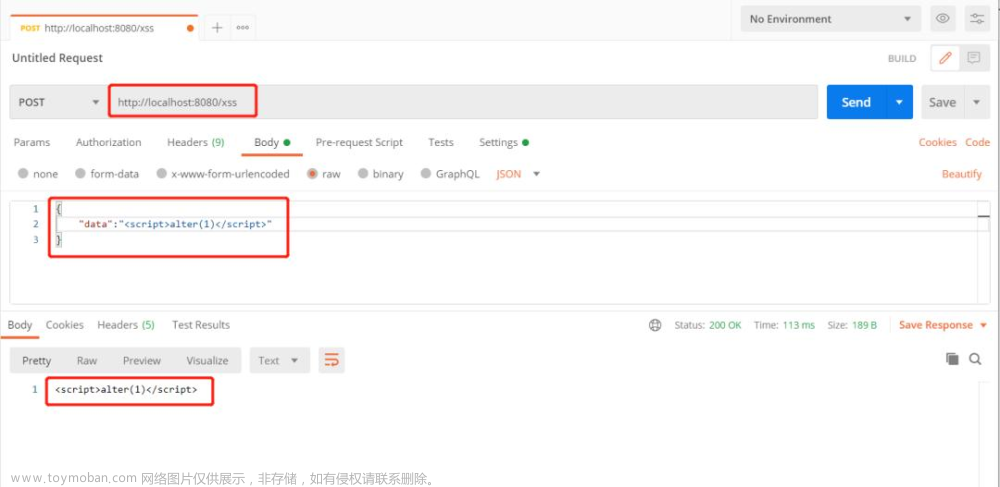
设置XSS防护:
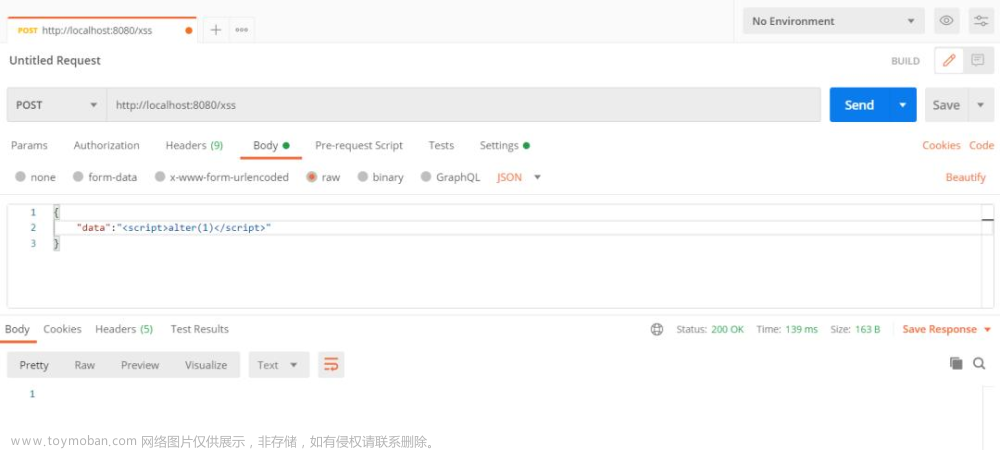
3.2.3、测试POST请求
如果使用request.getParameter("xss")); 等等ServletRequest原生方法,则是MICA拦截不到的,需要补充下面文章的过滤器,亲测有用,原理就是重写了原生的一些方法.添加过滤.
SpringBoot集成Hutool防止XSS攻击实现_wcybaonier的博客-CSDN博客
四、MICA-XSS 原理剖析
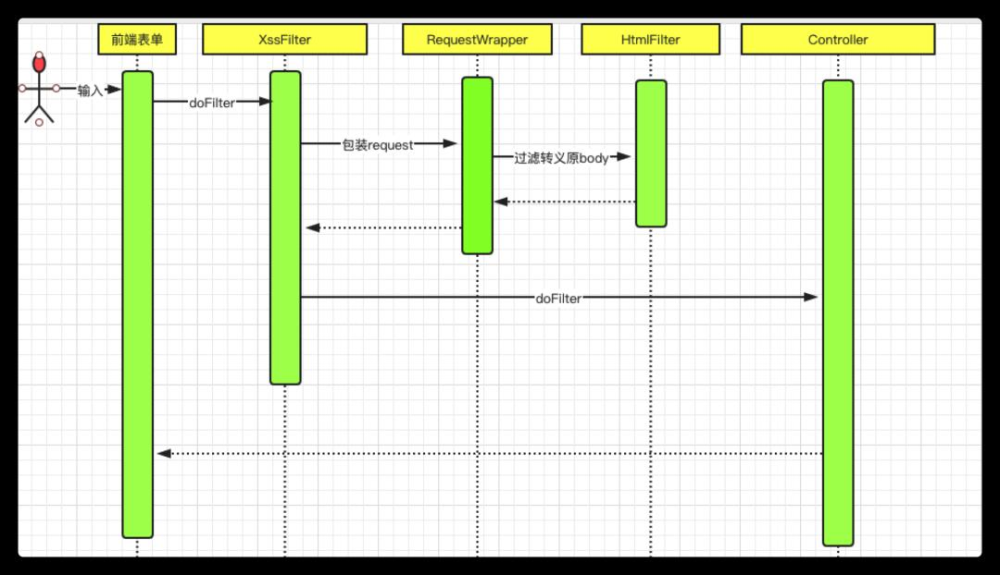
说明:
- 如图上图,通过增添XssFilter拦截用户提交的URL参数,并进行相关的转义和黑名单排除,从而完成相关的业务逻辑。
- mica-xss防护XSS攻击的整个过程中,最核心的部分就是通过包装用户的原始请求,创建新的 requestwrapper(请求包装器) 保证请求流在后面的流程可以重复读。
4.1、MICA-XSS 源码
链接:https://gitee.com/596392912/mica/tree/master/mica-xss文章来源:https://www.toymoban.com/news/detail-547809.html
mica-xss 源码文章来源地址https://www.toymoban.com/news/detail-547809.html
到了这里,关于SpringBoot 防护XSS攻击的文章就介绍完了。如果您还想了解更多内容,请在右上角搜索TOY模板网以前的文章或继续浏览下面的相关文章,希望大家以后多多支持TOY模板网!