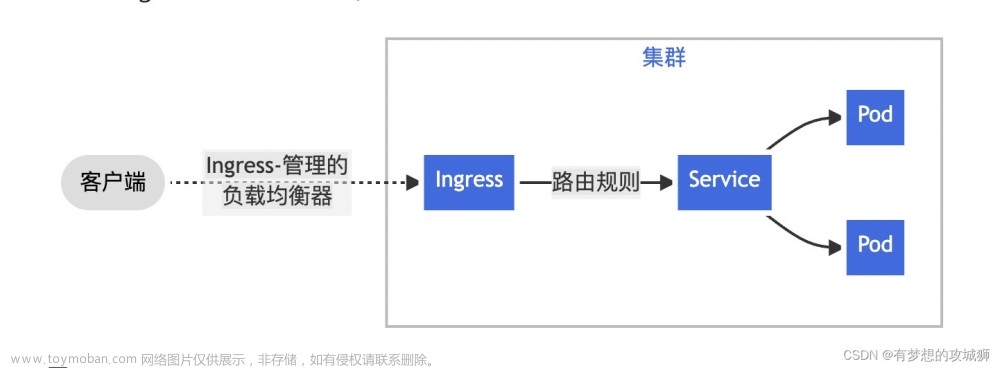
ingress基于域名进行映射,把url(http https)的请求转发到service,再由service把请求转发到每一个pod
ingress只要一个或者少量的公网ip或者LB,可以把多个http请求暴露到外网,七层反向代理
理解为service的service,是一组基于域名和URL路径,把一个或者多个请求转发到service
先是七层代理然后再是四层代理再到pod
ingress >service>nginx
ingress的组成:
ingress是要给api对象,通过yaml文件来进行配置,ingress作用定义规则,定义请求如何转发到service的规则,配置的一个模板
ingress通过http和https暴漏集群内部的service,给service提供一个外部的url,负载均衡,ssl/tls(https),实现一份基于域名的负载均衡
ingress-controller:是具体的实现反向代理和负载均衡的程序,对ingress定义的规则进行解析,根据ingress的配置规则进行请求的转发
ingress-controller:不是k8s自带的组件功能,ingress-controller一个统称。
nginx ingress controller,traefik都是ingress-controller,开源
ingress资源的定义项
1、定义外部流量的路由规则
2、定义服务的暴漏方式,主机名,访问路径和其他的选项
3、负载均衡(ingress-controller)
nginx-ingress-controller运行方式是pod方式运行在集群当中
nginx-ingress-controller
ingress暴漏服务的方式
1、deployment+loadBalancer模式
ingress部署在公有云,会ingress配置文件里面会有一个type,type:LoadBalancer,公有云平台会为个loadbalancer的service创建一个负载均衡器,绑定一个公网地址。
通过域名指向这个公网地址就可以实现集群对外暴漏。
2、方式二:DaemonSet+hostnetwork+nodeSelector
DaemonSet在每个节点都会创建一个pod
hostnetwork:pod会共享节点主机的网络命名空间,容器内直接使用节点主机ip+端口,pod中的容器直接访问主机上网络资源

nodeSelector:根据标签来选择部署的节点,nginx-ingress-controller部署的节点
缺点:直接利用节点主机的网络和端口,一个node只能部署一个ingress-controller pod.比较适合大并发的生产环境。性能最好的。
netstat -lntp | grep nginx
8081端口,nginx-controller默认配置的一个bachend。反向代理端口
所有的请求当中,只要是不符合ingress配置的请求转发到8181,相当于一个error的页面

现在执行这个yaml文件,会生成一个service会生成一个service,在ingress-nginx这个命名空间生成一个service,所有的controlle的请求都会从这个定义的service的nodeport的端口,把请求转发到自定义的service的pod

过程
wget https://gitee.com/mirrors/ingress-nginx/raw/nginx-0.30.0/deploy/static/mandatory.yaml
vim mandatory.yaml
apiVersion: apps/v1
#kind: Deployment
kind: DaemonSet
metadata:
name: nginx-ingress-controller
namespace: ingress-nginx
labels:
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
spec:
replicas: 1
selector:
matchLabels:
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
template:
metadata:
labels:
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
annotations:
prometheus.io/port: "10254"
prometheus.io/scrape: "true"
spec:
# wait up to five minutes for the drain of connections
hostNetwork: true
terminationGracePeriodSeconds: 300
serviceAccountName: nginx-ingress-serviceaccount
nodeSelector:
test1: "true"
#kubernetes.io/os: linux
#在master节点上上传镜像压缩包
cd /opt/ingress
tar zxvf ingree.contro.tar.gz
#所有节点加载镜像包
docker load -i ingree.contro.tar
kubectl apply -f mandatory.yaml
//到 node02 节点查看
netstat -lntp | grep nginx
vim /opt/ingress/nginx-service.yaml
apiVersion: v1
kind: PersistentVolumeClaim
metadata:
name: nfs-pvc1
spec:
accessModes:
- ReadWriteMany
storageClassName: nfs-client-storagesclass
resources:
requests:
storage: 2Gi
---
apiVersion: apps/v1
kind: Deployment
metadata:
name: nginx-app1
labels:
app: nginx2
spec:
replicas: 3
selector:
matchLabels:
app: nginx2
template:
metadata:
labels:
app: nginx2
spec:
containers:
- name: nginx
image: nginx:1.22
volumeMounts:
- name: nfs-pvc2
mountPath: /usr/share/nginx/html/
volumes:
- name: nfs-pvc2
persistentVolumeClaim:
claimName: nfs-pvc2
---
apiVersion: v1
kind: Service
metadata:
name: nginx-app-svc2
spec:
ports:
- protocol: TCP
port: 80
targetPort: 80
selector:
app: nginx2
---
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: nginx-app-ingress2
spec:
rules:
- host: www.test1.com
http:
paths:
- path: /
pathType: Prefix
backend:
service:
name: nginx-app-svc2
port:
number: 80
kubectl apply -f nginx-service.yaml
3、deployment+NodePort:
nginx+ingress-controller
host--->ingress的配置赵大鹏pod---controller---请求到pod
nodeport----controller---ingress==service---pod
nodeport暴露端口的方式最简单的方法,nodeport多了一层nat地址转换
并发量大的对性能会有一定影响,内部都会用nodeport

apiVersion: v1
kind: PersistentVolumeClaim
metadata:
name: nfs-pvc3
spec:
accessModes:
- ReadWriteMany
storageClassName: nfs-client-storageclass
resources:
requests:
storage: 2Gi
---
apiVersion: apps/v1
kind: Deployment
metadata:
name: nginx-app3
labels:
app: nginx3
spec:
replicas: 1
selector:
matchLabels:
app: nginx3
template:
metadata:
labels:
app: nginx3
spec:
containers:
- name: nginx3
image: nginx:1.22
volumeMounts:
- name: nfs-pvc3
mountPath: /usr/share/nginx/html
volumes:
- name: nfs-pvc3
persistentVolumeClaim:
claimName: nfs-pvc3
---
apiVersion: v1
kind: Service
metadata:
name: nginx-app-svc3
spec:
ports:
- protocol: TCP
port: 80
targetPort: 80
selector:
app: nginx3
---
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: nginx-app-ingress3
spec:
rules:
- host: www.test2.com
http:
paths:
- path: /
pathType: Prefix
backend:
service:
name: nginx-app-svc3
port:
number: 80
kubectl apply -f nodePort.yaml
vim /etc/hosts
20.0.0.92 www.test2.com
~ 
Ingress HTTP 代理访问虚拟主机
apiVersion: apps/v1
kind: Deployment
metadata:
name: deployment1
spec:
replicas: 1
selector:
matchLabels:
name: nginx1
template:
metadata:
labels:
name: nginx1
spec:
containers:
- name: nginx1
image: nginx:1.14
imagePullPolicy: IfNotPresent
ports:
- containerPort: 80
---
apiVersion: v1
kind: Service
metadata:
name: svc-1
spec:
ports:
- port: 80
targetPort: 80
protocol: TCP
selector:
name: nginx1
kubectl apply -f deployment1.yaml
vim deployment2.yaml
apiVersion: apps/v1
kind: Deployment
metadata:
name: deployment2
spec:
replicas: 1
selector:
matchLabels:
name: nginx2
template:
metadata:
labels:
name: nginx2
spec:
containers:
- name: nginx2
image: nginx:1.14
imagePullPolicy: IfNotPresent
ports:
- containerPort: 80
---
apiVersion: v1
kind: Service
metadata:
name: svc-2
spec:
ports:
- port: 80
targetPort: 80
protocol: TCP
selector:
name: nginx2
kubectl apply -f deployment2.yaml
创建ingress资源
vim ingress-nginx.yaml
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: ingress1
spec:
rules:
- host: www.test.com
http:
paths:
- path: /
pathType: Prefix
backend:
service:
name: svc-1
port:
number: 80
---
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: ingress2
spec:
rules:
- host: www.abc.com
http:
paths:
- path: /
pathType: Prefix
backend:
service:
name: svc-2
port:
number: 80
kubectl apply -f ingress-nginx.yaml
ingress实现https代理访问
证书密钥创建证书,密钥
创建证书 密钥
secret 保存密钥信息
openssl req -x509 -sha256 -nodes -days 356 -newkey rsa:2048 -keyout tls.key -out tls.crt -subj "CN=nginxsvc/O=nginxsvc"
openssl req -x509 -sha256 -nodes -days 356 -newkey rsa:2048 -keyout tls.key -out tls.crt -subj "CN=nginxsvc/O=nginxsvc"
req生成证书文件的
x509生成x.509自签名 的证书
-sha256:表示使用sha-256的散列算法
-nodes:表示生成的密钥不加密
-days:365天 证书有效期365天
-newkey rsa:RSA的密钥对,长度2048位
-subj "/CN=nginxsvc/O=nginxsvc":主题,CN common name O: organzation组织
kubectl create secret tls tls-secret --key tls.key --cert tls.crt
kubectl describe secrets tls-secret
cd /opt
mkdir https
vim ingress-cs.yaml
apiVersion: apps/v1
kind: Deployment
metadata:
name: nginx-https
labels:
app: https
spec:
replicas: 3
selector:
matchLabels:
app: https
template:
metadata:
labels:
app: https
spec:
containers:
- name: nginx
image: nginx:1.22
---
apiVersion: v1
kind: Service
metadata:
name: nginx-svc
spec:
ports:
- port: 80
targetPort: 80
protocol: TCP
selector:
app: https
---
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: nginx-ingress-https
spec:
tls:
- hosts:
- www.123ccc.com
secretName: tls-secret
#加密的配置保存在ingress当中,请求先到ingress-controller再根据ingress配置解析再转发到service,在代理进行时就要先验证密钥对,然后再把请求转发到service对应的pod。
rules:
- hosts: www.123ccc.com
http:
paths:
- paths: /
pathType: prefix
backend:
service:
name: nginx-svc
port:
number: 80
kubectl get svc -n ingress-nginx容器对nginx实现账号密码认证
mkdir basic-auth
yum -y install http
cd basic-auth
vim ingress-auth.yaml
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: ingress-auth
annotations:
#开启认证模块的位置
nginx.ingress.kubernets.io/auth-type: basic
#设置认证类型basic,这是k8s自带的认证加密模块
nginx.ingress.kubernets.io/auth-secret: basic-auth
#把认证的加密模块导入到ingress当中
nginx.ingress.kubernets.io/auth-realm: 'Authentication Required -wqb'
#设置认证窗口的提示信息。
spec:
rules:
- host: www.wqb.com
http:
paths:
- path: /
pathType: Prefix
backend:
service:
name: nginx-svc
port:
number: 80
kubectl apply -f ingress-auth.yaml
vim nginx-rewrite.yaml
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: nginx-rewrite
annotation:
nginx.ingress.kubernetes.io/rewrite-target: https://www.123ccc.com:32336
#访问页面会跳转到指定的页面。
spec:
rules:
- host: www.wqb.com
http:
paths:
- path: /
pathType: Prefix
backend:
service:
name: nginx-svc
port:
number: 80
kubectl apply -f nginx-rewrite.yaml



traefik是一个为了让部署微服务更加快捷而诞生的一个http反向代理,负载均衡
traefik设计时就能够实现和k8ss API交互,感知后端service以及pod的变化,可以自动更新配置和重载
pod内的nginx 80 8081
traefik的部署方式
daemonset
特点优点:每个节点都会部署要给traeflk,节点感知,可以自动发现,更新容器的配置,不需要手动重载
缺点:资源占用,大型集群中,aemonset可能会运行多个traefik的实例,尤其时节点上不需要大量容器运行的情况下,没有办法进行扩缩容
主要部署再对外集群:对外的业务会经常容易八年更,daemonset可以更好的,自动的发现服务配置变更
部署对外集群。
deployment:集中控制,可以使用少量的实例来运行处理整个集群的流量
缺点:deployment的负载均衡不会均分到每个节点
手动更新,无法感知容器内部配置变化,主要部署在对内集群
部署对内集群:对内相对稳定,更新和变化也比较少。适合deployment
traffic-tye:internal 对内服务
traffic-type:external 对外服务
nginx-ingress:相对较慢
工作原理都一样,都是七层代理,都可以动态的更新配置,都可以自动发现服务
traefik-ingress:自动更新重载更快,更方便
traefik的并发能力只有nginx-ingress的6成
ingress
nginx-ingress-controller用的时最多的
deployment+loadbalaner这个必须要共有云提供公网的地址
daemonset+hostnetwork+nodeselector:和节点服务器共享网络,一个节点部署一个controller pod. 既然使用宿主机的端口性能最好适合大并发
deployment+NodePort:这是最常见的也是最常用最简单的方法,但是性能不太好,因为多了一层nat地址转发,不太适合大并发
另外就是traefik-controller
deamontset适合对外 可以自动更新容器配置 hsot 用的时节点的网络
deployment适合对内 无法自动更新配置 Nodeport
daomonset演示
daemonset的配置更新后的自动发现wget https://gitee.com/mirrors/traefik/raw/v1.7/examples/k8s/traefik-rbac.yaml wget https://gitee.com/mirrors/traefik/raw/v1.7/examples/k8s/traefik-ds.yaml wget https://gitee.com/mirrors/traefik/raw/v1.7/examples/k8s/ui.yaml
需要执行这三个文件
然后自己配置yaml文件
kubectl apply -f traefik-ingress2.yaml

接下来做域名映射
vim /etc/hosts
用域名加8080访问页面
 文章来源:https://www.toymoban.com/news/detail-804080.html
文章来源:https://www.toymoban.com/news/detail-804080.html
 文章来源地址https://www.toymoban.com/news/detail-804080.html
文章来源地址https://www.toymoban.com/news/detail-804080.html
到了这里,关于k8s之ingress的文章就介绍完了。如果您还想了解更多内容,请在右上角搜索TOY模板网以前的文章或继续浏览下面的相关文章,希望大家以后多多支持TOY模板网!