在Red Hat Enterprise Linux 或其他类似的Linux发行版中,全局umask设置通常在几个不同的系统级配置文件中定义。以下是一些可能设置umask的地方:
(1)/etc/profile:
这是为系统上的所有用户设置全局环境变量和启动程序的地方。通常,umask设置会在这个文件中定义。
[root@iZ8vb0njm9zbv3qvisb1ktZ ~]# vim /etc/profile
EUID=`/usr/bin/id -u`
UID=`/usr/bin/id -ru`
fi
USER="`/usr/bin/id -un`"
LOGNAME=$USER
MAIL="/var/spool/mail/$USER"
fi
# Path manipulation
if [ "$EUID" = "0" ]; then
pathmunge /usr/sbin
pathmunge /usr/local/sbin
else
pathmunge /usr/local/sbin after
pathmunge /usr/sbin after
fi
HOSTNAME=`/usr/bin/hostname 2>/dev/null`
HISTSIZE=1000
if [ "$HISTCONTROL" = "ignorespace" ] ; then
export HISTCONTROL=ignoreboth
else
export HISTCONTROL=ignoredups
fi
export PATH USER LOGNAME MAIL HOSTNAME HISTSIZE HISTCONTROL
# By default, we want umask to get set. This sets it for login shell
# Current threshold for system reserved uid/gids is 200
# You could check uidgid reservation validity in
# /usr/share/doc/setup-*/uidgid file
if [ $UID -gt 199 ] && [ "`/usr/bin/id -gn`" = "`/usr/bin/id -un`" ]; then
umask 002
else
umask 022
fi
for i in /etc/profile.d/*.sh /etc/profile.d/sh.local ; do
if [ -r "$i" ]; then
if [ "${-#*i}" != "$-" ]; then
. "$i"
else
. "$i" >/dev/null
fi
fi
done
unset i
unset -f pathmunge
if [ -n "${BASH_VERSION-}" ] ; then
if [ -f /etc/bashrc ] ; then
# Bash login shells run only /etc/profile
# Bash non-login shells run only /etc/bashrc
# Check for double sourcing is done in /etc/bashrc.
. /etc/bashrc
fi
fi
(2)/etc/bashrc 或 /etc/bash.bashrc:
对于使用Bash shell的系统,这个文件包含了所有Bash用户的全局定义和别名。umask也可能在这里设置。
# /etc/bashrc
# System wide functions and aliases
# Environment stuff goes in /etc/profile
# It's NOT a good idea to change this file unless you know what you
# are doing. It's much better to create a custom.sh shell script in
# /etc/profile.d/ to make custom changes to your environment, as this
# will prevent the need for merging in future updates.
# Prevent doublesourcing
if [ -z "$BASHRCSOURCED" ]; then
BASHRCSOURCED="Y"
# are we an interactive shell?
if [ "$PS1" ]; then
if [ -z "$PROMPT_COMMAND" ]; then
case $TERM in
xterm*|vte*)
if [ -e /etc/sysconfig/bash-prompt-xterm ]; then
PROMPT_COMMAND=/etc/sysconfig/bash-prompt-xterm
elif [ "${VTE_VERSION:-0}" -ge 3405 ]; then
PROMPT_COMMAND="__vte_prompt_command"
else
PROMPT_COMMAND='printf "\033]0;%s@%s:%s\007" "${USER}" "${HOSTNAME%%.*}" "${PWD/#$HOME/\~}"'
fi
;;
screen*)
if [ -e /etc/sysconfig/bash-prompt-screen ]; then
PROMPT_COMMAND=/etc/sysconfig/bash-prompt-screen
else
PROMPT_COMMAND='printf "\033k%s@%s:%s\033\\" "${USER}" "${HOSTNAME%%.*}" "${PWD/#$HOME/\~}"'
fi
;;
*)
[ -e /etc/sysconfig/bash-prompt-default ] && PROMPT_COMMAND=/etc/sysconfig/bash-prompt-default
;;
esac
fi
# Turn on parallel history
shopt -s histappend
history -a
# Turn on checkwinsize
shopt -s checkwinsize
[ "$PS1" = "\\s-\\v\\\$ " ] && PS1="[\u@\h \W]\\$ "
# You might want to have e.g. tty in prompt (e.g. more virtual machines)
# and console windows
# If you want to do so, just add e.g.
# if [ "$PS1" ]; then
# PS1="[\u@\h:\l \W]\\$ "
# fi
# to your custom modification shell script in /etc/profile.d/ directory
fi
if ! shopt -q login_shell ; then # We're not a login shell
# Need to redefine pathmunge, it gets undefined at the end of /etc/profile
pathmunge () {
case ":${PATH}:" in
*:"$1":*)
;;
*)
if [ "$2" = "after" ] ; then
PATH=$PATH:$1
else
PATH=$1:$PATH
fi
esac
}
# By default, we want umask to get set. This sets it for non-login shell.
# Current threshold for system reserved uid/gids is 200
# You could check uidgid reservation validity in
# /usr/share/doc/setup-*/uidgid file
if [ $UID -gt 199 ] && [ "`/usr/bin/id -gn`" = "`/usr/bin/id -un`" ]; then
umask 002
else
umask 022
fi
SHELL=/bin/bash
# Only display echos from profile.d scripts if we are no login shell
# and interactive - otherwise just process them to set envvars
for i in /etc/profile.d/*.sh; do
if [ -r "$i" ]; then
if [ "$PS1" ]; then
. "$i"
else
. "$i" >/dev/null
fi
fi
done
unset i
unset -f pathmunge
fi
fi
# vim:ts=4:sw=4
(3)Shell个人配置文件:
如~/.bashrc, ~/.bash_profile, ~/.profile等,这些是针对单个用户的配置文件。虽然这些不是全局设置,但是管理员可能已经为每个用户配置了默认的umask。
PAM (Pluggable Authentication Modules) 配置:
在/etc/pam.d/目录下的PAM配置文件中,可能会有pam_umask.so模块的相关配置。例如,在/etc/pam.d/login文件中,可能会有如下行来设置umask:
session optional pam_umask.so
或者指定了一个默认的umask值:
session optional pam_umask.so umask=0022
(4)Systemd服务文件:
如果你是在Systemd服务中更改umask,那么你需要查看服务的配置文件。这些文件通常位于/etc/systemd/system/或/usr/lib/systemd/system/目录下。在服务文件中,可以通过UMask=指令设置umask。
要查看当前的全局umask设置,你可以在终端中运行以下命令:
umask
这将显示当前shell会话的umask值。要找出是哪个配置文件设置了这个值,你可能需要手动检查上述文件。你可以使用grep命令来帮助搜索这些文件中的umask设置:
[root@iZ8vb0njm9zbv3qvisb1ktZ system]# grep -ir "umask" /etc/profile /etc/bashrc /etc/bash.bashrc /etc/pam.d/ /etc/systemd/system/ /usr/lib/systemd/system/
/etc/profile:# By default, we want umask to get set. This sets it for login shell
/etc/profile: umask 002
/etc/profile: umask 027
/etc/bashrc: # By default, we want umask to get set. This sets it for non-login shell.
/etc/bashrc: umask 002
/etc/bashrc: umask 022
grep: /etc/bash.bashrc: No such file or directory
/usr/lib/systemd/system/rsyslog.service:UMask=0066
请注意,如果你的系统配置了多个地方设置了umask,最终的umask值将取决于这些配置的加载顺序和优先级。通常,最后执行的配置文件中的设置将覆盖之前的设置。
那么,文件掩码到底是什么呢?
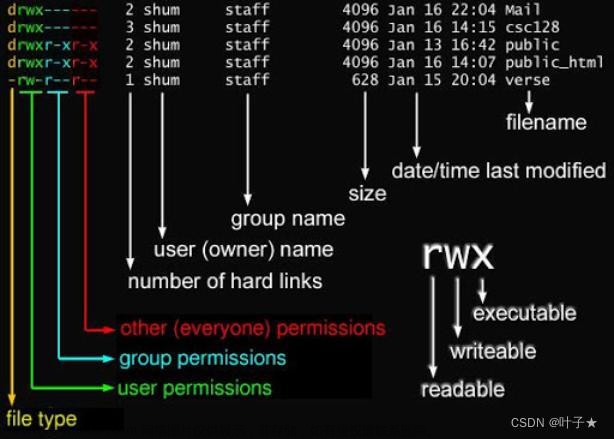
其实在Linux系统中,文件掩码(umask)用于确定新创建的文件或目录的默认权限。umask值是一个三位的八进制数,每一位分别对应用户(u)、组(g)和其他(o)的权限。
umask值实际上是一个“反向”的权限设置。也就是说,它定义了哪些权限应该被移除,而不是哪些权限应该被赋予。因此,要得到新创建的文件或目录的默认权限,你需要从全权限(即777对于目录,666对于文件)中减去umask值。
如果umask值是022,那么:
对于目录,全权限是777,减去umask值022后,得到的默认权限是755。也就是说,用户有读(r)、写(w)和执行(x)权限,组和其他用户有读和执行权限。
对于文件,全权限是666,减去umask值022后,得到的默认权限是644。也就是说,用户有读和写权限,组和其他用户只有读权限。文章来源:https://www.toymoban.com/news/detail-792642.html
请注意,这只是默认权限。你可以在创建文件或目录后,使用chmod命令来更改它们的权限。文章来源地址https://www.toymoban.com/news/detail-792642.html
到了这里,关于Linux笔记:Linux中的文件系统权限的文章就介绍完了。如果您还想了解更多内容,请在右上角搜索TOY模板网以前的文章或继续浏览下面的相关文章,希望大家以后多多支持TOY模板网!

![[Linux]文件系统权限与访问控制](https://imgs.yssmx.com/Uploads/2024/02/426421-1.png)