前言
在网络安全等级保护中,对日志有着一系列的要求,通常以部署日志审计系统来满足等保的要求,此处我们选择syslog来实现日志的集中收集,统一管理。
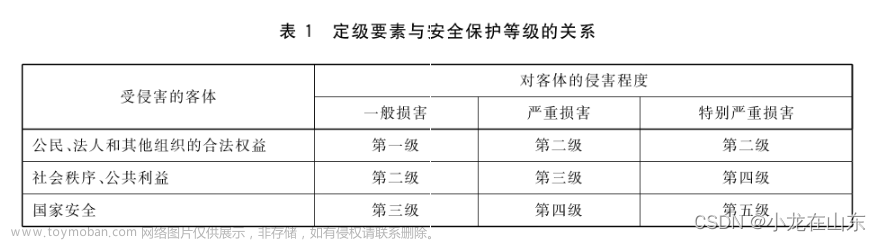
等级保护要求
在这里我们主要目标是满足安全区域边界、安全管理中心里的下面两条的要求。其中安全管理中心的日志保存时间大于6个月是硬性的时间要求。

拓扑描述

如图所示,LogServer的IP地址为192.168.152.132/24,现有交换机、路由器、防火墙各一台,以及两台WebServer,一台Windows,一台Linux。现要求配置所有的设备,使得交换机、路由器、防火墙、WebServer的日志都上传到LogServer中。
配置步骤
1、配置服务端
首先创建一台CentOS7主机,最小化安装的情况下也是带有rsyslog服务的。可以为日志文件单独准备一块大容量硬盘,在安装系统的时候单独划分/var/log目录为一个分区。修改rsyslog的配置文件/etc/rsyslog.conf如下:

然后修改/etc/sysconfig/rsyslog如下:
添加防火墙规则:firewall-cmd --add-port=514/udp,至此,服务端的配置就完成了。
2、配置客户端
2.1 防火墙
首先为边界防火墙端口配置IP:
<SRG>sys
[SRG]sysname BJ-FW01
[BJ-FW01]interface GigabitEthernet 0/0/8
[BJ-FW01-GigabitEthernet0/0/8]ip address 192.168.152.140 24
[BJ-FW01-GigabitEthernet0/0/8]quit
[BJ-FW01]interface GigabitEthernet 0/0/1
[BJ-FW01-GigabitEthernet0/0/1]ip address 192.168.151.1 24
[BJ-FW01-GigabitEthernet0/0/1]quit
因为日志服务器在区域逻辑上来说是属于信任区的,所以我们把日志服务器所在端口加入防火墙的trust区域,这样才能进行数据通信:
[BJ-FW01]firewall zone trust
[BJ-FW01-zone-trust]add interface GigabitEthernet 0/0/8
[BJ-FW01-zone-trust]quit
此时我们在防火墙上ping日志服务器:
[BJ-FW01]ping 192.168.152.132
17:18:45 2022/01/29
PING 192.168.152.132: 56 data bytes, press CTRL_C to break
Reply from 192.168.152.132: bytes=56 Sequence=1 ttl=64 time=390 ms
Reply from 192.168.152.132: bytes=56 Sequence=2 ttl=64 time=340 ms
Reply from 192.168.152.132: bytes=56 Sequence=3 ttl=64 time=300 ms
Reply from 192.168.152.132: bytes=56 Sequence=4 ttl=64 time=120 ms
Reply from 192.168.152.132: bytes=56 Sequence=5 ttl=64 time=110 ms
--- 192.168.152.132 ping statistics ---
5 packet(s) transmitted
5 packet(s) received
0.00% packet loss
round-trip min/avg/max = 110/252/390 ms
由上ping的结果可知从防火墙到日志服务器的数据链路已经做好了,接下来我们配置防火墙使其把日志上传到日志服务器:
[BJ-FW01]info-center enable
[BJ-FW01]info-center channel 6 name LogServer
[BJ-FW01]info-center loghost 192.168.152.132 channel LogServer
[BJ-FW01]info-center source CMD channel LogServer log level debugging
[BJ-FW01]info-center loghost source GigabitEthernet 0/0/8
(由于华为防火墙的默认日志时间戳类型导致SYSLOG不能正确的以主机名区分,所以需要修改一下日志的时间戳类型)
[BJ-FW01]info-center timestamp debugging short-date
[BJ-FW01]info-center timestamp log short-date
测试
我们在防火墙上执行一下命令,然后在服务器上看是否收集到了防火墙发送的日志:
防火墙:
<BJ-FW01>ping 192.168.152.132
14:42:23 2022/02/09
PING 192.168.152.132: 56 data bytes, press CTRL_C to break
Reply from 192.168.152.132: bytes=56 Sequence=1 ttl=64 time=270 ms
Reply from 192.168.152.132: bytes=56 Sequence=2 ttl=64 time=200 ms
Reply from 192.168.152.132: bytes=56 Sequence=3 ttl=64 time=170 ms
Reply from 192.168.152.132: bytes=56 Sequence=4 ttl=64 time=90 ms
Reply from 192.168.152.132: bytes=56 Sequence=5 ttl=64 time=80 ms
--- 192.168.152.132 ping statistics ---
5 packet(s) transmitted
5 packet(s) received
0.00% packet loss
round-trip min/avg/max = 80/162/270 ms
日志服务器:
[root@LogServer log]# tail BJ-FW01/%%01SHELL.log
2022-02-09T06:20:08+08:00 BJ-FW01 %%01SHELL/5/CMDRECORD(l): task:co0 ip:** user:** vrf:public command:info-center timestamp log short-date.
2022-02-09T06:24:45+08:00 BJ-FW01 %%01SHELL/6/DISPLAY_CMDRECORD(l): task:co0 ip:** user:** vrf:public command:display current-configuration.
2022-02-09T06:41:23+08:00 BJ-FW01 %%01SHELL/4/LOGOUT(l): vrf:public user:Console logout from con0
2022-02-09T06:42:15+08:00 BJ-FW01 %%01SHELL/4/LOGIN(l): vrf:public user:Console login from con0
2022-02-09T06:42:23+08:00 BJ-FW01 %%01SHELL/5/CMDRECORD(l): task:co0 ip:** user:** vrf:public command:ping 192.168.152.132.
可以看到,我们在LogServer的/var/log/BJ-FW01/%%01SHELL.log文件中找到了刚才我们在防火墙上执行的ping 192.168.152.132命令记录。
2.2 路由器
首先为路由器的端口配置IP:
<Huawei>sys
[Huawei]sysname CORE-RT-01
[CORE-RT-01]interface GigabitEthernet0/0/0
[CORE-RT-01-GigabitEthernet0/0/0]ip address 192.168.151.2 24
[CORE-RT-01-GigabitEthernet0/0/0]quit
[CORE-RT-01]interface GigabitEthernet0/0/2
[CORE-RT-01-GigabitEthernet0/0/2]ip address 192.168.150.1 24
[CORE-RT-01-GigabitEthernet0/0/2]quit
为路由器配置路由使其能够和日志服务器通信:
[CORE-RT-01]ip route-static 192.168.152.0 24 192.168.151.1
[CORE-RT-01]ping 192.168.152.140
PING 192.168.152.140: 56 data bytes, press CTRL_C to break
Reply from 192.168.152.140: bytes=56 Sequence=1 ttl=255 time=40 ms
Reply from 192.168.152.140: bytes=56 Sequence=2 ttl=255 time=140 ms
Reply from 192.168.152.140: bytes=56 Sequence=3 ttl=255 time=50 ms
Reply from 192.168.152.140: bytes=56 Sequence=4 ttl=255 time=360 ms
Reply from 192.168.152.140: bytes=56 Sequence=5 ttl=255 time=80 ms
--- 192.168.152.140 ping statistics ---
5 packet(s) transmitted
5 packet(s) received
0.00% packet loss
round-trip min/avg/max = 40/134/360 ms
[CORE-RT-01]ping 192.168.152.132
PING 192.168.152.132: 56 data bytes, press CTRL_C to break
Request time out
Request time out
Request time out
Request time out
Request time out
--- 192.168.152.132 ping statistics ---
5 packet(s) transmitted
0 packet(s) received
100.00% packet loss
不知道为什么,能ping通192.168.152.140却ping不通192.168.152.132,如果有哪位读者知道,还望能够评论告知一下。
接下来我们配置路由器使其把日志上传到日志服务器:
[CORE-RT-01]info-center enable
[CORE-RT-01]info-center channel 6 name LogServer
[CORE-RT-01]info-center loghost 192.168.152.132 channel LogServer
[CORE-RT-01]info-center source CMD channel LogServer log level debugging
[CORE-RT-01]info-center loghost source GigabitEthernet 0/0/0
[root@LogServer CORE-RT-01]# cat %%01SHELL.log
2022-02-09T17:49:13+08:00 CORE-RT-01 %%01SHELL/5/LOGIN(l)[63]: Console login from con0.
2022-02-09T17:49:15+08:00 CORE-RT-01 %%01SHELL/5/CMDRECORD(l)[64]: Record command information. (Task=co0 , Ip=**, User=**, Command="system-view")
2022-02-09T17:49:18+08:00 CORE-RT-01 %%01SHELL/6/DISPLAY_CMDRECORD(l)[65]: Record display command information. (Task=co0 , Ip=**, User=**, Command="display current-configuration")
2022-02-09T17:59:19+08:00 CORE-RT-01 %%01SHELL/5/TIMEOUT(l)[66]: Console login from con0 is time out.
2022-02-09T17:59:19+08:00 CORE-RT-01 %%01SHELL/5/LOGOUT(l)[67]: Console logout from con0.
2022-02-09T17:59:19+08:00 CORE-RT-01 %%01SHELL/5/CMDRECORD(l)[68]: Record command information. (Task=co0 , Ip=**, User=**, Command="undo debugging all")
2022-02-09T18:15:22+08:00 CORE-RT-01 %%01SHELL/5/LOGIN(l)[69]: Console login from con0.
2022-02-09T18:15:23+08:00 CORE-RT-01 %%01SHELL/5/CMDRECORD(l)[70]: Record command information. (Task=co0 , Ip=**, User=**, Command="system-view")
2022-02-09T18:17:05+08:00 CORE-RT-01 %%01SHELL/6/DISPLAY_CMDRECORD(l)[71]: Record display command information. (Task=co0 , Ip=**, User=**, Command="display logbuffer")
我们在日志服务器里已经能够看到路由器上传的日志了,说明路由器到日志服务器的通信是正常的了,但却不能ping通,不知道是为啥。还有,路由器上传上来的日志时间比实际的时间快了8个小时。
路由器时间:
[CORE-RT-01]dis clock
2022-02-08 16:09:10-08:00
Tuesday
Time Zone(China-Standard-Time) : UTC-08:00
日志服务器时间:
[root@LogServer ~]# date
Tue Feb 8 16:17:56 CST 2022
2.3 交换机
我们配置交换机:
[Huawei]sysname CORE-SW-01
[CORE-SW-01]interface GigabitEthernet 0/0/1
[CORE-SW-01-GigabitEthernet0/0/1]port link-type access
[CORE-SW-01-GigabitEthernet0/0/1]quit
[CORE-SW-01]vlan 109
[CORE-SW-01-vlan109]port GigabitEthernet 0/0/1
[CORE-SW-01-vlan109]quit
[CORE-SW-01]interface Vlanif 109
[CORE-SW-01-Vlanif109]ip address 192.168.150.2 24
[CORE-SW-01-Vlanif109]quit
[CORE-SW-01]ip route-static 192.168.151.0 24 192.168.150.1
[CORE-SW-01]ip route-static 192.168.152.0 24 192.168.150.1
[CORE-SW-01]info-center enable
[CORE-SW-01]info-center channel 6 name LogServer
[CORE-SW-01]info-center loghost 192.168.152.132 channel LogServer
[CORE-SW-01]info-center source CMD channel LogServer log level debugging
[CORE-SW-01]info-center loghost source Vlanif 109
此时我们在日志服务器已经能够查看到来自交换机的日志了。
[root@LogServer CORE-SW-01]# cat %%01SHELL.log
2022-02-09T18:23:43+08:00 CORE-SW-01 %%01SHELL/5/LOGIN(l)[169]: Console login from con0.
2022-02-09T18:23:47+08:00 CORE-SW-01 %%01SHELL/5/CMDRECORD(l)[170]: Record command information. (Task=co0 , Ip=**, User=**, Command="system-view")
2022-02-09T18:25:03+08:00 CORE-SW-01 %%01SHELL/6/DISPLAY_CMDRECORD(l)[171]: Record display command information. (Task=co0 , Ip=**, User=**, Command="display current-configuration")
2022-02-09T18:35:05+08:00 CORE-SW-01 %%01SHELL/5/TIMEOUT(l)[172]: Console login from con0 is time out.
2022-02-09T18:35:05+08:00 CORE-SW-01 %%01SHELL/5/LOGOUT(l)[173]: Console logout from con0.
2022-02-09T18:35:05+08:00 CORE-SW-01 %%01SHELL/5/CMDRECORD(l)[174]: Record command information. (Task=co0 , Ip=**, User=**, Command="undo debugging all")
2022-02-09T22:57:19+08:00 CORE-SW-01 %%01SHELL/5/LOGIN(l)[172]: Console login from con0.
2022-02-09T22:57:22+08:00 CORE-SW-01 %%01SHELL/5/CMDRECORD(l)[173]: Record command information. (Task=co0 , Ip=**, User=**, Command="system-view")
2022-02-09T22:57:24+08:00 CORE-SW-01 %%01SHELL/6/DISPLAY_CMDRECORD(l)[174]: Record display command information. (Task=co0 , Ip=**, User=**, Command="display current-configuration")
2.5 Linux主机
Linux主机中,配置/etc/rsyslog.conf如下:
对于Linux主机,按照等级保护2.0中对于安全计算环境的安全审计来说,有如下的要求:

要求对重要的用户行为进行审计,从我个人的观点来说,用户操作绝对可以算的上是重要的用户行为了,那么,在Linux里要对用户的操作进行审计,就用Audit了,所以我们配置一下Audit的审计规则文件/etc/audit/rules.d/audit.rules如下:
上面的配置里,我们把SSH的配置文件加入到了审计的规则里,任何用户对ssh_config进行写入和修改属性的操作都将被审计,这里可以自由发挥,把你认为的重要文件加入进去以进行审计。
题外话,Linux审计包根据各种认证标准提供了一组预配置的审计规则文件:/usr/share/doc/audit-version/rules

其中:
nispom.rules——符合《国家工业安全方案操作手册》第八章要求的审计规则配置;
capp.rules——满足[受控访问保护配置文件(CAPP)]设置要求的审计规则配置(http://www.niap-ccevs.org/pp/pp_os_ca_v1.d.pdf)
lspp.rules——符合[标记安全保护配置文件(LSPP)]设置要求的审计规则配置(http://www.commoncriteriaportal.org/files/ppfiles/lspp.pdf)
stig.rules——符合安全技术实施指南(STIG)规定要求的审计规则配置
配置好审计规则后,接下来我们配置将Audit的审计日志发送到日志服务器上,配置/etc/audisp/plugins.d/syslog.conf如下:
active = yes
direction = out
path = builtin_syslog
type = builtin
args = LOG_SYSLOG
format = string

配置完后我们在WebServer上执行一下ls命令,然后在日志服务器上看能否收到WebServer发过来的操作日志:
WebServer:
[root@WebServer ~]# ls
anaconda-ks.cfg
[root@WebServer ~]# date
2022年 02月 13日 星期日 18:43:37 CST
日志服务器:
2022-02-13T18:43:35+08:00 WebServer audispd: node=WebServer type=SYSCALL msg=audit(1644749015.458:545): arch=c000003e syscall=59 success=yes exit=0 a0=cae310 a1=ca8f20 a2=caf910 a3=7fff2daedb20 items=2 ppid=1259 pid=1281 auid=0 uid=0 gid=0 euid=0 suid=0 fsuid=0 egid=0 sgid=0 fsgid=0 tty=pts0 ses=1 comm="ls" exe="/usr/bin/ls" subj=unconfined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023 key=(null)
2022-02-13T18:43:35+08:00 WebServer audispd: node=WebServer type=EXECVE msg=audit(1644749015.458:545): argc=2 a0="ls" a1="--color=auto"
2022-02-13T18:43:35+08:00 WebServer audispd: node=WebServer type=CWD msg=audit(1644749015.458:545): cwd="/root"
2022-02-13T18:43:35+08:00 WebServer audispd: node=WebServer type=PATH msg=audit(1644749015.458:545): item=0 name="/usr/bin/ls" inode=50502987 dev=fd:00 mode=0100755 ouid=0 ogid=0 rdev=00:00 obj=system_u:object_r:bin_t:s0 objtype=NORMAL cap_fp=0000000000000000 cap_fi=0000000000000000 cap_fe=0 cap_fver=0
2022-02-13T18:43:35+08:00 WebServer audispd: node=WebServer type=PATH msg=audit(1644749015.458:545): item=1 name="/lib64/ld-linux-x86-64.so.2" inode=75378 dev=fd:00 mode=0100755 ouid=0 ogid=0 rdev=00:00 obj=system_u:object_r:ld_so_t:s0 objtype=NORMAL cap_fp=0000000000000000 cap_fi=0000000000000000 cap_fe=0 cap_fver=0
2022-02-13T18:43:35+08:00 WebServer audispd: node=WebServer type=PROCTITLE msg=audit(1644749015.458:545): proctitle=6C73002D2D636F6C6F723D6175746F
2022-02-13T18:43:35+08:00 WebServer audispd: node=WebServer type=SYSCALL msg=audit(1644749015.458:545): arch=c000003e syscall=59 success=yes exit=0 a0=cae310 a1=ca8f20 a2=caf910 a3=7fff2daedb20 items=2 ppid=1259 pid=1281 auid=0 uid=0 gid=0 euid=0 suid=0 fsuid=0 egid=0 sgid=0 fsgid=0 tty=pts0 ses=1 comm="ls" exe="/usr/bin/ls" subj=unconfined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023 key=(null)
2022-02-13T18:43:35+08:00 WebServer audispd: node=WebServer type=EXECVE msg=audit(1644749015.458:545): argc=2 a0="ls" a1="--color=auto"
2022-02-13T18:43:35+08:00 WebServer audispd: node=WebServer type=CWD msg=audit(1644749015.458:545): cwd="/root"
2022-02-13T18:43:35+08:00 WebServer audispd: node=WebServer type=PATH msg=audit(1644749015.458:545): item=0 name="/usr/bin/ls" inode=50502987 dev=fd:00 mode=0100755 ouid=0 ogid=0 rdev=00:00 obj=system_u:object_r:bin_t:s0 objtype=NORMAL cap_fp=0000000000000000 cap_fi=0000000000000000 cap_fe=0 cap_fver=0
2022-02-13T18:43:35+08:00 WebServer audispd: node=WebServer type=PATH msg=audit(1644749015.458:545): item=1 name="/lib64/ld-linux-x86-64.so.2" inode=75378 dev=fd:00 mode=0100755 ouid=0 ogid=0 rdev=00:00 obj=system_u:object_r:ld_so_t:s0 objtype=NORMAL cap_fp=0000000000000000 cap_fi=0000000000000000 cap_fe=0 cap_fver=0
2022-02-13T18:43:35+08:00 WebServer audispd: node=WebServer type=PROCTITLE msg=audit(1644749015.458:545): proctitle=6C73002D2D636F6C6F723D6175746F
2022-02-13T18:43:37+08:00 WebServer audispd: node=WebServer type=SYSCALL msg=audit(1644749017.183:546): arch=c000003e syscall=59 success=yes exit=0 a0=ca8e60 a1=cb0660 a2=caf910 a3=7fff2daedb20 items=2 ppid=1259 pid=1282 auid=0 uid=0 gid=0 euid=0 suid=0 fsuid=0 egid=0 sgid=0 fsgid=0 tty=pts0 ses=1 comm="date" exe="/usr/bin/date" subj=unconfined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023 key=(null)
2022-02-13T18:43:37+08:00 WebServer audispd: node=WebServer type=EXECVE msg=audit(1644749017.183:546): argc=1 a0="date"
2022-02-13T18:43:37+08:00 WebServer audispd: node=WebServer type=CWD msg=audit(1644749017.183:546): cwd="/root"
2022-02-13T18:43:37+08:00 WebServer audispd: node=WebServer type=PATH msg=audit(1644749017.183:546): item=0 name="/usr/bin/date" inode=50493139 dev=fd:00 mode=0100755 ouid=0 ogid=0 rdev=00:00 obj=system_u:object_r:bin_t:s0 objtype=NORMAL cap_fp=0000000000000000 cap_fi=0000000000000000 cap_fe=0 cap_fver=0
2022-02-13T18:43:37+08:00 WebServer audispd: node=WebServer type=PATH msg=audit(1644749017.183:546): item=1 name="/lib64/ld-linux-x86-64.so.2" inode=75378 dev=fd:00 mode=0100755 ouid=0 ogid=0 rdev=00:00 obj=system_u:object_r:ld_so_t:s0 objtype=NORMAL cap_fp=0000000000000000 cap_fi=0000000000000000 cap_fe=0 cap_fver=0
2022-02-13T18:43:37+08:00 WebServer audispd: node=WebServer type=PROCTITLE msg=audit(1644749017.183:546): proctitle="date"
2022-02-13T18:43:37+08:00 WebServer audispd: node=WebServer type=SYSCALL msg=audit(1644749017.183:546): arch=c000003e syscall=59 success=yes exit=0 a0=ca8e60 a1=cb0660 a2=caf910 a3=7fff2daedb20 items=2 ppid=1259 pid=1282 auid=0 uid=0 gid=0 euid=0 suid=0 fsuid=0 egid=0 sgid=0 fsgid=0 tty=pts0 ses=1 comm="date" exe="/usr/bin/date" subj=unconfined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023 key=(null)
2022-02-13T18:43:37+08:00 WebServer audispd: node=WebServer type=EXECVE msg=audit(1644749017.183:546): argc=1 a0="date"
2022-02-13T18:43:37+08:00 WebServer audispd: node=WebServer type=CWD msg=audit(1644749017.183:546): cwd="/root"
2022-02-13T18:43:37+08:00 WebServer audispd: node=WebServer type=PATH msg=audit(1644749017.183:546): item=0 name="/usr/bin/date" inode=50493139 dev=fd:00 mode=0100755 ouid=0 ogid=0 rdev=00:00 obj=system_u:object_r:bin_t:s0 objtype=NORMAL cap_fp=0000000000000000 cap_fi=0000000000000000 cap_fe=0 cap_fver=0
2022-02-13T18:43:37+08:00 WebServer audispd: node=WebServer type=PATH msg=audit(1644749017.183:546): item=1 name="/lib64/ld-linux-x86-64.so.2" inode=75378 dev=fd:00 mode=0100755 ouid=0 ogid=0 rdev=00:00 obj=system_u:object_r:ld_so_t:s0 objtype=NORMAL cap_fp=0000000000000000 cap_fi=0000000000000000 cap_fe=0 cap_fver=0
2022-02-13T18:43:37+08:00 WebServer audispd: node=WebServer type=PROCTITLE msg=audit(1644749017.183:546): proctitle="date"
我们在WebServer上新建一个用户,再测试一下:
WebServer:
[root@WebServer ~]# useradd shenji
[root@WebServer ~]# passwd shenji
更改用户 shenji 的密码 。
新的 密码:
无效的密码: 密码未通过字典检查 - 它基于字典单词
重新输入新的 密码:
passwd:所有的身份验证令牌已经成功更新。
[root@WebServer ~]# cat /etc/passwd | grep shenji
shenji:x:1000:1000::/home/shenji:/bin/bash
shenji的UID和GID都是1000,我们在日志服务器搜索一下uid为1000的用户看一下有没有日志:
日志服务器:文章来源:https://www.toymoban.com/news/detail-594812.html
[root@LogServer ~]# cat /var/log/WebServer/audispd.log | grep uid=1000
2022-02-13T18:50:15+08:00 WebServer audispd: node=WebServer type=SYSCALL msg=audit(1644749415.377:569): arch=c000003e syscall=59 success=yes exit=0 a0=560c230b2210 a1=560c230b3ea0 a2=7ffed8217ae0 a3=2 items=2 ppid=1296 pid=1297 auid=0 uid=1000 gid=1000 euid=1000 suid=1000 fsuid=1000 egid=1000 sgid=1000 fsgid=1000 tty=pts0 ses=1 comm="bash" exe="/usr/bin/bash" subj=unconfined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023 key=(null)
2022-02-13T18:50:15+08:00 WebServer audispd: node=WebServer type=SYSCALL msg=audit(1644749415.377:569): arch=c000003e syscall=59 success=yes exit=0 a0=560c230b2210 a1=560c230b3ea0 a2=7ffed8217ae0 a3=2 items=2 ppid=1296 pid=1297 auid=0 uid=1000 gid=1000 euid=1000 suid=1000 fsuid=1000 egid=1000 sgid=1000 fsgid=1000 tty=pts0 ses=1 comm="bash" exe="/usr/bin/bash" subj=unconfined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023 key=(null)
2022-02-13T18:50:15+08:00 WebServer audispd: node=WebServer type=SYSCALL msg=audit(1644749415.380:570): arch=c000003e syscall=59 success=yes exit=0 a0=19c96b0 a1=19c9710 a2=19c9350 a3=7ffc46d89d60 items=2 ppid=1298 pid=1299 auid=0 uid=1000 gid=1000 euid=1000 suid=1000 fsuid=1000 egid=1000 sgid=1000 fsgid=1000 tty=pts0 ses=1 comm="id" exe="/usr/bin/id" subj=unconfined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023 key=(null)
2022-02-13T18:50:15+08:00 WebServer audispd: node=WebServer type=SYSCALL msg=audit(1644749415.380:570): arch=c000003e syscall=59 success=yes exit=0 a0=19c96b0 a1=19c9710 a2=19c9350 a3=7ffc46d89d60 items=2 ppid=1298 pid=1299 auid=0 uid=1000 gid=1000 euid=1000 suid=1000 fsuid=1000 egid=1000 sgid=1000 fsgid=1000 tty=pts0 ses=1 comm="id" exe="/usr/bin/id" subj=unconfined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023 key=(null)
2022-02-13T18:50:15+08:00 WebServer audispd: node=WebServer type=SYSCALL msg=audit(1644749415.383:571): arch=c000003e syscall=59 success=yes exit=0 a0=19c9590 a1=19c97b0 a2=19c9350 a3=7ffc46d89d60 items=2 ppid=1300 pid=1301 auid=0 uid=1000 gid=1000 euid=1000 suid=1000 fsuid=1000 egid=1000 sgid=1000 fsgid=1000 tty=pts0 ses=1 comm="id" exe="/usr/bin/id" subj=unconfined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023 key=(null)
2022-02-13T18:50:15+08:00 WebServer audispd: node=WebServer type=SYSCALL msg=audit(1644749415.383:571): arch=c000003e syscall=59 success=yes exit=0 a0=19c9590 a1=19c97b0 a2=19c9350 a3=7ffc46d89d60 items=2 ppid=1300 pid=1301 auid=0 uid=1000 gid=1000 euid=1000 suid=1000 fsuid=1000 egid=1000 sgid=1000 fsgid=1000 tty=pts0 ses=1 comm="id" exe="/usr/bin/id" subj=unconfined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023 key=(null)
2022-02-13T18:50:15+08:00 WebServer audispd: node=WebServer type=SYSCALL msg=audit(1644749415.385:572): arch=c000003e syscall=59 success=yes exit=0 a0=19d0cb0 a1=19d0ce0 a2=19c9650 a3=7ffc46d89e60 items=3 ppid=1297 pid=1302 auid=0 uid=1000 gid=1000 euid=1000 suid=1000 fsuid=1000 egid=1000 sgid=1000 fsgid=1000 tty=pts0 ses=1 comm="grepconf.sh" exe="/usr/bin/bash" subj=unconfined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023 key=(null)
2022-02-13T18:50:15+08:00 WebServer audispd: node=WebServer type=SYSCALL msg=audit(1644749415.385:572): arch=c000003e syscall=59 success=yes exit=0 a0=19d0cb0 a1=19d0ce0 a2=19c9650 a3=7ffc46d89e60 items=3 ppid=1297 pid=1302 auid=0 uid=1000 gid=1000 euid=1000 suid=1000 fsuid=1000 egid=1000 sgid=1000 fsgid=1000 tty=pts0 ses=1 comm="grepconf.sh" exe="/usr/bin/bash" subj=unconfined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023 key=(null)
2022-02-13T18:50:15+08:00 WebServer audispd: node=WebServer type=SYSCALL msg=audit(1644749415.388:573): arch=c000003e syscall=59 success=yes exit=0 a0=225fd40 a1=225e410 a2=225d540 a3=7ffe38db7820 items=2 ppid=1302 pid=1303 auid=0 uid=1000 gid=1000 euid=1000 suid=1000 fsuid=1000 egid=1000 sgid=1000 fsgid=1000 tty=pts0 ses=1 comm="grep" exe="/usr/bin/grep" subj=unconfined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023 key=(null)
2022-02-13T18:50:15+08:00 WebServer audispd: node=WebServer type=SYSCALL msg=audit(1644749415.388:573): arch=c000003e syscall=59 success=yes exit=0 a0=225fd40 a1=225e410 a2=225d540 a3=7ffe38db7820 items=2 ppid=1302 pid=1303 auid=0 uid=1000 gid=1000 euid=1000 suid=1000 fsuid=1000 egid=1000 sgid=1000 fsgid=1000 tty=pts0 ses=1 comm="grep" exe="/usr/bin/grep" subj=unconfined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023 key=(null)
2022-02-13T18:50:15+08:00 WebServer audispd: node=WebServer type=SYSCALL msg=audit(1644749415.391:574): arch=c000003e syscall=59 success=yes exit=0 a0=19e6420 a1=19e6600 a2=19c9650 a3=7ffc46d88e20 items=2 ppid=1304 pid=1305 auid=0 uid=1000 gid=1000 euid=1000 suid=1000 fsuid=1000 egid=1000 sgid=1000 fsgid=1000 tty=pts0 ses=1 comm="tty" exe="/usr/bin/tty" subj=unconfined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023 key=(null)
2022-02-13T18:50:15+08:00 WebServer audispd: node=WebServer type=SYSCALL msg=audit(1644749415.391:574): arch=c000003e syscall=59 success=yes exit=0 a0=19e6420 a1=19e6600 a2=19c9650 a3=7ffc46d88e20 items=2 ppid=1304 pid=1305 auid=0 uid=1000 gid=1000 euid=1000 suid=1000 fsuid=1000 egid=1000 sgid=1000 fsgid=1000 tty=pts0 ses=1 comm="tty" exe="/usr/bin/tty" subj=unconfined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023 key=(null)
2022-02-13T18:50:15+08:00 WebServer audispd: node=WebServer type=SYSCALL msg=audit(1644749415.393:575): arch=c000003e syscall=59 success=yes exit=0 a0=19e6520 a1=19e65c0 a2=19c9650 a3=7ffc46d88e20 items=2 ppid=1304 pid=1306 auid=0 uid=1000 gid=1000 euid=1000 suid=1000 fsuid=1000 egid=1000 sgid=1000 fsgid=1000 tty=pts0 ses=1 comm="tput" exe="/usr/bin/tput" subj=unconfined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023 key=(null)
2022-02-13T18:50:15+08:00 WebServer audispd: node=WebServer type=SYSCALL msg=audit(1644749415.393:575): arch=c000003e syscall=59 success=yes exit=0 a0=19e6520 a1=19e65c0 a2=19c9650 a3=7ffc46d88e20 items=2 ppid=1304 pid=1306 auid=0 uid=1000 gid=1000 euid=1000 suid=1000 fsuid=1000 egid=1000 sgid=1000 fsgid=1000 tty=pts0 ses=1 comm="tput" exe="/usr/bin/tput" subj=unconfined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023 key=(null)
2022-02-13T18:50:15+08:00 WebServer audispd: node=WebServer type=SYSCALL msg=audit(1644749415.395:576): arch=c000003e syscall=59 success=yes exit=0 a0=19e5f90 a1=19d0a70 a2=19c9650 a3=7ffc46d893e0 items=2 ppid=1307 pid=1308 auid=0 uid=1000 gid=1000 euid=1000 suid=1000 fsuid=1000 egid=1000 sgid=1000 fsgid=1000 tty=pts0 ses=1 comm="dircolors" exe="/usr/bin/dircolors" subj=unconfined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023 key=(null)
2022-02-13T18:50:15+08:00 WebServer audispd: node=WebServer type=SYSCALL msg=audit(1644749415.395:576): arch=c000003e syscall=59 success=yes exit=0 a0=19e5f90 a1=19d0a70 a2=19c9650 a3=7ffc46d893e0 items=2 ppid=1307 pid=1308 auid=0 uid=1000 gid=1000 euid=1000 suid=1000 fsuid=1000 egid=1000 sgid=1000 fsgid=1000 tty=pts0 ses=1 comm="dircolors" exe="/usr/bin/dircolors" subj=unconfined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023 key=(null)
2022-02-13T18:50:15+08:00 WebServer audispd: node=WebServer type=SYSCALL msg=audit(1644749415.398:577): arch=c000003e syscall=59 success=yes exit=0 a0=19e4cc0 a1=19e56e0 a2=19e5300 a3=7ffc46d89c20 items=2 ppid=1297 pid=1309 auid=0 uid=1000 gid=1000 euid=1000 suid=1000 fsuid=1000 egid=1000 sgid=1000 fsgid=1000 tty=pts0 ses=1 comm="grep" exe="/usr/bin/grep" subj=unconfined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023 key=(null)
2022-02-13T18:50:15+08:00 WebServer audispd: node=WebServer type=SYSCALL msg=audit(1644749415.398:577): arch=c000003e syscall=59 success=yes exit=0 a0=19e4cc0 a1=19e56e0 a2=19e5300 a3=7ffc46d89c20 items=2 ppid=1297 pid=1309 auid=0 uid=1000 gid=1000 euid=1000 suid=1000 fsuid=1000 egid=1000 sgid=1000 fsgid=1000 tty=pts0 ses=1 comm="grep" exe="/usr/bin/grep" subj=unconfined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023 key=(null)
2022-02-13T18:50:15+08:00 WebServer audispd: node=WebServer type=SYSCALL msg=audit(1644749415.400:578): arch=c000003e syscall=59 success=yes exit=0 a0=19e45a0 a1=19e4460 a2=19e5300 a3=7ffc46d89520 items=2 ppid=1310 pid=1311 auid=0 uid=1000 gid=1000 euid=1000 suid=1000 fsuid=1000 egid=1000 sgid=1000 fsgid=1000 tty=pts0 ses=1 comm="id" exe="/usr/bin/id" subj=unconfined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023 key=(null)
2022-02-13T18:50:15+08:00 WebServer audispd: node=WebServer type=SYSCALL msg=audit(1644749415.400:578): arch=c000003e syscall=59 success=yes exit=0 a0=19e45a0 a1=19e4460 a2=19e5300 a3=7ffc46d89520 items=2 ppid=1310 pid=1311 auid=0 uid=1000 gid=1000 euid=1000 suid=1000 fsuid=1000 egid=1000 sgid=1000 fsgid=1000 tty=pts0 ses=1 comm="id" exe="/usr/bin/id" subj=unconfined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023 key=(null)
2022-02-13T18:50:16+08:00 WebServer audispd: node=WebServer type=SYSCALL msg=audit(1644749416.807:579): arch=c000003e syscall=59 success=yes exit=0 a0=19e3a20 a1=19cc080 a2=19e5300 a3=7ffc46d8b4a0 items=2 ppid=1297 pid=1312 auid=0 uid=1000 gid=1000 euid=1000 suid=1000 fsuid=1000 egid=1000 sgid=1000 fsgid=1000 tty=pts0 ses=1 comm="ls" exe="/usr/bin/ls" subj=unconfined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023 key=(null)
2022-02-13T18:50:16+08:00 WebServer audispd: node=WebServer type=SYSCALL msg=audit(1644749416.807:579): arch=c000003e syscall=59 success=yes exit=0 a0=19e3a20 a1=19cc080 a2=19e5300 a3=7ffc46d8b4a0 items=2 ppid=1297 pid=1312 auid=0 uid=1000 gid=1000 euid=1000 suid=1000 fsuid=1000 egid=1000 sgid=1000 fsgid=1000 tty=pts0 ses=1 comm="ls" exe="/usr/bin/ls" subj=unconfined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023 key=(null)
2022-02-13T18:50:21+08:00 WebServer audispd: node=WebServer type=SYSCALL msg=audit(1644749421.065:580): arch=c000003e syscall=59 success=yes exit=0 a0=19e5620 a1=19ca5f0 a2=19e5300 a3=7ffc46d8b4a0 items=2 ppid=1297 pid=1313 auid=0 uid=1000 gid=1000 euid=1000 suid=1000 fsuid=1000 egid=1000 sgid=1000 fsgid=1000 tty=pts0 ses=1 comm="ls" exe="/usr/bin/ls" subj=unconfined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023 key=(null)
2022-02-13T18:50:21+08:00 WebServer audispd: node=WebServer type=SYSCALL msg=audit(1644749421.065:580): arch=c000003e syscall=59 success=yes exit=0 a0=19e5620 a1=19ca5f0 a2=19e5300 a3=7ffc46d8b4a0 items=2 ppid=1297 pid=1313 auid=0 uid=1000 gid=1000 euid=1000 suid=1000 fsuid=1000 egid=1000 sgid=1000 fsgid=1000 tty=pts0 ses=1 comm="ls" exe="/usr/bin/ls" subj=unconfined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023 key=(null)
2022-02-13T18:50:25+08:00 WebServer audispd: node=WebServer type=SYSCALL msg=audit(1644749425.098:581): arch=c000003e syscall=59 success=yes exit=0 a0=19ccc10 a1=19cca40 a2=19e5300 a3=7ffc46d8b4a0 items=2 ppid=1297 pid=1314 auid=0 uid=1000 gid=1000 euid=1000 suid=1000 fsuid=1000 egid=1000 sgid=1000 fsgid=1000 tty=pts0 ses=1 comm="date" exe="/usr/bin/date" subj=unconfined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023 key=(null)
2022-02-13T18:50:25+08:00 WebServer audispd: node=WebServer type=SYSCALL msg=audit(1644749425.098:581): arch=c000003e syscall=59 success=yes exit=0 a0=19ccc10 a1=19cca40 a2=19e5300 a3=7ffc46d8b4a0 items=2 ppid=1297 pid=1314 auid=0 uid=1000 gid=1000 euid=1000 suid=1000 fsuid=1000 egid=1000 sgid=1000 fsgid=1000 tty=pts0 ses=1 comm="date" exe="/usr/bin/date" subj=unconfined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023 key=(null)
可以看到,日志服务器已经成功收到了WebServer发送过来的日志,我们已经对用户的操作进行了审计。文章来源地址https://www.toymoban.com/news/detail-594812.html
到了这里,关于安全审计——等级保护日志审计要求的一种解决方案的文章就介绍完了。如果您还想了解更多内容,请在右上角搜索TOY模板网以前的文章或继续浏览下面的相关文章,希望大家以后多多支持TOY模板网!