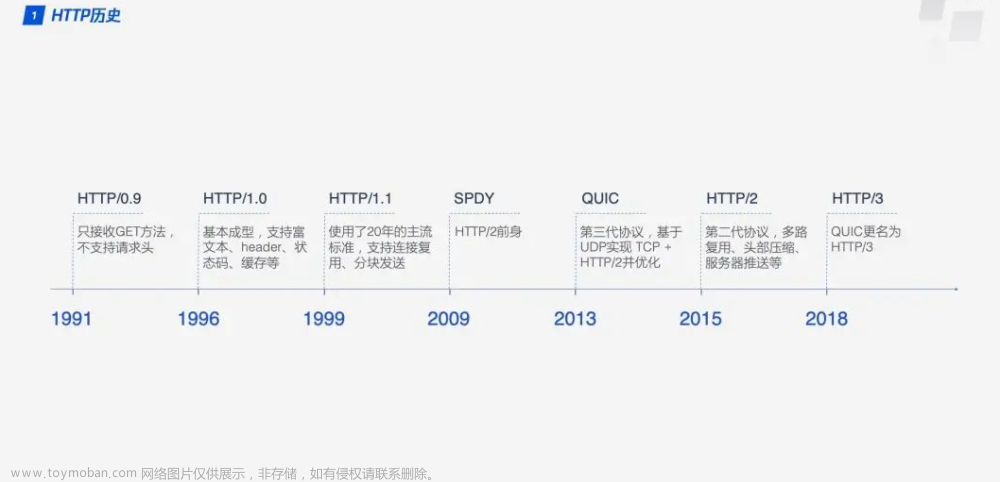
-
使用Wireshark工具打开流量文件http1.pcapng,如下图所示。

-
在过滤检索栏输入http,wireshark自动进行过滤。

-
选中其中一条记录后,wireshark 下方显示若干信息。
 文章来源:https://www.toymoban.com/news/detail-636699.html
文章来源:https://www.toymoban.com/news/detail-636699.html
Frame 81: 925 bytes on wire (7400 bits), 925 bytes captured (7400 bits) on interface eth0, id 0
Ethernet II, Src: IntelCor_ac:91:ad (38:de:ad:ac:91:ad), Dst: PcsCompu_ed:cb:ff (08:00:27:ed:cb:ff)
Internet Protocol Version 4, Src: 192.168.43.173, Dst: 192.168.43.230
Transmission Control Protocol, Src Port: 80, Dst Port: 58648, Seq: 1, Ack: 415, Len: 871
Hypertext Transfer Protocol
HTTP/1.1 200 OK\r\n
Server: nginx/1.11.5\r\n
Date: Tue, 22 Dec 2020 01:53:46 GMT\r\n
Content-Type: text/html; charset=UTF-8\r\n
Transfer-Encoding: chunked\r\n
Connection: keep-alive\r\n
Vary: Accept-Encoding\r\n
X-Powered-By: PHP/7.2.1\r\n
Content-Encoding: gzip\r\n
\r\n
[HTTP response 1/1]
[Time since request: 0.039416574 seconds]
[Request in frame: 80]
**[Request URI: http://192.168.43.173/yctf/cmd_exec/index.php?ip=flag%7Byou_can_find_it%7D]**
HTTP chunked response
Content-encoded entity body (gzip): 617 bytes -> 1221 bytes
File Data: 1221 bytes
Line-based text data: text/html (36 lines)
在 [Request URI: http://192.168.43.173/yctf/cmd_exec/index.php?ip=flag%7Byou_can_find_it%7D] 里面包含了flag。文章来源地址https://www.toymoban.com/news/detail-636699.html
到了这里,关于CTF流量题解http1.pcapng的文章就介绍完了。如果您还想了解更多内容,请在右上角搜索TOY模板网以前的文章或继续浏览下面的相关文章,希望大家以后多多支持TOY模板网!