点关注不迷路
目录
点关注不迷路
SSH远程连接
一、SSH介绍
1、管理Linux服务器的方式
2、确保Linux服务正常运行
3、客户端软件
二、ssh远程连接操作
1、ssh远程连接
2、执行远程命令
3、远程拷贝文件
三、SSH怎么实现加密?
1、数据加密
2、数据加密算法
3、对称加密算法
4、非对称加密算法
四、免密SSH
1、ssh认证方式
2、基于密钥的认证流程
3、配置免密SSH
4、注意事项
5、配置Windows与Linux间的免密
五、SSH服务配置
2、关闭SELinux
1、配置文件
2、常用配置项
SSH远程连接
一、SSH介绍
- SSH 应用层协议
- 实现Linux主机加密、远程连接
- 适用于Linux服务器远程连接
- telnet
- 远程连接,不加密
- 适用于局域网网络设备的远程连接
1、管理Linux服务器的方式
- 本地管理
- 安装系统、故障修复
- 远程管理
2、确保Linux服务正常运行
1)确认ssh服务正常运行
[root@haha ~]# ps -elf | grep ssh
4 S root 1038 1 0 80 0 - 28225 poll_s 13:20 ? 00:00:00 /usr/sbin/sshd -D
4 S root 1073 1038 0 80 0 - 39726 poll_s 13:20 ? 00:00:00 sshd: root@pts/0
0 S root 1336 1247 0 80 0 - 28206 pipe_w 13:25 pts/0 00:00:00 grep --color=auto ssh
[root@haha ~]# netstat -tunlp | grep "sshd"
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN 1038/sshd
tcp6 0 0 :::22 :::* LISTEN 1038/sshd
[root@haha ~]# - ssh服务端口:22/tcp
2)对应服务端软件
[root@haha ~]# rpm -qf /usr/sbin/sshd
openssh-server-7.4p1-21.el7.x86_64
3、客户端软件
- Windows
- xshell
- secureCRT
- putty
- Linux
- ssh命令
[root@haha ~]# which ssh
/usr/bin/ssh
[root@haha ~]# rpm -qf /usr/sbin/sshd
openssh-server-7.4p1-21.el7.x86_64
[root@haha ~]#二、ssh远程连接操作
1、ssh远程连接
#ssh 用户名@服务器地址
2、执行远程命令
[root@localhost ~]# ssh root@192.168.59.100 uptime
root@192.168.59.100's password:
10:33:44 up 38 min, 1 user, load average: 0.00, 0.01, 0.02
[root@localhost ~]# ssh root@192.168.59.100 ifconfig ens33
root@192.168.59.100's password: 3、远程拷贝文件
- scp //只能拷文件 拷目录要加 -r
- rsync
- 增量拷贝工具
1)scp命令的使用 //拷目录
#scp 源文件 用户名@服务器地址:目录
[root@node01 ~]# scp /opt/file01.txt root@192.168.140.11:/tmp
[root@node01 ~]# scp root@192.168.140.11:/etc/passwd /tmp/[root@node01 ~]# scp -r /opt/linux/ root@192.168.140.11:/tmp/2)rsync命令的使用 //拷文件
- 确保所有Linux主机正常安装rsync软件
- -a 保留权限
- -v 显示详细过程
[root@node01 ~]# rsync -av /opt/python/ root@192.168.140.11:/tmp/
root@192.168.140.11's password:
sending incremental file list
./
1.py
10.py
2.py
3.py
4.py
5.py
6.py
7.py
8.py
9.py
sent 581 bytes received 209 bytes 225.71 bytes/sec
total size is 0 speedup is 0.00三、SSH怎么实现加密?
- 利用非对称算法
- ssh首次连接主机时,主机会自动发送自己的密钥,询问是否接受
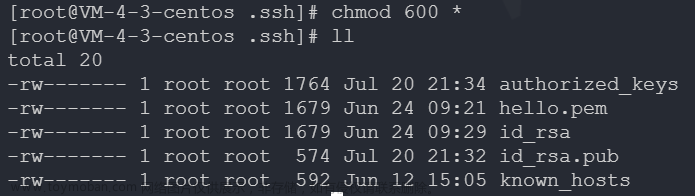
- ssh密钥存储位置:
- ~/.ssh/known_hosts
1、数据加密
- 利用数学算法、密钥实现加密
2、数据加密算法
- 对称加密
- 非对称加密
3、对称加密算法
- 数据加密、解密使用的密钥是一样的

4、非对称加密算法
- 加密、解密时使用的密钥是不一样的
- 基于密钥对(公钥、私钥)
- 本质上就是利用特定的数学算法生成的随机数
- 公钥加密,私钥加密

四、免密SSH
1、ssh认证方式
- 基于用户名、密码的认证【默认】
- 基于密钥的认证
2、基于密钥的认证流程
- 在客户端生成密钥对
- 将公钥拷贝到服务器
3、配置免密SSH
1)在客户端生成密钥对
[root@localhost ~]# ssh-keygen -t rsa
Generating public/private rsa key pair.
Enter file in which to save the key (/root/.ssh/id_rsa):
Created directory '/root/.ssh'.
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /root/.ssh/id_rsa.
Your public key has been saved in /root/.ssh/id_rsa.pub.
The key fingerprint is:
SHA256:/3KJAFuexCyTP2cjxa19nRXzJaGjH1PlPojrARqVusg root@localhost.localdomain
The key's randomart image is:
+---[RSA 2048]----+
| ...|
| . ..=.|
| + + .o ..*|
| = B o.oo..o|
| %S+.+o. o+|
| . o @.*.oo..o|
| E o *.=.o |
| +.+ |
| +. |
+----[SHA256]-----+
- 私钥
[root@localhost ~]# cd /root/.ssh/
[root@localhost .ssh]# ls
id_rsa id_rsa.pub
[root@localhost .ssh]# cat id_rsa
-----BEGIN RSA PRIVATE KEY-----
MIIEowIBAAKCAQEAp1aUNBtiPp5NqcGwjJ069u1jpyl5k6ThkYKej2Tuelo5IzWu
nHPfpUwtItcLZ1mflqi48uD+/EJWKrt4dg8BPmuoAnYUaKjtCro/FDz55vy+W5tg
jVyaC2Ii5LdUNjIiNqtklVDapsmmpK7aSaUeL244kdZovKaiNM0gKmfDMpu4O6OQ
uMfrNaFkL5kfBxPVVsoUK6GpgkcuXG5EP62Q3t5s9mVzenAM6JevUMqDMFa0IsNX
Ucme1saIZiB/IPvm6Rx/zVKtmG23652N2BgXOh+LxaQ5240Tbat0m1HfCLf5k6aj
j22RTXNAT8AYeBycWKBXGAERJ239sikzGLwN+wIDAQABAoIBADH6o+0kOKWnNl77
YLW+yDu0D02AD7XPSyfgsWb2qFuW0vX3NJ255hRCukBrphZKKGYhIow4MzA4x++f
ao0oUiDImreReOsBeTr5AZoT1DfvSROnRqEyBThdKTrSnq5JLvrRGguWyJeEJueM
6dmRHYDhFLhKJ6IgytWmZnMD5sMYT70Ts0+2IWQpdnqw7dxsoSKy59QX4E5FGr0z
K7mYnopldr+/srf7OrlOrVTCylIDM/J3K47v2vH5n8bQKjTkPm+e+vm8nUwPnz7a
3mfxAS9uhnIx57vcPHmmFJdNUO3eIgav7s4sRKloPdEXQINdWx1kbZQz3kd8lV3Q
mYzeEUECgYEAz8/+3Bjq2AvX2FHXXg/V3bEJnSOMDAmn8JOQcCF62IYxC+YC7reu
u30BHmV26YJrXXm/HnjAhpXIxvXcaUd30iow6sclHcE7GhcAgyn8A+9fKRXyeGEj
JYXa/iETtg+xOt47m1etbJKxq77gvqE5yWXMapHGDs8FWWSpNuf8MjECgYEAziP6
6hjtGEKStmwB1OE8y8pscPnpP1Rm8B692jqMR8dmgSSZNQMGINbkgYvTQls3dNLh
JR+4RUx3foXYq7df/jM4+Suj74O+kPsq5s7dumeAgucJzTnOV5up4LxlPF2qR+Rl
mRnQD/BXIYJkwe/QxPHW/21+OgrXbqzlP2vX6+sCgYEAj4wnijWUE0SrBnwR/qGF
o6tk7qzdUnthDGeCQFKAHw0i2As8P1WWV2BT44FHEKnMLDeq8wuKQe05UWYHqJl7
hSsruyFw3ArcHnuBGRlpQfaZjzHf2ZOPyZ2a1ixXB03zqKxWFEoOO49hNzeU21lX
J20wNPUZEKWkFknYMVsx9CECgYAJzEYB2Ht0er2UdB/GKYqFOTLcT9SZUP6vjRaD
B+NhCgZCPyYVEfa5mt0zlxzMe59wKxHOfOp6SL8pQV1iFA44++BKX5ukJ8PoCjgo
zk5VrNO75RVfLs8y9NAnQW0iaGVOk3mMxGBSUZ8ilZsKaMaohcItU9v7EEbbGNaw
pASYTwKBgHM49ie68PcbG8yLSza7LfcLj9IS5Q3jQ2gmCBiDlxEqOQg9cEpSRNid
UE25jKCJIhkmTk7vpS4IXw6ZFR3BcOuxF0gl4GJGVFzX6B9lRqLyP3Gy1ovMfP+5
9x+jUbMNN3+XDoUon0HuL/O8vcXqcTZ8VHfolhzlHYwGIaFxwaHh
-----END RSA PRIVATE KEY-----
[root@localhost .ssh]#
- 公钥
[root@localhost .ssh]# cat id_rsa.pub
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCnVpQ0G2I+nk2pwbCMnTr27WOnKXmTpOGRgp6PZO56WjkjNa6cc9+lTC0i1wtnWZ+WqLjy4P78QlYqu3h2DwE+a6gCdhRoqO0Kuj8UPPnm/L5bm2CNXJoLYiLkt1Q2MiI2q2SVUNqmyaakrtpJpR4vbjiR1mi8pqI0zSAqZ8Mym7g7o5C4x+s1oWQvmR8HE9VWyhQroamCRy5cbkQ/rZDe3mz2ZXN6cAzol69QyoMwVrQiw1dRyZ7WxohmIH8g++bpHH/NUq2YbbfrnY3YGBc6H4vFpDnbjRNtq3SbUd8It/mTpqOPbZFNc0BPwBh4HJxYoFcYAREnbf2yKTMYvA37 root@localhost.localdomain2)将公钥拷贝到服务器
[root@localhost .ssh]# ssh-copy-id root@192.168.59.151
/usr/bin/ssh-copy-id: INFO: Source of key(s) to be installed: "/root/.ssh/id_rsa.pub"
The authenticity of host '192.168.59.151 (192.168.59.151)' can't be established.
ECDSA key fingerprint is SHA256:rjrgFHXhI3DnTNoe1oMu2g9XTU9PXA3475p3SEum7FI.
ECDSA key fingerprint is MD5:a5:61:33:71:bc:eb:ae:8e:ac:d8:bf:08:2e:1e:91:50.
Are you sure you want to continue connecting (yes/no)? yes
/usr/bin/ssh-copy-id: INFO: attempting to log in with the new key(s), to filter out any that are already installed
/usr/bin/ssh-copy-id: INFO: 1 key(s) remain to be installed -- if you are prompted now it is to install the new keys
root@192.168.59.151's password:
Number of key(s) added: 1
Now try logging into the machine, with: "ssh 'root@192.168.59.151'"
and check to make sure that only the key(s) you wanted were added.
[root@localhost .ssh]#
- 自动将公钥拷贝到对方服务器用户家目录
- /root/.ssh/authorized_keys
3)验证
[root@ck1 ~]# ssh root@192.168.59.151 ifconfig ens33
ens33: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.59.151 netmask 255.255.255.0 broadcast 192.168.59.255
inet6 fe80::20c:29ff:fe94:9536 prefixlen 64 scopeid 0x20<link>
ether 00:0c:29:94:95:36 txqueuelen 1000 (Ethernet)
RX packets 287 bytes 37816 (36.9 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 281 bytes 39470 (38.5 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
4、注意事项
- 免密SSH基于用户
- 免密SSH是单向的
5、配置Windows与Linux间的免密
1)在Windows生成密钥对
在xshell软件中点工具---->新建用户密钥生成向导




[root@ck1 ~]# rpm -q lrzsz
lrzsz-0.12.20-36.el7.x86_64
[root@ck1 ~]# rz
[root@ck1 ~]# ls
anaconda-ks.cfg id_rsa_2048.pub
[root@ck1 ~]# mv id_rsa_2048.pub /root/.ssh/authorized_keys
[root@ck1 ~]# ls -l /root/.ssh/
总用量 16
-rw-r--r--. 1 root root 380 8月 29 19:52 authorized_keys
-rw-------. 1 root root 1675 8月 29 19:39 id_rsa
-rw-r--r--. 1 root root 390 8月 29 19:39 id_rsa.pub
-rw-r--r--. 1 root root 176 8月 29 19:42 known_hosts
[root@ck1 ~]#
2)将公钥拷贝到服务器
[root@localhost ~]# cat id_rsa_2048.pub >> /root/.ssh/authorized_keys
[root@localhost ~]# cat /root/.ssh/authorized_keys
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCtQk+Kx4bafhFsSwZC09RQXT2UIux6KDOeXmzYxN+oZFrXqSIGHHforssyiEUqV9dfETmv6kYencgSsU37ecSpn/3QUVuTU6bu26zF4sSF/w+qYuylJ1TuDg5HsqpRWbrJ5Q8eGLg9lwozlCQ0lswLnxmAM1B66SJuY8Lsm1W9f5XBA/RweNiVJwFHoqLHTVwnn0/Gt/LdfL/LnqH+TxbSjnf9mRdBVtogsAITDCBqpzRDCW/XaBkmKOe9mXC/8rZ6saZdLyZKQXefl52Wdh9mYbRVvO32YTnTdLk1mQ3fwOotBlVIPMMrx2HLRIhQXP1L7q9U4f39uPIqYcT3rUvj root@node01.linux.com
ssh-rsa AAAAB3NzaC1yc2EAAAABIwAAAQEArrxv/vWwlcsBBNkYCQ0K07nqqDDbbd27eFRIrT+uX0SQ+i1dIXcBgNDf0Zt3nJw9n8bAnksiKxxC6OzRaCMIm/XDr8V75gd3DybeBXO7IVybA/OAr6LVRY5ehAI9OyqMPe6yUxRyekk6uV3KOattMeD2rya0JBTXnjgZjRqc4pApxdh4pAwZGGtaS447TLogLrdnfxAvcEp7dyXl5li/wPRRB2dHZEjyULErWl+R7+Li0nlz2TO790dqHYBcnqdmwMO5iCjIL5trVRqPAgf1HJ7N7/M298h8nCgYR0w80T/E7d/M9/H5x63UYGF/yck891G9tgtqkJsIgukEOXGudQ==[root@localhost ~]# 3)验证

五、SSH服务配置
前提工作:
1、关闭防火墙
#systemctl stop firewalld //关闭
#systemctl disable firewalld //关闭开机自启动
#systemctl mask firewalld //彻底禁用
#iptables -F
2、关闭SELinux
#getenforce //查看SELinux
#setenforce 0 //临时关闭
#vim /etc/sysconfig/selinux //永久关闭
SELINUX=disabled
1、配置文件
- /etc/ssh/sshd_config
2、常用配置项
1)修改ssh服务端口
Port 44444
[root@localhost ~]# systemctl restart sshd2)禁用密码认证
PasswordAuthentication no3)禁止root用户远程登录文章来源:https://www.toymoban.com/news/detail-783999.html
PermitRootLogin no4)禁用DNS反解,加快ssh连接速度文章来源地址https://www.toymoban.com/news/detail-783999.html
UseDNS no 到了这里,关于云计算Linux运维——基础服务应用——SSH远程连接(1)的文章就介绍完了。如果您还想了解更多内容,请在右上角搜索TOY模板网以前的文章或继续浏览下面的相关文章,希望大家以后多多支持TOY模板网!