网络攻击是指任何以干扰、破坏网络系统为目的的非授权行为。目前的网络攻击模式呈现多方位、多手段化,让人防不胜防。概括来说网络攻击分为四大类:拒绝服务攻击、利用型攻击、信息收集型攻击、欺骗型攻击。
1.拒绝服务攻击
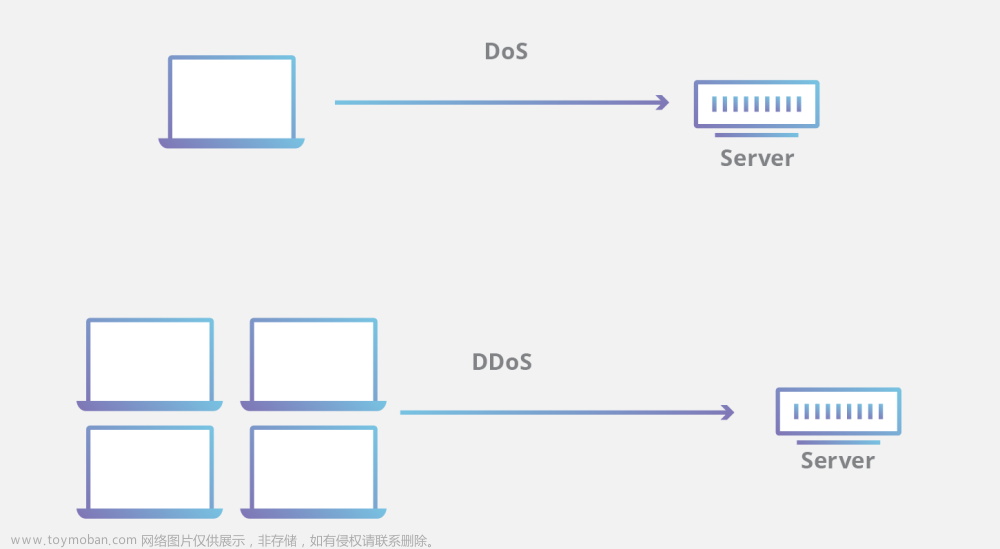
拒绝服务攻击(Denial of Service,DoS)是通过使用户服务器崩溃或阻止其提供服务,从而使合法用户无法使用网络服务器。DoS 是一种比较简单但又很有效的攻击手段。它的攻击方式有很多种,最基本的 DoS 攻击就是利用虚假地址假冒合理的用户请求来占用服务资源,致使服务超载,无法响应其他的请求。
2.利用型攻击
利用型攻击是一种试图对计算机进行控制的攻击手段。常见的方式有:口令猜测和缓冲区溢出攻击。
(1)口令猜测
攻击者通过猜测口令进入系统,获得控制系统的权限,从而对系统进行攻击。
(2)缓冲区溢出攻击
攻击者向缓冲区中写入超长的、预设的内容,导致缓冲区溢出,覆盖正常程序和数据,进而让计算机执行这些预设程序,达到进行非法操作、实现攻击的目的。
3.信息收集型攻击
攻击者对用户目标系统不直接造成危害,进行刺探性攻击,目的是获取系统的有用信息,为进一步入侵做准备。
4.欺骗型攻击
欺骗型攻击是网络攻击中的一种重要手段。常见的欺骗型攻击有IP 欺骗攻击、 DNS 欺骗攻击、Web 欺骗攻击和 E-mail 欺骗攻击。
对于一个企业、单位或学校的局域网,最常遇到的具体攻击形式主要是病毒和木马程序、黑客攻击及操作系统安全漏洞的攻击。
5.德迅云安全高防ip:
43.240.73.1
43.240.73.2
43.240.73.3
43.240.73.4
43.240.73.5
43.240.73.6
43.240.73.7
43.240.73.8
43.240.73.9
43.240.73.10
43.240.73.11
43.240.73.12
43.240.73.13
43.240.73.14
43.240.73.15
43.240.73.16
43.240.73.17
43.240.73.18
43.240.73.19
43.240.73.20
43.240.73.21
43.240.73.22
43.240.73.23
43.240.73.24
43.240.73.25
43.240.73.26
43.240.73.27
43.240.73.28
43.240.73.29
43.240.73.30
43.240.73.31
43.240.73.32
43.240.73.33
43.240.73.34
43.240.73.35
43.240.73.36
43.240.73.37
43.240.73.38
43.240.73.39
43.240.73.40
43.240.73.41
43.240.73.42
43.240.73.43
43.240.73.44
43.240.73.45
43.240.73.46
43.240.73.47
43.240.73.48
43.240.73.49
43.240.73.50
43.240.73.51
43.240.73.52
43.240.73.53
43.240.73.54
43.240.73.55
43.240.73.56
43.240.73.57
43.240.73.58
43.240.73.59
43.240.73.60
43.240.73.61
43.240.73.62
43.240.73.63
43.240.73.64
43.240.73.65
43.240.73.66
43.240.73.67
43.240.73.68
43.240.73.69
43.240.73.70
43.240.73.71
43.240.73.72
43.240.73.73
43.240.73.74
43.240.73.75
43.240.73.76
43.240.73.77
43.240.73.78
43.240.73.79
43.240.73.80
43.240.73.81
43.240.73.82
43.240.73.83
43.240.73.84
43.240.73.85
43.240.73.86
43.240.73.87
43.240.73.88
43.240.73.89
43.240.73.90
43.240.73.91
43.240.73.92
43.240.73.93
43.240.73.94
43.240.73.95
43.240.73.96
43.240.73.97
43.240.73.98
43.240.73.99
43.240.73.100
43.240.73.101
43.240.73.102
43.240.73.103
43.240.73.104
43.240.73.105
43.240.73.106
43.240.73.107
43.240.73.108
43.240.73.109
43.240.73.110
43.240.73.111
43.240.73.112
43.240.73.113
43.240.73.114
43.240.73.115
43.240.73.116
43.240.73.117
43.240.73.118
43.240.73.119
43.240.73.120
43.240.73.121
43.240.73.122
43.240.73.123
43.240.73.124
43.240.73.125
43.240.73.126
43.240.73.127
43.240.73.128
43.240.73.129
43.240.73.130
43.240.73.131
43.240.73.132
43.240.73.133
43.240.73.134
43.240.73.135
43.240.73.136
43.240.73.137
43.240.73.138
43.240.73.139
43.240.73.140
43.240.73.141
43.240.73.142
43.240.73.143
43.240.73.144
43.240.73.145
43.240.73.146
43.240.73.147
43.240.73.148
43.240.73.149
43.240.73.150
43.240.73.151
43.240.73.152
43.240.73.153
43.240.73.154
43.240.73.155
43.240.73.156
43.240.73.157
43.240.73.158
43.240.73.159
43.240.73.160
43.240.73.161
43.240.73.162
43.240.73.163
43.240.73.164
43.240.73.165
43.240.73.166
43.240.73.167
43.240.73.168
43.240.73.169
43.240.73.170
43.240.73.171
43.240.73.172
43.240.73.173
43.240.73.174
43.240.73.175
43.240.73.176
43.240.73.177
43.240.73.178
43.240.73.179
43.240.73.180
43.240.73.181
43.240.73.182
43.240.73.183
43.240.73.184
43.240.73.185
43.240.73.186
43.240.73.187
43.240.73.188
43.240.73.189
43.240.73.190
43.240.73.191
43.240.73.192
43.240.73.193
43.240.73.194
43.240.73.195
43.240.73.196
43.240.73.197
43.240.73.198
43.240.73.199
43.240.73.200
43.240.73.201
43.240.73.202
43.240.73.203
43.240.73.204
43.240.73.205
43.240.73.206
43.240.73.207
43.240.73.208
43.240.73.209
43.240.73.210
43.240.73.211
43.240.73.212
43.240.73.213
43.240.73.214
43.240.73.215
43.240.73.216
43.240.73.217
43.240.73.218
43.240.73.219
43.240.73.220
43.240.73.221
43.240.73.222
43.240.73.223
43.240.73.224文章来源:https://www.toymoban.com/news/detail-683082.html
43.240.73.225文章来源地址https://www.toymoban.com/news/detail-683082.html
到了这里,关于网络攻击的类型有哪些?的文章就介绍完了。如果您还想了解更多内容,请在右上角搜索TOY模板网以前的文章或继续浏览下面的相关文章,希望大家以后多多支持TOY模板网!