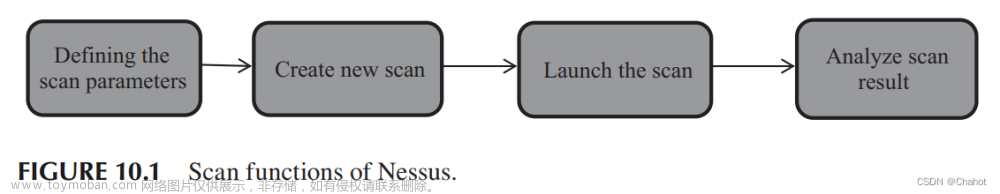
用Nessus professional扫描某个Linux终端,发现如下高危漏洞:
PCI DSS Compliance : Remote Access Software Has Been Detected
Description
Due to increased risk to the cardholder data environment when remote access software is present, 1) justify the business need for this software to the ASV and confirm it is implemented securely, or 2) confirm it is disabled/ removed. Consult your ASV if you have questions about this Special Note.
Output
PCI DSS Compliance : Scan Interference
Description
Interference from either the network or the host did not allow the scan to fulfill the PCI DSS scan validation requirements. This report is insufficient to certify this server. There may be a firewall, IDS or other software blocking Nessus from scanning.
Solution
- Adjust Nessus scan settings to improve performance.
- Whitelist the Nessus scanner for any IDS or Firewall which may be blocking the scan.Output
Samba 4.9.x < 4.9.13 / 4.10.x < 4.10.8 / 4.11.0rc3 Security Bypass (CVE-2019-10197)
Description
The version of Samba running on the remote host is 4.9.x prior to 4.9.13, 4.10.x prior to 4.10.3.8, or 4.11.x prior to 4.11.0rc3. It is, therefore, affected by security bypass vulnerability.
An unauthenticated attacker could use this flaw to escape the shared directory and access the contents of directories outside the share.
Note that Nessus has not tested for this issue but has instead relied only on the application's self-reported version number.Solution
Upgrade to Samba version 4.9.13 / 4.10.8 / 4.11.0rc3 or later.
See Also
Samba - Security Announcement Archive
Output
PCI DSS compliance
Description
The remote host is vulnerable to one or more conditions that are considered to be 'automatic failures' according to the PCI DSS Approved Scanning Vendors Program Guide (version 3.1). These failures include one or more of the following :
- Vulnerabilities with a CVSS base score greater than or equal to 4.0
- Unsupported operating systems
- Internet reachable database servers (must validate whether cardholder data is stored)
- Presence of built-in or default accounts
- Unrestricted DNS Zone transfers
- Unvalidated parameters leading to SQL injection attacks
- Cross-Site Scripting (XSS) flaws
- Directory traversal vulnerabilities
- HTTP response splitting/header injection
- Detection of backdoor applications (malware, trojan horses, rootkits, backdoors)
- Use of older, insecure SSL/TLS versions (TLS v1.2 is the minimum standard)
- Use of anonymous key exchange protocols (such as anonymous Diffie-Hellman in SSL/TLS)
- Scan Interference
Details of the failed items may be found in the 'Output' section of this plugin result. These vulnerabilities and/or failure conditions will have to be corrected before you are able to submit your scan results for validation by Tenable to meet your quarterly external scanning requirements.
If you are conducting this scan via Tenable.io and either disagree with any of the results, believe there are false-positives, or must rely on compensating controls to mitigate the vulnerability then you may proceed with submitting this report to our PCI-ASV Workbench by clicking on 'Submit for PCI'. You may login to the Tenable PCI-ASV Workbench in Tenable.io and dispute or provide mitigation evidence for each of the residual findings.See Also
https://www.pcisecuritystandards.org
Output
这些漏洞其实都和port有关。Samba应用也是运行在端口139. 一个简单粗暴的方法就是把相关的端口都关闭。这个可以通过iptables命令来实现。如运行如下规则:
$iptables -I INPUT -p tcp --dport 139 -j DROP
这条命令是在INPUT chain的顶部加上一条过滤规则(rule),这条规则把目的地址端口为139的,协议是tcp的所有进来的包都忽略掉(DROP),也就是没有回应。注意,使用 -I 而不是 -A,因为 -I是放在顶部,-A是放在底部,而IPTABLES的顶部优先级高于底部,即以顶部的规则为准。
这时候再运行$iptables -L -v可以在INPUT chain的顶部看到如下记录:
0 0 DROP tcp -- any any anywhere anywhere tcp dpt:netbios-ssn netbios-ssn的端口就是139.
再次扫描,发现该漏洞没有了。注意,如果还要对IPv6进行扫描的话,要把IPv6的过滤规则也放上去,即:ip6tables -I INPUT -p tcp --dport %d -j DROP。
除此之外,为了避免可能的其它漏洞报告,需要把IP forwarding功能禁掉。命令为:
$echo 0 > /proc/sys/net/ipv4/ip_forward
$echo 0 > /proc/sys/net/ipv6/conf/all/forwarding
现在把扫描结果张贴如下:
 文章来源:https://www.toymoban.com/news/detail-569682.html
文章来源:https://www.toymoban.com/news/detail-569682.html
注意,本文提到的方法简单粗暴。因为把这些端口禁了后,相关的应用也无法正常进行。但是这种方法可以让安全测试过关,如果客户允许这样做。现实是所有通过的厂商都是这么做的。因为安全测试本来就是有很多false positive。如果完全按照Nessus扫描结果,终端的正常业务根本无法开展。但是厂商在客户面前都很弱势。为了面子上过得去,就用这种方式,大家达成默契即可。 文章来源地址https://www.toymoban.com/news/detail-569682.html
到了这里,关于一种解决Nessus扫描中有关端口漏洞的简单方法的文章就介绍完了。如果您还想了解更多内容,请在右上角搜索TOY模板网以前的文章或继续浏览下面的相关文章,希望大家以后多多支持TOY模板网!