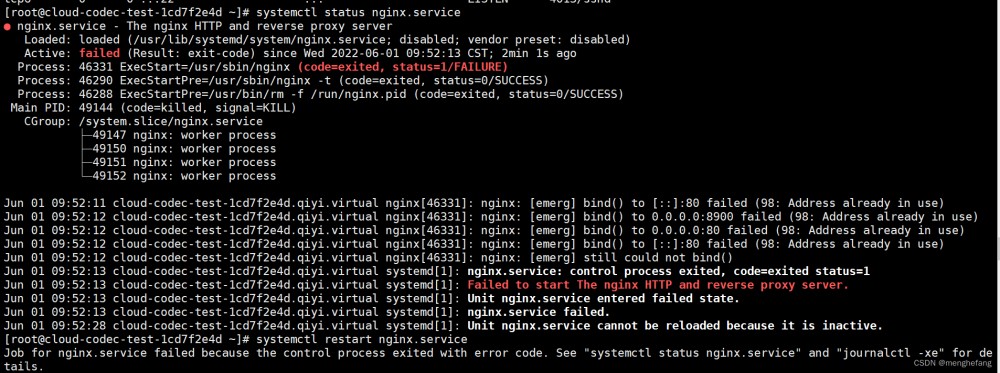
server { listen 443 ssl; server_name www.XXX.com; proxy_read_timeout 3600s; # 设置读取超时时间 ssl_certificate C:/xxxx.pem; ssl_certificate_key C:/xxxx.key; ssl_session_cache shared:SSL:1m; ssl_session_timeout 5m; #ssl_ciphers HIGH:!aNULL:!MD5; #ssl_prefer_server_ciphers on; client_max_body_size 5m; client_body_buffer_size 5m; location / { #保留代理之前的host 包含客户端真实的域名和端口号 proxy_set_header Host $host; #保留代理之前的真实客户端ip proxy_set_header X-Real-IP $remote_addr; #这个Header和X-Real-IP类似,但它在多级代理时会包含真实客户端及中间每个代理服务器的IP proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for; #表示客户端真实的协议(http还是https) proxy_set_header X-Forwarded-Proto $scheme; #指定修改被代理服务器返回的响应头中的location头域跟refresh头域数值 #如果使用"default"参数,将根据location和proxy_pass参数的设置来决定。 #proxy_redirect [ default|off|redirect replacement ]; #proxy_redirect off; proxy_pass http://xxxxx; } # intermediate configuration ssl_protocols TLSv1.2 TLSv1.3; ssl_ciphers ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:DHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES256-GCM-SHA384:DHE-RSA-CHACHA20-POLY1305; ssl_prefer_server_ciphers off; }
关键配置(更新配置时,请注意 原因的配置项是否有配置这3个配置 不能有重复配置项)
# intermediate configuration ssl_protocols TLSv1.2 TLSv1.3; ssl_ciphers ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:DHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES256-GCM-SHA384:DHE-RSA-CHACHA20-POLY1305; ssl_prefer_server_ciphers off;
测试工具(支持自定义端口的测试好难找)
https://geekflare.com/tools/tls-test
https://myssl.com/文章来源:https://www.toymoban.com/news/detail-805260.html
转自 https://www.cnblogs.com/chenpan/p/17760230.html文章来源地址https://www.toymoban.com/news/detail-805260.html
到了这里,关于nginx 关闭TLS 1.0 TLS 1.1的文章就介绍完了。如果您还想了解更多内容,请在右上角搜索TOY模板网以前的文章或继续浏览下面的相关文章,希望大家以后多多支持TOY模板网!


![宝塔面板迁移错误:nginx: [emerg] unknown “connection_upgrade“ variablenginx: configuration file /www/server/](https://imgs.yssmx.com/Uploads/2024/01/812790-1.png)