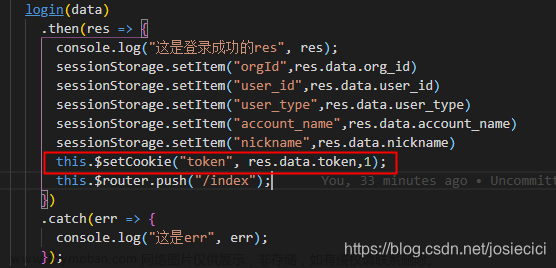
1.问题展示
项目安全扫描,扫到以下问题。
检测到目标URL存在客户端(JavaScript)Cookie引用
检测到目标Strict-Transport-Security响应头缺失
检测到目标Referrer-Policy响应头缺失
检测到目标X-Permitted-Cross-Domain-Policies响应头缺失
检测到目标X-Download-Options响应头缺失
点击劫持:X-Frame-Options未配置
2. 解决问题
设置统一过滤器,过滤所有请求,设置以上响应头,即可解决问题。文章来源:https://www.toymoban.com/news/detail-673367.html
response.addHeader("Referrer-Policy","origin");
response.addHeader("Content-Security-Policy","object-src 'self'");
response.addHeader("X-Permitted-Cross-Domain-Policies","master-only");
response.addHeader("X-Content-Type-Options","nosniff");
response.addHeader("X-XSS-Protection","1; mode=block");
response.addHeader("X-Download-Options","noopen");
// 站点劫持
response.addHeader("X-Frame-Options","SAMEORIGIN");
// 请求的响应头中缺少 Strict-Transport-Security
response.addHeader("Strict-Transport-Security","max-age=63072000; includeSubdomains; preload");
文章来源地址https://www.toymoban.com/news/detail-673367.html
到了这里,关于clickjacking(点击劫持)、请求的响应头中缺少 Strict-Transport-Security的文章就介绍完了。如果您还想了解更多内容,请在右上角搜索TOY模板网以前的文章或继续浏览下面的相关文章,希望大家以后多多支持TOY模板网!